- Details
- Category: Security News
There are two elements of a ransomware attack - the infection and then the action that takes place on infected devices. And both elements are evolving, says Ben Johnson of Carbon Black. He shares insight on how to improve ransomware defenses.
Infections are on the rise - the daily headlines are testament to that, says Johnson, co-founder and Chief Security Strategist at Carbon Black. But what many security leaders don't see behind the scenes is how attackers are launching attacks that try to circumvent human defenses.
Social engineering is still effective, Johnson says, but taking the human out of the equation leads to even greater infection rates.
"If you can target a server or a remote desktop - someplace where there is no human - your chances as an attacker go up," Johnson says. "So, we're starting to see more targeting of servers and desktops through brute-forcing of credentials, or finding vulnerabilities in websites and then just automatically trying to encrypt their system."
When it comes to defending against these evolve attacks, organizations have two options: They can harden their systems to prevent infection, or - failing that - they can work to close open doors after they've been infected.
In an interview about defending against ransomware, Johnson discusses:
How ransomware and its targets have evolved; What to do to prevent infection, and how to respond when ransomware takes root; The surprising cultural challenges one often faces when fighting ransomware.Johnson is co-founder and chief security strategist for Carbon Black. In that role, he uses his experience as a cofounder and chief technology officer for Carbon Black, which merged with Bit9 in February 2014, to drive the company's message to customers, partners, the news media and industry analysts.
Johnson, who was directly responsible for the powerful functionality of the Carbon Black endpoint threat detection and response (ETDR) solution, has extensive experience building complex systems for environments where speed and reliability are paramount.
- Details
- Category: Security News
Big Data , Breach Notification , Cybersecurity
7 Scenes: Scottish Cybersecurity Conference Talking Ransomware, Botnets, Banking, Bitcoins and More The Egg at the Craiglockhart campus of Edinburgh Napier University in Scotland (Photo: Mathew Schwartz, ISMG)
The Egg at the Craiglockhart campus of Edinburgh Napier University in Scotland (Photo: Mathew Schwartz, ISMG)Fun cybersecurity fact about Scotland: Many of Britain's banks host their security operations centers in or around Edinburgh.
See Also: Rethinking Endpoint Security
So said Ian Rainsborough of digital forensic software maker Guidance Software, addressing the May 10 "International Conference on Big Data in Cyber Security," hosted by Edinburgh Napier University in Scotland. Throughout the day, a range of experts from academia, industry and the public sector detailed the latest trends in big data, policing, organizing information security teams, ransomware campaigns and more (see Police Reveal Botnet Herders' Disaster Recovery Secrets).
Here are seven visual highlights from the event:
1. Scottish Cybersecurity Networking
The "International Conference on Big Data in Cyber Security" took place at Edinburgh Napier University.
Organized by Bill Buchanan, a professor at the Edinburgh Napier School of Computing, the one-day event included presentations from a number of information security experts, ranging from law enforcement officials and forensic investigators to "big data" practitioners and CISOs, and drew attendees from across the United Kingdom, as well as a smattering from the European mainland. But as with every type of local cybersecurity event, many of the attendees hailed from Scotland, and told me they were there not just to learn, but also to network with peers.
2. Ransomware Hits Hairdresser
 Police Scotland's Eamonn Keane said small businesses in Scotland have been especially hard hit by ransomware attacks.
Police Scotland's Eamonn Keane said small businesses in Scotland have been especially hard hit by ransomware attacks.
Eamonn Keane, a detective inspector with Police Scotland's cybercrime unit, said it's been difficult for police to disrupt the massive rise in ransomware infections. "Every day, there's a new ransomware virus," he said. "I suppose we're going to have to apply a much more proactive engagement from a law enforcement perspective ... like we did with Gameover Zeus, like we did with the international scale of Blackshades and cybercrime as a service" (see How Do We Catch Cybercrime Kingpins?).
3. New Breach Notification Window: 72 Hours
 Hewlett Packard Enterprise's Tim Grieveson says that the EU's new data protection regulation will require breach notifications within 72 hours of discovery.
Hewlett Packard Enterprise's Tim Grieveson says that the EU's new data protection regulation will require breach notifications within 72 hours of discovery.
After more than four years of related negotiations, the EU's General Data Protection Regulation - the Soviet-sounding "GDPR" for short - passed on April 14. The GDPR includes a number of new provisions, for example giving regulators the ability to impose a fine of up to 4 percent of a company's worldwide annual revenue, as well as instituting mandatory data breach notifications for any organization that stores or handles personally identifiable information, once they discover that they've been breached.
"The scary thing is 72 hours - we have 72 hours to actually tell the authorities there has been a breach," said Tim Grieveson, Hewlett Packard Enterprise's chief cyber and security strategist for the Europe, the Middle East and Africa regions. Other experts have told me that the 72-hour figure isn't yet set in stone, but the current focus on three days suggests that whatever the breach-notification requirement ends up being, it won't stretch to weeks.
4. Building Security Playbooks
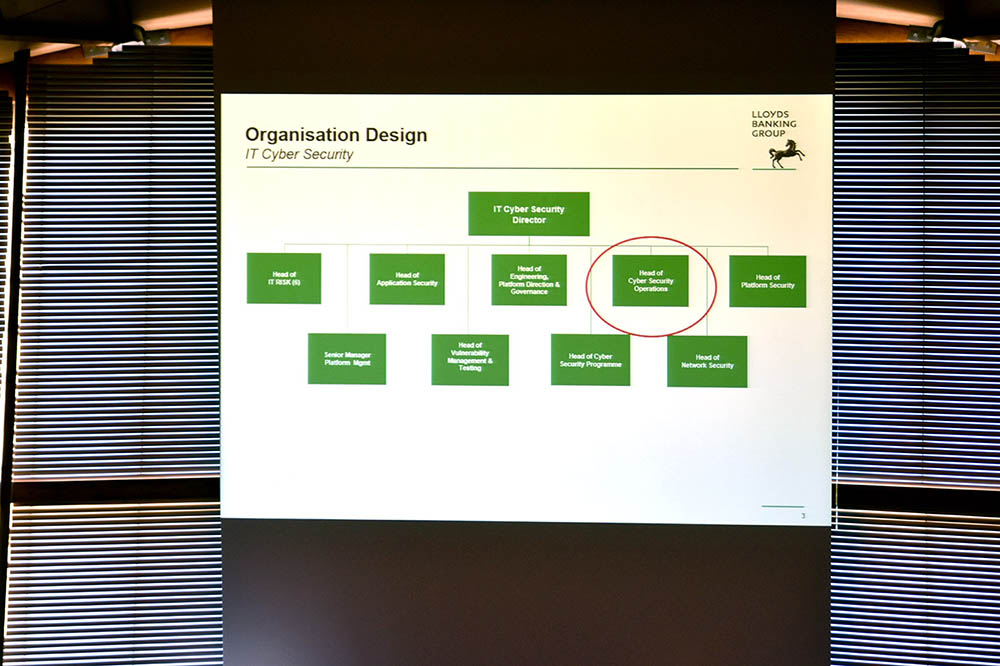 How Lloyds Banking Group organizes its security group.
How Lloyds Banking Group organizes its security group.
The day included multiple banking-related discussions. One was from Stephen Livingstone, who works with the security operations group at Lloyds Banking, which prioritizes developing security playbooks. "This is primarily because we're expecting to see high staff turnover in the next couple of years, and we want to ensure that knowledge transfer is something that happens often and easily," he said.
From a security standpoint, meanwhile, he said that one online challenge continues to be the "bring your own device" movement, because Lloyds currently has no legal resource to seize BYOD technology during the course of an internal investigation, although a fix is in the works. "We're addressing that with legal at the moment," Livingstone said.
5. Inside a Backup Botnet
 Forcepoint's Andy Settle delivers his presentation from inside the university building known as "The Egg."
Forcepoint's Andy Settle delivers his presentation from inside the university building known as "The Egg."
Andy Settle, head of special investigations for security firm Forcepoint - formerly known as Raytheon Websense - detailed a botnet campaign the company discovered, which it calls JAKU.
Settle said it's unclear who's behind the botnet, or what its purpose might be. But after launching a six-month investigation in October 2015, Forcepoint has found a number of interesting clues:
Victims: Korean language speakers are the most targeted (43 percent), followed by Japanese (30 percent) and English (13 percent). North Korea: "Tens, not hundreds, of victims" appear to travel to and from the North Korean capital of Pyongyang. Russia: Barring a few infections at a Russian ISP in Moscow, none of the botnet's victims were in Russia. Counterfeit Windows: 52 percent of victims appeared to be using a counterfeit Microsoft Windows operating system. Dwell time: The average victim PC is infected by JAKU malware for 93 days - up to a maximum of 348 days in one case - before the malware is somehow either blocked or eradicated.The takeaway from the above? "Don't jump to conclusions," Settle said. For example, the absence of Russian victims might be due to the malware selecting targets based on geography, language and timing, he said.
One possibility, Settle told me, is that whoever is behind the botnet has been keeping it in reserve for future campaigns, so that if a primary botnet gets disrupted by security researchers or law enforcement agencies, the JAKU botnet could become their primary botnet.
6. Big Data: Better Tools Required
 Steven Wilson, head of Europol's EC3
Steven Wilson, head of Europol's EC3
Steven Wilson, head of the European Cybercrime Center (EC3) at Europol - the EU's law enforcement agency - told the conference that better information sharing has been helping law enforcement agencies more quickly spot and disrupt criminal activity online.
Europol Director Rob Wainwright has been advancing the use of information-sharing platforms to connect more than 500 different law enforcement agencies from Europe - and beyond - and noted earlier this year that the amount of information being exchanged "has quadrupled in less than five years."
Because the volume of these incoming data feeds is both massive and increasing, and already reaches hundreds of terabytes per month, Wilson told the conference that Europol is increasingly looking to academia and the private sector to help it build the tools it needs to analyze all of that information. "The data feeds we're starting to get now are enormous, and to try and [tackle] them with conventional policing tactics is practically impossible," Wilson said.
7. Follow the Bitcoin Money
 Police Scotland's Eamonn Keane said criminals are increasingly operating online.
Police Scotland's Eamonn Keane said criminals are increasingly operating online.
Authorities already have some tools - developed by academics - that allow them to analyze and de-anonymize some bitcoin transactions, using, in part, data from the blockchain, which is the public ledger of all bitcoin transactions.
None of the law enforcement representatives present at the conference shared any new insights into exactly what those capabilities might be, although Police Scotland's Keane said the result of those capabilities has been well-documented, for example via the takedowns of both notorious Silk Road darknet marketplaces to date.
But criminals continue to be drawn by the relative ease and safety of operating online, Keane said, citing the following passage from a TED talk by Mikko Hypponen, chief research officer at Finnish security firm F-Secure: "It's more likely for any of us to become the victim of a crime online than here in the real world. And it's very obvious that this is only going to get worse. In the future, the majority of crime will be happening online."
Keane said: "We have a mandate to protect you in the real world; increasingly, it's moving into the online environment."
All photographs by Mathew J. Schwartz.
- Details
- Category: Security News
Breach Preparedness , Breach Response , Data Breach
Tom Kellermann on Why Security Leaders Need to Change Their StrategyToday's threat actors are more focused, funded and disruptive than ever. But the cybersecurity defense industry is not built to respond appropriately, says thought leader Tom Kellermann. What are security leaders overlooking?
See Also: How to Illuminate Data Risk to Avoid Financial Shocks
In his new role as CEO of Strategic Cyber Ventures, a cybersecurity technologies investment firm, Kellermann sees lots of new ideas. But too many of them are variations of the same theme: They are focused on developing specific tactical solutions that address only temporary problems that ultimately will morph. There is a systemic, industrywide lack of long-term vision, Kellermann says in this video interview with Information Security Media Group.
"The major cybersecurity vendors are laser-focused on maintaining their brand, their image and their cultural persona," Kellermann says. "With the exception of a few cases, that has become their albatross. Their lack of capacity to morph with the problem ... has been problematic."
In this interview at ISMG's recent Washington Fraud and Breach Prevention Summit, Kellermann discusses:
His new role at Strategic Cyber Ventures; What the top attackers are doing right; What cybersecurity defenders are doing wrong;Kellermann is a cyber intelligence expert, author and professor. He has worked in the highest levels of cybersecurity, having held a seat on the Commission on Cyber Security for the 44th President of the United States and served as an adviser to the International Cyber Security Protection Alliance. Before joining Strategic Cyber Ventures, he was chief cybersecurity officer at Trend Micro Inc., where he was responsible for analysis of emerging cybersecurity threats and relevant defensive technologies. Prior to Trend Micro, he served as vice president of Security for Core Security. He began his career as senior data risk management specialist for the World Bank's treasury security team, where he was responsible for cyber intelligence and security policy as he advised central banks around the world about their risk posture.
- Details
- Category: Security News
Anti-Malware , Anti-Money Laundering (AML) , Compliance
Millions Still Missing After Bangladesh Bank Heist
Banks and regulators have begun reviewing SWIFT-related information security practices following the online heist of $81 million from Bangladesh Bank. Authorities say much of that money is still missing.
See Also: The Inconvenient Truth About API Security
Bank of England, the U.K.'s central bank, ordered banks across the country to outline what steps they had taken to lock down their systems in the wake of the hack attack against Bangladesh Bank via the interbank SWIFT messaging system, Reuters reports, citing unnamed officials who weren't authorized to discuss the move.
Officials at the Bank of England didn't respond to a request for comment on that report.
SWIFT, which stands for the Society for Worldwide Interbank Financial Telecommunication, is a Brussels-based cooperative, maintains a messaging system used by 11,000 banks to help move money. Last week, SWIFT warned users that the February theft of $81 million from Bangladesh Bank's Federal Reserve of New York account - part of a plot to steal nearly $1 billion - was "part of a wider and highly adaptive campaign targeting banks."
Besides Bangladesh Bank, several other institutions have been targeted by the same group, SWIFT has warned. To date, only one of those banks has come forward: Vietnam's Tien Phong Commercial Joint Stock Bank, which says that it foiled a related attack attempt to steal more than $1 million in the fourth quarter of 2015.
Security researchers at U.K. defense contractor BAE Systems say it's not clear who's behind the attacks, although they have found that the malware used ties to some previous attacks, including the 2014 Sony Pictures Entertainment breach.
Authorities say most of the funds stolen in the Bangladesh Bank heist were laundered via casinos in the Philippines. In April, the Anti-Money Laundering Council in the Philippines filed a complaint with the country's Department of Justice against three senior executives at money-moving firm Philrem Service, based in Manila, which has been accused of converting and routing most of the $81 million stolen from the Bangladesh Bank's account at the New York Fed, the Philippines-based Inquirer reports.
SWIFT Urges Security Reviews
Security experts say all SWIFT-using banks must take breach prevention action as a result of the hack attacks.
"You're one of the biggest targets in the world right now," networking expert Doug Gourlay, corporate vice president at security startup Skyport Systems, tells Information Security Media Group. "This is the easiest bank robbery ever. It's the safest, and it pays out a heck of a lot better than walking in a regional branch with a gun."
In recent weeks, New York-based JPMorgan Chase has begun restricting many insiders' access to its SWIFT systems, The Wall Street Journal reports.
SWIFT has continued to defend the security of its software and network. It's also called on customers to "urgently review controls in their payments environments to all their messaging, payments and e-banking channels." (See SWIFT to Banks: Get Your Security Act Together)
Could SWIFT Do More?
But some security experts say that SWIFT could - and should - be doing more. "The system is widely perceived by banks as being secure, but these incidents have shaken their beliefs and are raising the same kinds of identification questions that have arisen with spoofed emails and other systems," Michael McGowan, anti-money-laundering and compliance technology leader at cybersecurity firm Stroz Friedberg, tells The Wall Street Journal.
Gourlay has called on SWIFT to update the "accurate but weak" security guidance that it currently offers to its users and spell out the detailed, prescriptive steps that it must take. And he's suggested that SWIFT could soon require its users to undergo periodic security audits to verify that they're using the messaging system in a secure manner (see Blocking Hack Attacks: SWIFT Must Do More).
In fact, some U.S. banks have been pushing SWIFT to discuss its response to the hack attacks - and if it responded quickly enough - as well as to help banks lock down their systems, Bloomberg News reports, citing unnamed officials inside a U.S. bank. They suggest that in the United States, BITS - the technology and policy division of the Financial Services Roundtable - could be tapped to organize related discussions.
Hackers Struck on a Friday
More details about the malware-enabled hack of Bangladesh Bank continue to come to light, including the fact that it was carried out on a Friday, which is a Muslim day of prayer.
"One of our bank official's computers, who actually is in the group who make the payment, who passes the payment instruction, his computer was hacked, and it was a Friday ... and the Bangladesh Bank is totally shut down on a Friday, because it's a Muslim day of prayer, and so it's all sealed, and so no one actually goes to the bank," Bangladesh Ambassador to the Philippines John Gomes told a Philippine Senate panel on May 19.
"So these payment instructions were made by the hacker; it was not anyone in the Philippines who was the hacker, nor was it anyone in Bangladesh who was the hacker," he added. "So this was hacked on a Friday, and then it went to the U.S. It was a Saturday, and then a Sunday, so they also had the weekend over there."
Bangladesh Ambassador to the Philippines John Gomes addresses the Philippine Senate.Gomes said Bangladesh Bank had neither found nor received any evidence suggesting that insiders were involved in the hack, as the FBI has reportedly suggested. Likewise, he says the bank hasn't seen any evidence to substantiate the possibility that hackers with ties to North Korea might have been involved.
$21 Million Still Unaccounted For
So far, $60 million of the money stolen in the Bangladesh Bank heist has been accounted for, though not necessarily recovered, Julia Bacay-Abad, executive director of the country's Anti-Money Laundering Council, told the Philippine Senate at the May 19 hearing, according to the Inquirer. But due to related legal challenges, it may take another six months before any of the recovered funds get restored to the bank, she added.
Bangladesh Ambassador Gomes told the committee that having to wait months more to see the money get returned "would be like a slap on my face."
- Details
- Category: Security News
Anti-Malware , Encryption , Technology
In a Surprise Twist, Cybercrime Developers Tell Victims: 'We Are Sorry!'
There's rarely good news in the world of cybercrime. But for victims of the TeslaCrypt ransomware, there's been a surprising twist, and one that provides relief.
See Also: Secure, Agile Mobile Banking: Keeping Pace with Last Best User Experience
On Wednesday, security vendor ESET said whomever is behind the TelsaCrypt ransomware - part of a noxious family of malware that encrypts most files on a computer and demands a ransom - suddenly released the master decryption key.
"One of ESET's analysts contacted the group anonymously using the official support channel offered to the ransomware victims ... and requested the universal master decryption key," ESET says in a blog post. "Surprisingly, they made it public."
With the key in hand, ESET was able to build and release a tool that will unlock computers affected by any of the four versions of TeslaCrypt that have been seen to date. Another tool for unlocking TeslaCrypt-infected PCs is TeslaDecoder, which has also been updated to make use of the now-released master decryption key, according to the Bleeping Computer forum, which reports that TeslaCrypt's developers appear to have been wrapping up their operations recently, and that many ransomware users have been switching to CryptXXX ransomware instead.
The TeslaCrypt decryption key was published on a hidden ".onion" website viewable through the Tor browser. It included a mystifying note in broken English: "Project closed. Wait for other people to make universal decrypt software. We are sorry!"
Whether the apology is sincere is impossible to tell. But ransomware - by all measures - has become one the greatest threats facing Internet users. Law enforcement and computer security companies have been struggling to counter it.
Pictured: TeslaCrypt lock screen.
Source: Cisco pic.twitter.com/CQ71Gtfmil
Ransomware Attacks Surge
Once ransomware infects a computer, it typically encrypts most file types and displays a message demanding a ransom, usually payable in the virtual currency bitcoin or another Internet-based payment system. In return for the ransom, cybercriminals promise to share a decryption key that will unlock all of the files.
Although ransomware has been around for more than decade, it has proliferated over the past couple of years. Consumers often see an average ransom demand of a few hundred dollars (see Please Don't Pay Ransoms, FBI Urges).
Those running the schemes have increasingly diversified their targets, going after governments, schools and hospitals in hopes of higher payments.
"Ransomware attacks are not only proliferating, they're becoming more sophisticated," the FBI warned on April 29 (see FBI Alert: $18 Million in Ransomware Losses). "Several years ago, ransomware was normally delivered through spam emails, but because email systems got better at filtering out spam, cybercriminals turned to spear phishing emails targeting specific individuals."
Ransomware Defenses
One defense is to not fall prey to targeted attacks through email and to avoid opening malicious documents or links. Security software can often spot and block attacks, but such applications are far from foolproof (see Ransomware: 7 Defensive Strategies).
A sure-fire way to recover from ransomware is to ensure that files are backed up and that the backup is not connected to the same network as an infected computer. But some organizations do not segregate their backups in such a way or even do timely ones.
TeslaCrypt was first seen early last year and appeared to be a variant of CryptoLocker, another type of ransomware designed to forcibly encrypt PCs. In mid-2014, CryptoLocker disappeared after the U.S. Department of Justice, working with law enforcement agencies in Australia, Germany, France, Japan, Ukraine and the United Kingdom, shut down the Gameover Zeus botnet.
TeslaCrypt initially focused on targeting gamers. It was engineered to encrypt files containing saved game sessions and activation keys for the Steam gaming marketplace, according to a Cisco blog post. The ransom demand was typically $500.
But in April 2015, Cisco's Talos unit created a tool that could recover files encrypted by an early version of TeslaCrypt. That version used a weak encryption algorithm and stored the decryption keys on the victim's device.
The triumph, however, was only temporary, as subsequent versions of TeslaCrypt closed that hole. Other researchers have occasionally found coding errors or mistakes in other types of ransomware, but developers and the cybercrime gangs who increasingly rely on ransomware to generate illicit profits usually react quickly to code flaws and fix the malware, so as to not disrupt their revenue stream.
More Articles …
Page 3430 of 3546

