- Details
- Category: Security News
It's one thing to talk or even plan about "What happens if we are breached?" It's quite another to undertake a true breach exercise. What are the critical elements of such a drill? Author Regina Phelps shares advice from her new book.
The book, "Cyber Breach: What if your defenses fail? Designing an exercise to map a ready strategy," has just been published by Chandi Media. Phelps, a longtime emergency management and response expert and educator, says such breach exercises give organizations the necessary chance to test and refine their response plans.
"You can see what works, what doesn't and you can dramatically advance the thinking of everyone from executives down to the affected departments," Phelps says in an interview with Information Security Media Group. "I have never seen an exercise yield such incredible results, deeper understanding and thinking about possible solutions and issues as a well-crafted cyber breach exercise."
"Impact" is the key theme of Phelps' book and her exercises. "What we're looking at is the management of an event," she says. "What do you do, for example, in your company right now if you have no systems for days or weeks or, God forbid, months? When you open up any plan from a company, there is nothing that addresses that. They assume always that systems will be up in a reasonable amount of time."
And so the premise Phelps builds upon is: What if you lost your systems for a protracted period of time? How would you do your business, and how would you manage the reputational damage?
In this interview about her new book (see audio player below photo), Phelps discusses:
Her experience with clients who have been breached; The importance of meaningful breach exercises; Eight must-haves to ensure a successful exercise.Phelps, RN, BSN, MPA, CEM, is an internationally recognized expert in the field of emergency management and continuity planning. Since 1982, she has provided consultation and speaking services to clients in four continents. She is founder of Emergency Management & Safety Solutions, a consulting company specializing in emergency management, continuity planning and safety. Among the company's clients are McAfee, IMF, Microsoft, American Express, Northern Trust, VISA, Triton Container, Intuit, Stanford University, Caltech Institute, JPL, Merck, MasterCard and the World Bank. Phelps is working on a new book on crisis leadership.
- Details
- Category: Security News
Despite understanding the need for multifactor authentication, many financial institutions struggle with the complexity of implementing effective solutions.
"Let's talk about what this complexity looks like...The average MFA initiatives have been ongoing for six years. On average, four point solutions are deployed because no one solution secures all IT assets. Organizations incrementally adopt new, partial solutions as they become aware of new threats and as new systems are brought online." Chris Trytten, Director of Product Marketing at Crossmatch, says.
Historically, multifactor authentication systems required everything to be custom-built, Trytten, explains. Managing the growing number of systems and the ever-increasing number of employees, partners and customers - all from multiple access points - is difficult at best.
In an interview discussing the latest multifactor authentication trends, Trytten offers insights and strategies on:
The primary barriers preventing financial institutions from adopting multifactor authentication; The ways in which multifactor authentication helps deter cyberattacks; and How Crossmatch simplifies identity and access management for financial institutions.Trytten is Director of Product Marketing at Crossmatch. With over two decades of technical and managerial experience in systems and security in the financial and retail spaces, Trytten guides Crossmatch's product and and marketing teams to address the security needs of these industries. Prior to joining Crossmatch, Trytten worked at leading companies in Silicon Valley, including DigitalPersona, Interlink Networks, Siemens and Apple. He is also a recognized musician, having won the prestigious Villa Lobos International Guitar Competition in 1981.
- Details
- Category: Security News
Cybersecurity , Mobility , Risk Management
Presidential Candidates All But Ignore Cybersecurity Trump, Clinton, Sanders Fail to Spell Out Their Cyber Policies Presidential candidates Donald Trump, Hillary Clinton and Bernie Sanders
Presidential candidates Donald Trump, Hillary Clinton and Bernie SandersAmerica's cyber infrastructure is under constant attack, and damage to it could have significant economic and national security consequences.
See Also: The Inconvenient Truth About API Security
It's a threat that must be addressed at the highest levels of government, working in conjunction with the private sector. But the candidates for president of the United States don't have much to say about the cyberthreat. Search the keyword "cyber" on the campaign websites of Hillary Clinton, Bernie Sanders and Donald Trump, and the number of returns is miniscule. And except for one posting about securing the electric grid, none of the sites offers any substance or insight on cybersecurity strategies.
Most recent cybersecurity talk in the campaign has focused on Clinton's use of a private email server as secretary of state. Otherwise, except for a few mentions at candidates' debates last fall, cybersecurity has hardly surfaced as an issue.
Cybersecurity Doesn't Fit on Bumper Sticker
Candidates haven't raised cybersecurity as an issue because they haven't figured out how they can get any votes out of it. As former federal CIO Karen Evans says, "Cybersecurity doesn't fit on a bumper sticker."
Trump has criticized Clinton for the use of the private email server mainly in an attempt to question her judgment. But he's offered little proof that her actions caused damage to national security or were illegal.
In the wake of Apple's refusal to help the FBI crack open the iPhone used by one of the San Bernardino shooters, all three candidates weighed in. Here's what they had to say:
Donald Trump
Audio from MSNBC-sponsored town hall and a Trump rallyHillary Clinton
Audio from MSNBC/Telemundo-sponsored town hallBernie Sanders
Audio from MSNBC/Telemundo-sponsored town hallBut the candidates' views on using a backdoor to circumvent encryption or other safeguards on a mobile device used by a criminal or terrorist come up far short of addressing the core cybersecurity threats the nation faces.
Shuttering the Internet
At a December GOP presidential debate, Trump proposed shuttering parts of the internet to stop the so-called Islamic State from using it as an online recruiting tool. "I don't want them using our internet to take our young, impressionable youth and watching the media talking about how they're masterminds."
But terrorists using the internet to recruit gullible followers doesn't threaten America's cyber infrastructure. Besides, Trump didn't explain how he'd shutter part of the internet, saying he'd pass on the job to the "brilliant people from Silicon Valley" to figure it out.
What Trump proposes - even with the brilliance of Silicon Valley - cannot be done. The internet, after all, isn't a single entity; it's a network of networks that the United States does not control. If anything, Trump's explanation on shuttering the internet demonstrates his ignorance on how internet technology works.
Threat from China
A cyber-related area where the candidates seem to agree is the threat posed by China.
In a foreign policy address delivered April 27, Trump made passing references to cybersecurity. Speaking of President Obama, Trump said: "He has even allowed China to steal government secrets with cyberattacks and engage in industrial espionage against the United States and its companies."
Later in the speech, the presumptive GOP nominee said: "We need to think smarter about areas where our technological superiority gives us an edge. This includes 3-D printing, artificial intelligence and cyberwarfare." He did not provide any details on how he'd prevent China from stealing government and corporate secrets or how to be smarter in cyberwarfare.
In an article posted on his campaign website, Trump provided more details on the threat China poses but failed to explain the technical steps needed to be taken to mitigate that threat
That article noted: "China's ongoing theft of intellectual property may be the greatest transfer of wealth in history. This theft costs the U.S. over $300 billion and millions of jobs each year. China's government ignores this rampant cybercrime and, in other cases, actively encourages or even sponsors it - without any real consequences. China's cyber lawlessness threatens our prosperity, privacy and national security. We will enforce stronger protections against Chinese hackers and counterfeit goods and our responses to Chinese theft will be swift, robust and unequivocal."
Clinton, too, called on holding China accountable for its actions. But how she would do so, as well as other cybersecurity measures she'd take, remains unclear.
A posting on Clinton's website says: "Cyberattacks have profound consequences for our economy and our national security. Hillary will leverage the work of the public and private sectors - overcoming the mistrust that impedes cooperation today - to strengthen security and build resiliency for economy and infrastructure. Our country will outpace this rapidly changing threat, maintain strong protections against unwarranted government or corporate surveillance and ensure American companies are the most competitive in the world."
Safeguarding the Electric Grid
Clinton furnished more details on how to protect the electrical grid from a virtual attack. "Our electrical grid needs upgrading ... to address the growing threat of cyberattack," a campaign site fact sheet says. The former secretary of state and Democratic senator from New York proposes:
Creating a Presidential Threat Assessment and Response Team to improve coordination across federal agencies and strengthen collaboration with state and local officials and the electric power industry in assessing and addressing cybersecurity threats; Implementing a cybersecurity strategy that integrates and protects the expanded use of distributed energy resources and other clean energy technologies; and Providing new tools and resources to states, cities and rural communities to make the investments necessary to improve grid resilience to cyberattacks and extreme weather events.As for Sanders' stand on the issues, I couldn't find any cybersecurity-related postings on his campaign website.
Forecasting 45th President's Policies
At Information Security Media Group's upcoming Fraud and Breach Prevention Summit in the Washington area, a panel of experts will tackle the issue of how the next president should address cybersecurity.
Former federal CIO Evans will be joined by Ari Schwartz, former assistant to the president for cybersecurity; Steve Chabinsky, former FBI deputy director for cyber; and Larry Clinton, president of the Internet Security Alliance, in a session titled "How the Next President Will Deal with Obama's Cybersecurity Legacy." The panel will be held at 9 a.m. May 18.
Phyllis Schneck, speaking of government-private sector cooperation on cybersecurity, shortly after joining DHS in 2014.Later that day, at 12:05 p.m., Homeland Security Deputy Undersecretary Phyllis Schneck will deliver a keynote address, discussing how the government and private sector collaborate on sharing information to help mitigate cyberthreats.
Please join me at the summit, where I'll serve as a moderator. Here's information on how to sign up.
- Details
- Category: Security News

Commercial Bank of Ceylon, based in Colombo, Sri Lanka, has apparently been hacked, with its data posted online May 12 by the Bozkurtlar hacking group, which has also posted seven other data dumps from banks in the Middle East and Asia since April 26.
See Also: How to Mitigate Credential Theft by Securing Active Directory
The group, believed to have Turkish ties, released data from five South Asian banks on May 10. It also dumped data online from UAE-based InvestBank on May 7 and data from Qatar National Bank on April 26.
Commercial Bank of Ceylon did not immediately reply to Information Security Media Group's request for comment. But a researcher analyzing the data involved, who asked to remain anonymous, says that the hacked data appears to be genuine.
The files from the latest disclosure appear to contain the entire contents of the corporate website of the Commercial Bank of Ceylon, the researcher says, explaining that no customer data or payment card information was apparently exposed in the incident. The dump appears to have occurred in November of last year, which suggests the compromise took place before that, according to the researcher.
As with the other bank data compromises in the region in recent weeks, the attackers notified ISMG and others via Twitter about the file dump, which apparently was relatively quickly taken offline. Commercial Bank of Ceylon's web services at www.combank.net appear to have been taken offline briefly post the disclosure. The website was functional on May 13.
Data Dump Contents
The dump contains 158,276 files in 22,901 folders and is about 6.97 GB uncompressed. The compromised data contains annual reports, application forms, bank financial statements, .PHP files, web development backups and other files needed for the functioning of the bank's corporate front-end web infrastructure, the researcher tells ISMG.
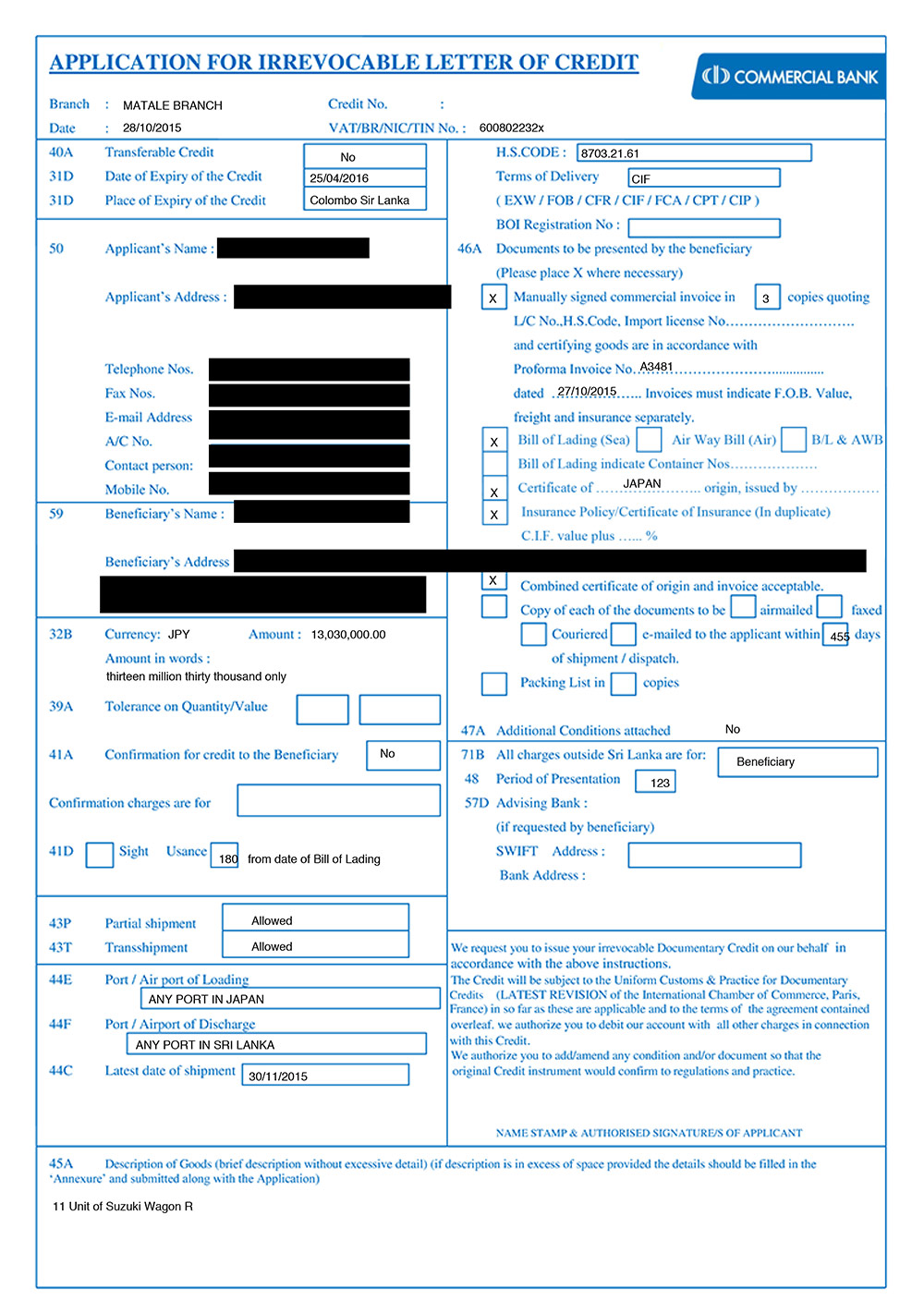 A sample file from the Commercial Bank of Ceylon dump
A sample file from the Commercial Bank of Ceylon dump
The attackers appear to have compromised the bank's systems using a SQL injection attack and uploading a Web Shell - a script that enables remote administration - onto the bank's PHP server, the researcher says. He bases this conclusion on the presence of artifacts from the hack in the data dump, including logs and files the indicate where the SQL injection was used and where the Shell was injected.
Bozkurtlar attackers had posted on Twitter, on a handle which has since been taken offline, that they would continue posting data from Asian and Middle Eastern banks, after the first dump of data from QNB (see: Qatar National Bank Suffers Massive Breach).
Many have been questioning the motives of the Bozkurtlar attackers, given the lack of any hacktivist message, announcement or reports of attempts at blackmail. However, analysis has revealed some common patterns and methods in the attacks, the researcher claims.
The Havij Connection
Several of the attacks appear to have involved an Iranian automated SQL injection tool called Havij 1.18 Pro, as per logs found in the leaked data, which includes the tool's payload, the researcher says. The attackers seem to have been successful in compromising Commercial Bank of Ceylon's web-facing front-end using a combination of this tool and Web Shell upload, but were unable to pivot onto the internal network as a result of relatively strong internal security controls.
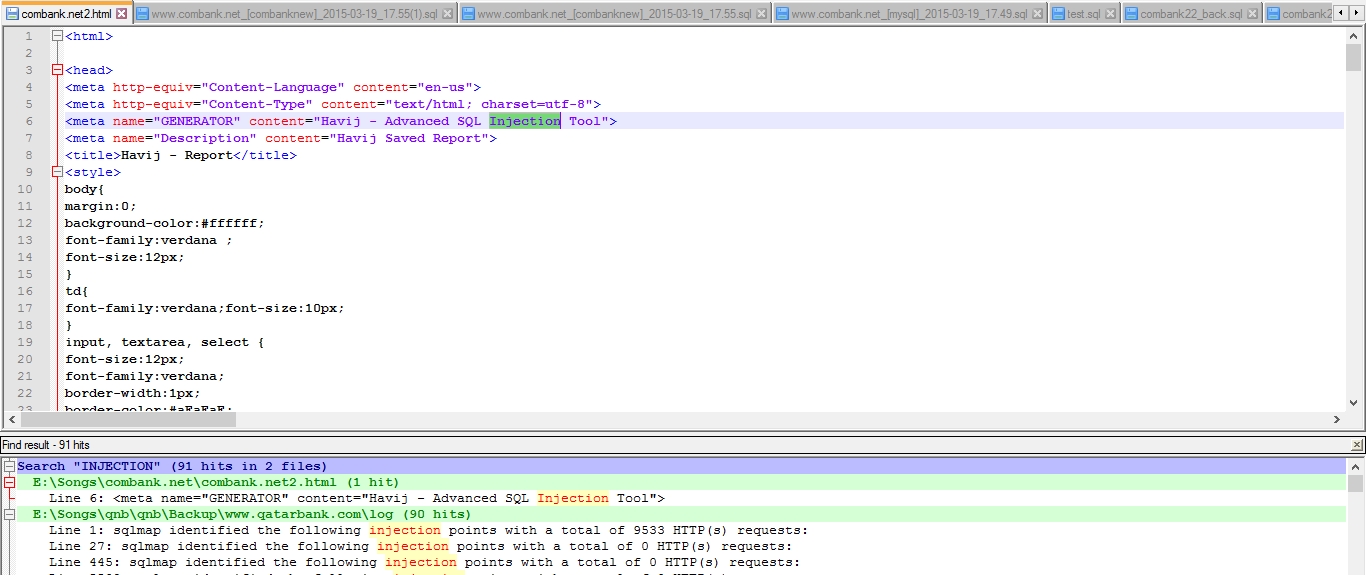 Havij log from Commercial Bank of Ceylon compromise dump
Havij log from Commercial Bank of Ceylon compromise dump
In addition to the Commercial Bank of Ceylon attack, the Havij advanced SQL injection tool was apparently used in the attacks against Kathmandu, Nepal-based Sanima Bank and Dhaka, Bangladesh-based Dutch Bangla Bank, the researcher confirms. The Qatar National Bank breach also involved an SQL injection and Web Shell combination, but it remains unclear if it involved the Havij tool (see: Dissecting a Hacktivist Attack).
The automated SQL injection tool has gained a lot of popularity with the cybercriminals and white hat researchers alike, because of the ease with which SQL injection attacks could be launched - literally at a click of a button - greatly reducing the effort and expertise required to launch such attacks.
Havij was written by Farshad Shahbazi, a security researcher at Iranian security firm the ITSecTeam, who also goes by hacker moniker r3dm0v3. The tool was released in July 2009 and the ITSecTeam started offering a free version in 2010, making the tool popular with hackers worldwide - regardless of the hat they are wearing, notes a blog on the Havij. While Havij was discontinued at the end of 2014, it is still freely available for download online.
ITSecTeam was in the news earler this year when a grand jury in New York indicted seven Iranian nationals who were allegedly working on behalf of the Iranian government - some of whom were employees of ITSecTeam - for their alleged involvement in conspiracies to conduct a coordinated campaign of distributed denial-of-service attacks against U.S. banks and others from 2011 through 2013 (see: 7 Iranians Indicted for DDoS Attacks Against U.S. Banks).
- Details
- Category: Security News
Breach Preparedness , Data Breach , Risk Management
Millions of Users Could Be at Risk If Flaw Is Leaked
Mozilla wants the U.S. government to provide it with information about a possible unpatched vulnerability in its Firefox browser, which was used by the FBI as part of a large child pornography investigation.
See Also: Proactive Malware Hunting
Mozilla filed a brief on May 11 in U.S. District Court for the Western District of Washington, saying it feared that early disclosure of the vulnerability would put millions of users at risk.
On Feb. 17, the federal court granted a motion asking for the disclosure of the vulnerability to the defense counsel of Jay Michaud, a middle school teacher who is charged in relation to Playpen, a now-shuttered child pornography website site. Mozilla's brief asks the court to require the government to disclose the information at least 14 days before the defense counsel receives it.
"Any disclosure without advance notice to Mozilla will inevitably increase the likelihood the exploit will become public before Mozilla can fix any associated Firefox vulnerability," according to the brief.
Mozilla's filing comes as technology companies have increasingly clashed with the U.S. government over vulnerability disclosure and encryption.
Playpen Investigation
Two years ago, the White House pledged a greater commitment to the Vulnerability Equities Process, a framework set up six years ago for notifying companies about zero-day vulnerabilities.
In the child pornography case, the FBI used the vulnerability to gather evidence on tens of thousands of users of Playpen, which was a "hidden" website that used the Tor anonymity system. Tor, short for The Onion Router, routes Internet traffic through a network of proxy servers, making it difficult to discover a user's real IP address.
Hidden websites that use the Tor system have a ".onion" URL. Such sites can only be visited using the Tor browser, which is a special browser based on Firefox's open-source code.
Tor is widely used by activists, dissidents, journalists and others who want greater anonymity in their web browsing, but the system is equally utilized by those involved in illegal activity.
Controversially, the FBI controlled Playpen for almost two weeks early last year. The agency used the browser vulnerability to record the real IP addresses of those who visited Playpen in order to later identify them.
It's unclear if the vulnerability lies within the Firefox code base or is part of the additional code added into the browser for the Tor functions. Mozilla hopes to find out.
"Court-ordered disclosure of vulnerabilities should follow the best practice of advance disclosure that is standard in the security research community," wrote Denelle Dixon-Thayer, Mozilla's chief of legal. "In this instance, the judge should require the government to disclose the vulnerability to the affected technology companies first, so it can be patched quickly."
Apple Vs. FBI II?
Mozilla's move adds to the friction between the U.S. government and technology companies over software flaws and encryption.
In February, Apple resisted a legal order that would have required it to create a customized version of iOS 9 in order to unlock the iPhone 5C of Syed Rizwan Farook, one of the San Bernardino mass shooters (see: FBI-Apple Aftermath: Finding the Elusive Compromise).
The U.S. government later said it had found a way to unlock the device without Apple's help, fueling speculation that a zero-day vulnerability had been found in the operating system that Apple didn't know about.
On May 11, FBI Director James Comey said the agency merely bought a tool from a company to crack the iPhone and not the software flaw itself, according to the Washington Post. Comey said the agency wasn't trying to avoid a review under the Vulnerabilities Equities Process, but it did not have enough knowledge of the method used, the publication reported.
More Articles …
Page 3427 of 3546
