- Details
- Category: Security News
IBM is deploying its Watson supercomputer to help organizations answer this essential question: In the face of nonstop security events, potential intrusions, suspected breaches and critical patches, what's the next, best action that an organization's security analyst should take?
"It's all very well understanding you've got a problem; it's then, well, how do I triage, how do I take an informed decision about that, and how do I then remediate? So what are the processes that I go through," says Peter Jopling, an executive security adviser with IBM Security who's based in the United Kingdom.
While deploying Watson to tackle information security challenges is still in its early stages, Jopling says that going forward, organizations will clearly need more help, not less. "The challenge with pretty much every organization I talk to is that security isn't their core business. They don't want to stand up a large security operations center with lots of people and lots of process around that," he says.
In this interview with Information Security Media Group at the Infosec Europe conference in London, Jopling also discusses:
Organizations' need for a security intelligence framework. Challenges related to assimilating security-related data and triaging the security team's response. How IBM anticipates Watson will provide security-related upsides.Jopling is the deputy program director of IBM Security's tiger team. He's previously served as the chief technology officer and software security executive for IBM's U.K. business unit; identity, risk and governance strategy manager for IBM Tivoli in the United Kingdom and Ireland; and as a security and mainframe account manager for Platinum Technology, prior to its acquisition by Computer Associates.
- Details
- Category: Security News
In this edition of the ISMG Security Report, our editors analyze Symantec's pending purchase of Blue Coat; vulnerabilities in mobile banking apps; retailers' objections to a national data breach notification bill; and the relaunch of the troubled Internal Revenue Service Get Transcript tool.
You'll hear in this report (click on player beneath image to listen):
DataBreachToday Executive Editor Mathew J. Schwartz describe why Symantec hopes its $4.65 billion purchase of Blue Coat will revitalize the anti-virus software maker; ISMG Associate Editor Radhika Nallayam report that placing customer convenience before security explains why 85 percent of the mobile banking apps in the Asia-Pacific region fail basic security checks; BankInfoSecurity Executive Editor Tracy Kitten describe why retailers are battling against breach notification legislation before the U.S. Congress that would require them to follow some of the same rules imposed on banks; and How the Internal Revenue Service is employing two-factor authentication to help secure its newly relaunched Get Transcript service, which it shuttered last August after a breach that exposed the personal information of 724,000 taxpayer accounts.The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Please check out our June 7 and June 10 reports, which respectively examine the backstory behind SWIFT-related thefts and concerns expressed by security practitioners at the Infosecurity Europe conference in London earlier this month. The next ISMG Security Report will be posted Friday, June 17.
Theme music for the ISMG Security Report is by Ithaca Audio under a Creative Commons license.
- Details
- Category: Security News

Most U.S. consumers never could have anticipated all of the changes we've experienced in payments over the last 10 years, including the emergence of e-commerce and mobile payments and the switch to chip cards.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
Ten years ago, payment card security was little more than an afterthought, Troy Leach, chief technology officer of the Payment Card Industry Security Standards Council, points out. The focus was on merchant loyalty programs and customer relationship management, which required merchants to know more about their customers by storing their shopping histories.
"In looking at the 2005 and 2006 timeframe, we were seeing a lot of breaches [as a result of] storing cardholder data unnecessarily," Leach says. "There were some very common challenges - some of those challenges we still see today, like default passwords or just weak network security or not separating sensitive information from the rest of a company's assets."
Of course we know today that storing cardholder data is a bad idea. But storing such data was common back in the days before PCI Data Security Standard compliance.
"The DSS was really created to have organizations re-evaluate how they were actually using and managing cardholder information," Leach says. "If we reflect back to that time, people were not aware of the risks associated with storing cardholder information or using it for loyalty programs or customer management programs. So much of the DSS effort in the beginning was actually to educate about the removal of unnecessary storage of information that was associated with many breaches at the time, and also just to raise awareness about how you could have a business strategy to eliminate processes and minimize the risk to every stakeholder in the payment ecosystem."
PCI Anniversary
This September marks the 10th anniversary of the PCI Security Standards Council - a group established by the major card brands to manage payment card data security through PCI-DSS.
Although PCI-DSS was introduced in December 2004 as the first unified payments security standard to be approved and required by all the major card brands, it wasn't until the PCI Council's inception in 2006 that widespread adoption of and compliance with the standard began to take root.
My career covering payments and financial security closely aligns with the birth of the PCI-DSS. In October 2004, I took a job with an online publication called ATMmarketplace, where I developed relationships with some of the same sources I still rely on today.
PCI-DSS has been criticized over the years for its rigidity and failure to evolve quickly enough to address emerging risks. In a February 2011 interview, online security expert Josh Corman predicted PCI-DSS wouldn't stand the test of time.
In the days to come, we'll present a series of interviews and articles about the impact PCI has had on payments security and how payments security in the U.S. and throughout the world has changed since 2006. We'll also examine an important question: Will the PCI-DSS remain a viable standard 10 years from now?
Troy Leach of the PCI Security Standards Council on the future viability of the PCI-DSS.
Look for my audio interviews with Leach, who's been on the PCI Council almost from day one, and Jeremy King, international director of the council, who helped lead efforts to spread awareness and adoption of the PCI-DSS to markets outside the U.S.
I'll also be conducting interviews with a wide variety of other payments experts to get their takes on the impact of PCI-DSS, and whether it will continue to be viable. And my colleagues at ISMG will examine the impact of PCI around the globe.
I'd like to know your thoughts about the future viability of the PCI-DSS. Post your comments below.
- Details
- Category: Security News
 All in the Microsoft family (from left): LinkedIn CEO Jeff Weiner, Microsoft CEO Satya Nadella and LinkedIn Executive Chairman Reid Hoffman. (Source: Microsoft)
All in the Microsoft family (from left): LinkedIn CEO Jeff Weiner, Microsoft CEO Satya Nadella and LinkedIn Executive Chairman Reid Hoffman. (Source: Microsoft)My initial reaction to Microsoft's announcement that it plans to buy LinkedIn for $26.2 billion in cash: I guess that massive 2012 data breach didn't hobble the company's prospects (see LinkedIn's Password Fail).
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
That's relevant because one oft-repeated breach bromide - regularly trotted out via vendors' surveys of customers' self-reported perceptions - is that consumers will defect from breached businesses. The warning is meant to be a cautionary note to all organizations: Get your security house in order, or else you might lose customers.
The sentiment is worthwhile. As a consumer, I want the organizations that I choose to do business with - or in the case of LinkedIn, the service I choose to use in exchange for however the site is monetizing my personal information and professional connections - to protect my information.
But it's clear that when businesses get breached, consumers might cry foul, although it's unlikely that they're going to go elsewhere.
Kansas Heart Hospital suffered a ransomware infection last month, for example, but chances are that if you're living in the Wichita area and planned to get a heart procedure done there prior to the attack, you're not going to let a little malware get in the way.
Switching bank accounts, too, is such a pain that few users actually do so, even when their bank suffers a breach.
Target Users Switched to Cash
On the retail and restaurant front, big-named breached businesses include P.F. Chang's, Wendy's as well as Target. In the wake of Target's 2013 mega-breach and reports of stolen payment card data, the reaction from many consumers was that they would continue to shop at Target, but pay cash. Likewise, even though Zappos suffered a massive 2012 breach that revealed substandard password practices, has a single person ever decided, based on that breach, to not buy a pair of shoes from the online retailer?
Meanwhile, TalkTalk suffered three separate breaches in 2015, but CEO Dido Harding remains at the helm, thus suggesting that however bad the hack attacks were, despite the loss of 100,000 customers following the October breach, and the company's stock price since then losing a third of its value, the board of directors still has faith in Harding.
Here's how @TalkTalk stock has performed on London exchange before/after Oct. 2015 breach. (Source: Google Finance) pic.twitter.com/FN05FLDvsL
In fact, the only businesses that seem to take an irreversible hit from breaches are the ones that get driven out of business, such as DigiNotar, a certificate authority that issued bad certificates in 2011; Code Spaces, which had its cloud-based data overwritten by attackers in 2014; or any number of bitcoin exchanges. But none of those were brand names or failed due to customer defections.
After 2012 Breach, LinkedIn Thrives
That's a relevant discussion when it comes to LinkedIn. While its data breach came to light four years ago, it's been in the limelight in recent weeks thanks to the paid breach-notification service LeakedSource getting its hands on 165 million LinkedIn credentials. LinkedIn was always mum about the 2012 breach, and never commented on whether it involved just the credentials related to 6.5 million password hashes that got posted to an underground password forum by a hacker who was seeking help in cracking them.
Looking back, it's likely that LinkedIn, which didn't have a CISO at the time - but quickly got one - did not know that hackers had stolen what appears to be almost every LinkedIn user's credentials. But whatever LinkedIn did - or did not - know, it chose to only reset the credentials associated with 6.5 million accounts. Four years later, of course, that looks to have been a really bad move.
Unfortunately, LinkedIn wasn't an outlier, exactly, as a number of other big-name firms had also been hacked and their poorly secured user credentials stolen (see 'Historical Mega Breaches' Continue: Tumblr Hacked).
LinkedIn + Microsoft = ?
Back to the LinkedIn acquisition. Microsoft CEO Satya Nadella says he expects the deal to close later this year, and that the combined companies "can accelerate the growth of LinkedIn, as well as Microsoft Office 365 and Dynamics as we seek to empower every person and organization on the planet."
Reading between the empowerment lines, the deal appears to be an attempt to make Microsoft's online collaboration environment "stickier," although Sean Sullivan, a security adviser at Finnish security firm F-Secure, warns that there can be related downsides. "In the short run, I'd raise the concern that tighter integration between LinkedIn, Skype and Exchange/OneDrive could open up new vectors for business email fraud," he tells me, highlighting the potential for "CFO impersonation via Skype for Business, rather than via email."
One recent banking malware campaign, for example, used LinkedIn information to personalize emails sent to phishing targets, according to information security firm Fox-IT. Hence, in the post-Microsoft LinkedIn regime, "hopefully it all ties together well in a way that makes it easy to tell outsiders from insiders," he says.
A big impetus for this deal also appears to be to give a boost to the Microsoft Dynamics software, which by many estimates plays fourth fiddle - after salesforce.com, SAP and Oracle - in the customer relationship management software market.
In fact, given the price being offered by Microsoft - 50 percent more than the company's share price was worth - I'd bet that one of these CRM competitors was sniffing around LinkedIn too.
From a security standpoint, that's not a bad turn for a company that managed to lose virtually all of its users' access credentials just four years ago.
- Details
- Category: Security News
Anti-Malware , Endpoint Security , Technology
Now Ransomware Locks Smart TVs Android Malware Demands iTunes Gift Cards as Ransom Payment
First the hackers came for our credit cards. Now they're taking control of our TVs.
See Also: Unlocking Software Innovation with Secure Data as a Service
Security researchers have spotted an updated strain of ransomware that's designed to infect and lock Android devices, including mobile phones, tablets as well as smart TVs (see Why 'Smart' Devices May Not Be Secure).
The malware is known as FLocker - short for "frantic locker" - and first appeared in May 2015, Trend Micro security researcher Echo Duan says in a blog post. "The latest variant of FLocker is a police Trojan that pretends to be 'U.S. Cyber Police' or another law enforcement agency, and it accuses potential victims of crimes they didn't commit. It then demands $200 worth of iTunes gift cards."
In other words, attackers are robbing from Android to pay for Apple, or at least the ability to launder stolen funds by selling the iTunes gift cards, for example via eBay.
To be clear, end users have to be tricked into downloading and executing the ransomware, as well as allowing it to have admin-level rights. But as previous malware infections have demonstrated, disguising attack code - for example by running spam campaigns with data pulled from LinkedIn profiles that include attached malware, to claiming that software attached to a phishing message is a TV firmware update - will trick at least some recipients (see Malware, Ransomware Thrive Despite Criminal Prosecutions).
Once installed, the malware doesn't unleash havoc indiscriminately. "When launched for the first time, FLocker checks whether the device is located in the following Eastern European counties: Kazakhstan, Azerbaijan, Bulgaria, Georgia, Hungary, Ukraine, Russia, Armenia and Belarus," Duan says. "If the device detects that it is located in any of these locations, it deactivates itself."
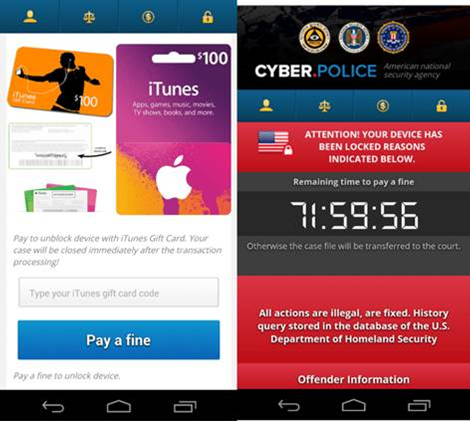 FLocker - Android malware's ransom page. (Source: Trend Micro)
FLocker - Android malware's ransom page. (Source: Trend Micro)
From Russia, With Love?
The malware's block zone offers a big clue, of course, to the origins of its developer (see Russian Cybercrime Rule No. 1: Don't Hack Russians).
Thankfully, variants of the malware seen to date cannot automatically execute, Trend Micro says. "If FLocker reaches a compatible target, it runs its routine 30 minutes after infecting the unit. After 30 minutes, it starts the background service which requests device admin privileges immediately," Duan says, in what appears to be an attempt to bypass any security tools that may be installed on the device.
Security experts have long recommended wiping and restoring - from a recent, known-good backup - any Android mobile device that suffers a malware or ransomware infection.
Where televisions are concerned, however, such an approach isn't feasible. Should an Android TV become infected with FLocker, "we suggest [users] contact the device vendor for solution at first," Duan says. Another option, detailed in full on Trend Micro's blog, is to put the device into debugging mode and launch an ADB shell to run a command that will kill the ransomware process, and then deactivate the lock screen, revoke the app's admin-level privileges and delete the application. Obviously, less advanced users might have difficulty executing that maneuver.
I Spy Internet-Connected Microphones
This ransomware attack isn't the first time that our televisions have potentially been turned against us. Earlier this year, for example, the privacy policy for Samsung's Smart TVs came to light, revealing that it allows anything said within range of the television's microphone to be transmitted to unnamed third parties (see Slouching Toward 1984). Samsung quickly attempted damage control by claiming that the information would never be used for marketing purposes, and noting that a microphone icon appears on screen whenever it's activated.
Of course, as everyone who puts a Band-Aid over their webcam knows, hackers can remotely activate such features to capture live audio or video while disabling any visual notifications that they've been remotely activated.
My webcam band-aid made it to the Sydney Morning Herald: http://t.co/ysWwzaihJp
Attack of the NSA-Pwned TVs
TVs aren't the only digital devices likely to be so targeted. Richard Ledgett, the U.S. National Security Agency's deputy director, last week said at a conference on military technology that his agency is looking into both medical devices and Internet of Things devices as potential signals intelligence targets, meaning sources that can be monitored to generate useful data.
Medical devices could be "a niche kind of thing ... a tool in the toolbox," Ledgett said, adding that there were easier ways to keep track of suspected terrorists or foreign intelligence agents, the Intercept reports.
And in response to a question about whether the Internet of Things is "a security nightmare or a signals intelligence bonanza," he said that it's "both."
"As my job is to penetrate other people's networks, complexity is my friend," Ledgett said. "The first time you update the software, you introduce vulnerabilities, or variables rather. It's a good place to be, [from] a penetration point of view."
More Articles …
Page 3445 of 3546
