- Details
- Category: Security News
Anti-Fraud , Anti-Malware , Fraud
But Post-Bangladesh Bank Hack Plans Would Not Require Compliance, CEO Says Gottfried Leibbrandt, CEO of SWIFT. (Source: SWIFT)
Gottfried Leibbrandt, CEO of SWIFT. (Source: SWIFT)After blaming a recent spate of bank robberies on banks' poor information security practices, SWIFT has somewhat changed its tune, saying that it wants to help financial firms spot related fraud and better share information about unfolding threats.
See Also: Vulnerability Management with Analytics and Intelligence
Gottfried Leibbrandt, SWIFT's CEO, announced the moves on May 24, together with a promise to better secure the SWIFT interbank messaging system.
"Cyber concerns are not new to us at SWIFT. Indeed, ever since I took on this job, cyber risk has been the main thing to keep me awake at night," Leibbrandt said in a keynote speech at the European Financial Services Conference in Brussels. "We work very hard at improving the cybersecurity of our network; every day we wake up and go to sleep thinking about, and protecting against that threat. It is hard work and never done."
SWIFT - short for the Society for Worldwide Interbank Financial Telecommunication - is a cooperative owned by 3,000 banks, founded in 1973, that bills itself as "the world's leading provider of secure financial messaging services." It's now used by 11,000 banks globally to process 25 million communications daily that collectively account for billions of dollars' worth of transfers.
Naturally, the SWIFT messaging system has long been a target of attackers, since a successful attack - utilizing real-looking but fraudulent messages - would allow thieves to transfer money out of victims' accounts, directly into attacker-controlled accounts. Investigators say that's just how attackers managed to transfer millions of dollars out of Bangladesh Bank's account at the Federal Reserve Bank of New York (see Bangladesh Bank Heist: Lessons Learned).
Leibbrandt predicted that the theft of $81 million from Bangladesh Bank "will prove to be a watershed event for the banking industry; there will be a before and an after Bangladesh." He also warned that more such attacks have been launched, and would surely be launched in the future.
Since that February attack, which came to light in March, more attacks - and attack attempts - have already been revealed, including the theft of $12.2 million from Banco del Austro, or BDA, in Ecuador, in early 2015, via fraudulent SWIFT messages. Earlier this month, Vietnam-based Tien Phong Bank said that it had successfully blocked a similar plot to transfer $1.36 million out of its accounts via fraudulent SWIFT messages, at the end of 2015.
Investigators say recent strikes have involved attackers successfully infecting banks' systems with malware and injecting fake money transfer requests into the SWIFT network. Attackers have been hiding those transfers by substituting a Trojanized version of a PDF reader used by the banks to review related statements generated by their SWIFT software.
SWIFT has continued to maintain that its network, software and core messaging services have not been hacked. Leibbrandt repeated that assertion, and said that some banks must dramatically improve their information security practices (see SWIFT to Banks: Get Your Security Act Together).
Increasing Scrutiny of SWIFT
But in recent weeks, some security experts have been asking if SWIFT shouldn't be doing more to help users stay secure, for example by creating security regulations - modeled on the Payment Card Industry's Data Security Standard - with which users would have to comply.
Officials in some countries have also been asking SWIFT how it plans to help customers better secure themselves. Notably, the Bank of England in April asked all British banks to detail how they'd responded to the Bangladesh Bank hack (see Banks, Regulators React to SWIFT Hack).
On May 23, Rep. Carolyn B. Maloney (D-NY) wrote to Fed Chair Janet Yellen, Comptroller of the Currency Thomas Curry and Federal Deposit Insurance Corp. Chairman Martin Gruenberg, asking them if they planned to follow the Bank of England's lead and order all U.S. banks to conduct a full cybersecurity review.
Maloney, who represents part of Manhattan - where many U.S. banks are headquartered - also asked officials what steps their agencies have taken or plan to take "to ensure that all U.S. banks have adequate security measures in place to protect against cyber attacks that involve stolen SWIFT credentials."
Her move followed Sen. Tom Carper (D-Del.), the ranking Democrat on the Senate Homeland Security and Governmental Affairs Committee, on May 19 writing to the New York Fed and SWIFT to request details about how they're responding to hack attacks.
SWIFT: "Not a Policeman"
While saying that SWIFT will do more to help, Leibbrandt said in his Brussels speech that the cooperative will not require banks to comply with its recommendations or any related audits. "SWIFT is not all-powerful, we are not a regulator, and we are not a policeman; success here depends on all the stakeholders in and around the industry," he said. "The security of our network remains our key priority; the security of their own environments has to remain - and, for some, become - banks' priority."
Later this week, meanwhile, Leibbrandt promised that later SWIFT will debut a "five-part customer security program" that features:
International information sharing "in a confidential way that uses the data while protecting the identity of the institution and customers." Requiring customers to use strong security tools and practices "to better protect their local environments." Better security guidance for customers, including related frameworks for auditing SWIFT-related security. A promise to try and help banks better analyze "payment pattern controls to identify suspicious behavior." Certification requirements for third-party providers.Call for Cooperation
Leibbrandt says more details on the plan will be forthcoming. But he also urged banks to help each other to better help themselves, starting with sharing information about related attacks. For example, SWIFT says it only learned of the $12 million heist from BDA this month, after it was revealed in media reports.
"Information sharing needs to get better, much better," he said. "It is critical that the global financial community works together to bolster our mutual security. ... We must work even harder at our collective defensive efforts."
- Details
- Category: Security News
Compliance , Cybersecurity , Info Sharing
ISF Director Says More Collaboration, Less Regulation NeededCyberattacks have gained regulatory attention worldwide. But the world doesn't need more regulation to address new threats, says Steve Durbin of the Information Security Forum. Instead, government must work more closely with the private sector.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
Durbin, managing director of the ISF, says government and the private sector must evaluate how to address cyber threats from an approach that doesn't just focus just on regulatory compliance, but also on the notion of business resilience.
"I'm a fan of government providing broad-based frameworks," Durbin says in this video interview conducted at Information Security Media Group's recent Washington Fraud and Breach Prevention Summit. "I think we do need regulation, of course. We always need legislation in this [cybersecurity] area. But government for me needs to do a better job of working collaboratively with business, with the private sector, to understand some of the implications of what they're doing."
As an example of how government decisions can adversely business, Durbin points to the European Court of Justice's declaration in October 2015 that the European Commission's safe harbor provisions for breach disclosure are invalid.
"Safe harbor was taken away, almost overnight for a lot of businesses," he says. "From a business perspective, it went [away] overnight. That left a gaping hole. We shouldn't have those types of situations."
In this interview, Durbin also discusses:
Why the NIST framework works as a pragmatic approach; Budgetary constraints plaguing cybersecurity investments; and Why organizations struggle to find qualified cybersecurity professionals.At the Information Security Forum, Durbin's main areas of focus include the emerging security threat landscape, cybersecurity, mobile security, the cloud and social media across both the corporate and personal environments. Previously, he was a senior vice president at the consultancy Gartner.
- Details
- Category: Security News
Identity and access management should empower businesses, satisfying customers and other stakeholders who need secure access to an enterprise's data and systems, says Jeremy Grant, former leader at the federal government's National Strategy for Trusted Identities in Cyberspace.
Too often, though, businesses, governments and other enterprises create hard feelings when customers and stakeholders struggle to securely access systems and data, says Grant, who now serves as managing director at the security advisory firm The Chertoff Group.
"One of the worst things you can do ... is to ask somebody to have to create a username and password in order to check out; nobody really likes doing that," Grant says in an interview with Information Security Media Group. "In fact, some would say that amounts to abusing your customer."
In the interview (click on player below photo to listen), Grant:
Describes what many organizations do wrong in implementing ID and access management programs; Explains how encryption and authentication go hand-in-hand; and Encourages organizations to analyze their approach to ID and access management to identify ways to improve it.Grant - along with Liz Votaw, senior vice president for authentication strategy at Bank of America - presented a session titled "Identity as the Great Enabler: Improving Security, Privacy and Customer Experiences" at ISMG's recent Washington Security and Breach Prevention Summit
As a managing director at The Chertoff Group, Grant advises clients on business, technical and policy issues concerning identity, privacy and cybersecurity. Earlier, Grant served for more than four years as leader of NSTIC, the public-private initiative housed at the National Institute of Standards and Technology, which aims to create a vibrant identity ecosystem where individuals and organizations can securely conduct online transactions (see As He Departs NSTIC, Jeremy Grant Sizes Up Progress).
- Details
- Category: Security News
Information Security Media Group is premiering the ISMG Security Report, a concise, on-demand audio report in which ISMG editors and other experts analyze the latest IT security news.
The ISMG Security Report, hosted by Executive Editor Eric Chabrow, will be posted on this and other ISMG news websites on Tuesdays and Fridays, with each episode running about 10 minutes.
Our debut episode features:
Look for our next report, which will be posted on Friday, May 27.
ISMG Security Report's theme music is by Ithaca Audio.
- Details
- Category: Security News
Breach Notification , Breach Response , Data Breach
LinkedIn's Password Fail No Site-Wide Password Reset Followed 2012 Breach
"In an abundance of caution, we are requiring all users to change their passwords."
See Also: Unlocking Software Innovation with Secure Data as a Service
After a data breach, many organizations communicate words to that effect to their customers. It's a smart move, since many breaches turn out to be much worse than initially suspected, as organizations find after launching a digital forensic investigation.
But in 2012, after 6.5 million LinkedIn users' password hashes appeared on a password-cracking forum, the social network didn't force all users to reset their passwords. That choice is now coming back to haunt LinkedIn, after an alleged cache of 167 million accounts appeared for sale on a dark web forum. Paid breach notification site Leaked Source says it was able to purchase the data for just 5 bitcoins, or about $2,200 (see LinkedIn Breach: Worse Than Advertised).
Rather belatedly - horse, barn, exit - LinkedIn says that it has locked the accounts of all users who haven't changed their passwords since 2012, requiring them to pick a new password.
When the LinkedIn breach came to light four years ago, LinkedIn - which didn't have a CISO - declined to tell me how many users might have been affected by the breach or breaches that obtained the credentials. But LinkedIn did at least lock some accounts.
"At the time, our immediate response included a mandatory password reset for all accounts we believed were compromised as a result of the unauthorized disclosure," LinkedIn CISO Cory Scott, who joined the company in 2013, says in a blog post. "Additionally, we advised all members of LinkedIn to change their passwords as a matter of best practice."
Now, of course, the size of the data dump suggests that attackers may have obtained every last LinkedIn user's credentials. And since the credentials' release, some buyers have reportedly already been putting them to use, taking over high-profile accounts and potentially using reused credentials to access victims' accounts on other services. And who knows what the data was being used for since 2012. "To my knowledge the database was kept within a small group of Russians," a member of Leaked Source told Vice Motherboard.
Then LinkedIn's Stock Price Increased
LinkedIn has hardly been transparent about what it knew and when. But as of now, the answer appears to have been: "Very little." And in the absence of definitive information about the breach back in 2012, the right thing to do would have been to lock every account and force password resets.
From a business perspective, organizations might try to avoid issuing password-reset notices, worrying that their brand will take a hit, or users will defect, thus sending their stock price plummeting. In fact, the news about LinkedIn's breach appears to have had the opposite effect.
For starters, the company's stock price increased after news broke this month that the breach was worse than expected, although it's unclear why. One theory for that rise was that large numbers users visiting LinkedIn users caused a spike in the company's advertising revenues, says Jeremi Gosney, CEO of consultancy Stricture, which provides password-cracking software, hardware and services, says via Twitter. "Another theory is automated trading platforms were seeing LinkedIn in the news a lot, so it thought 'buy!'"
#leakedin update: after wasting much the day on Friday, over the weekend we reached 156,302,827 / 177,500,189 (88%) cracked #passwords16
Users Don't Pick Good Passwords
The leaked LinkedIn credentials have - once again - revealed that many users, left unchecked, pick "123456," "sunshine," "qwerty," "linked" and "princess" as their password. In fact, those were many of the choices LinkedIn users made in 2012, according to Leaked Source's analysis of hashed passwords that it cracked (see Why Are We So Stupid About Passwords?). And LinkedIn allowed users to select those poor passwords.
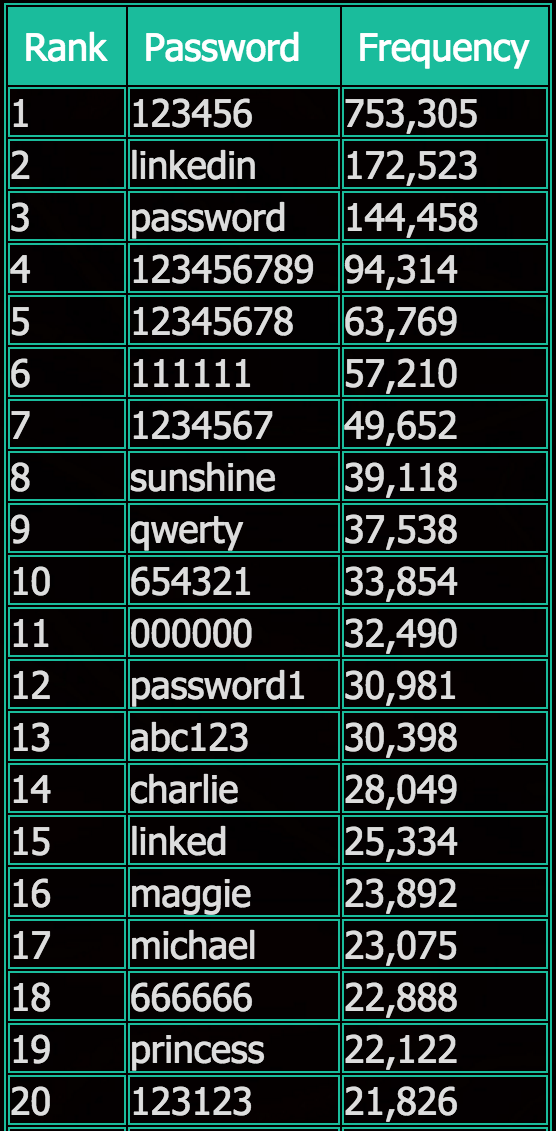 Top 20 password picks of 2012 LinkedIn users. (Source: Leaked Source)
Top 20 password picks of 2012 LinkedIn users. (Source: Leaked Source)Of course many security experts have long advised users to not reuse passwords across sites and to only pick long and strong passwords. And debate rages over whether users should reset their passwords on any site that ever suffers a breach - since it may portend worse - or else wait for related warnings from the breached organization.
But whatever passwords users might have picked, the LinkedIn breach is a reminder that unless passwords are securely stored, and hashed using secure techniques, it's child's play to crack them. LinkedIn, for example, was using the SHA1 cryptographic hash function, which security experts have long warned is not a secure way to hash passwords.
"People still make bad password choices," says Australian security expert Troy Hunt in a blog post.
"For me, what was more interesting about the whole thing was to witness both how the data was spreading and how comprehensively the weak cryptographic storage was being cracked," says Hunt, who runs the free "Have I Been Pwned?" breach-notification site - which sends alerts to email addresses registered with the site, when those email addresses show up in public data dumps.
At Least We Know About This One
Hunt says he's been fielding a lot of questions over why the stolen LinkedIn data took four years to come to light - and it's not clear why - or what attackers might been doing with it in the interim.
But he notes that the full extent of the LinkedIn breach taking four years to become known highlights how breaches may be much worse than they first appear. And it's also a reminder that "there's a lot of hacked companies we don't even know about," he says, and which may take years to come to light.
More Articles …
Page 3434 of 3546

