- Details
- Category: Security News
Establishing new laws and regulations to address privacy and cybersecurity concerns related to the Internet of Things would likely be ineffective, says attorney Steven Teppler, who co-chairs an American Bar Association committee addressing IoT issues.
"This is a very, very hotly contested issue," Teppler says in an interview with Information Security Media Group.
At a recent ABA-sponsored meeting about the Internet of Things, Teppler notes, "it was clear from the regulatory agencies who presented that putting out [new] regulations or laws would typically wind up being so outdated by the time they become effective that ... they would possibly operate against stakeholders' interests."
As a result, the best path forward, he says, is likely industry self-regulation "tempered by lawsuits which will help develop the legal framework by which these devices should be developed and managed during their lifespan."
Biggest Dangers
The most concerning Internet of Things devices are those that "if misused or are defective in the mechanical world can cause either property damage or personal injury," Teppler says.
For example, if a stove that can be operated remotely by a smartphone had defects and vulnerabilities in its software, a command to cook something for one hour could result in an instruction to cook something for 20 hours, he says. And automobiles, he notes, contain "sensors, chipsets and operating code ... that introduce new vectors for damage and personal injury." (See An In-Depth Analysis: How Automobiles Can be Hacked).
In the healthcare arena, certain devices used to share data with providers, insurers or device manufacturers could pose privacy risks if security measures are lacking, he adds.
In the interview (see audio player below photo), Teppler also discusses:
Potential risks posed to the privacy and security of personally identifiable information by Internet of Things devices; How to address the security of internet-connected medical devices and other health-related gear; Privacy concerns related to internet-connected toys.As a partner at the Abbott Law Group, P.A. in Jacksonville, Fla., Teppler leads the firm's electronic discovery and technology-related litigation practice. He is also an adjunct professor at Nova Southeastern University Law School. Teppler is the co-chair of the Internet of Things Committee of the American Bar Association's Science and Technology Section and past co-chair of the eDiscovery and Digital Evidence Committee of the American Bar Association.
- Details
- Category: Security News
Baking security into information systems from the get-go has been an unrealized goal at most enterprises. That's because organizations, in piecing together their systems, rely on hardware and software from vendors who don't always consider security a high priority.
But new guidance - based on engineering principles - from the National Institute of Standards and Technology is aimed at helping technology vendors build secure components their customers can use to build trustworthy information systems. After all, "consumers can't design or modify source code, or do the other tasks necessary for full-spectrum security," Ron Ross, NIST Fellow and guidance lead author, points out in an interview with Information Security Media Group (click on player below photo to listen).
The guidance, Special Publication 800-160: "Systems Security Engineering: Considerations for a Multidisciplinary Approach in the Engineering of Trustworthy Secure Systems," also includes chapters designed to help security professionals and other executives assess products that could be used to build trustworthy systems.
Systems Security Engineering
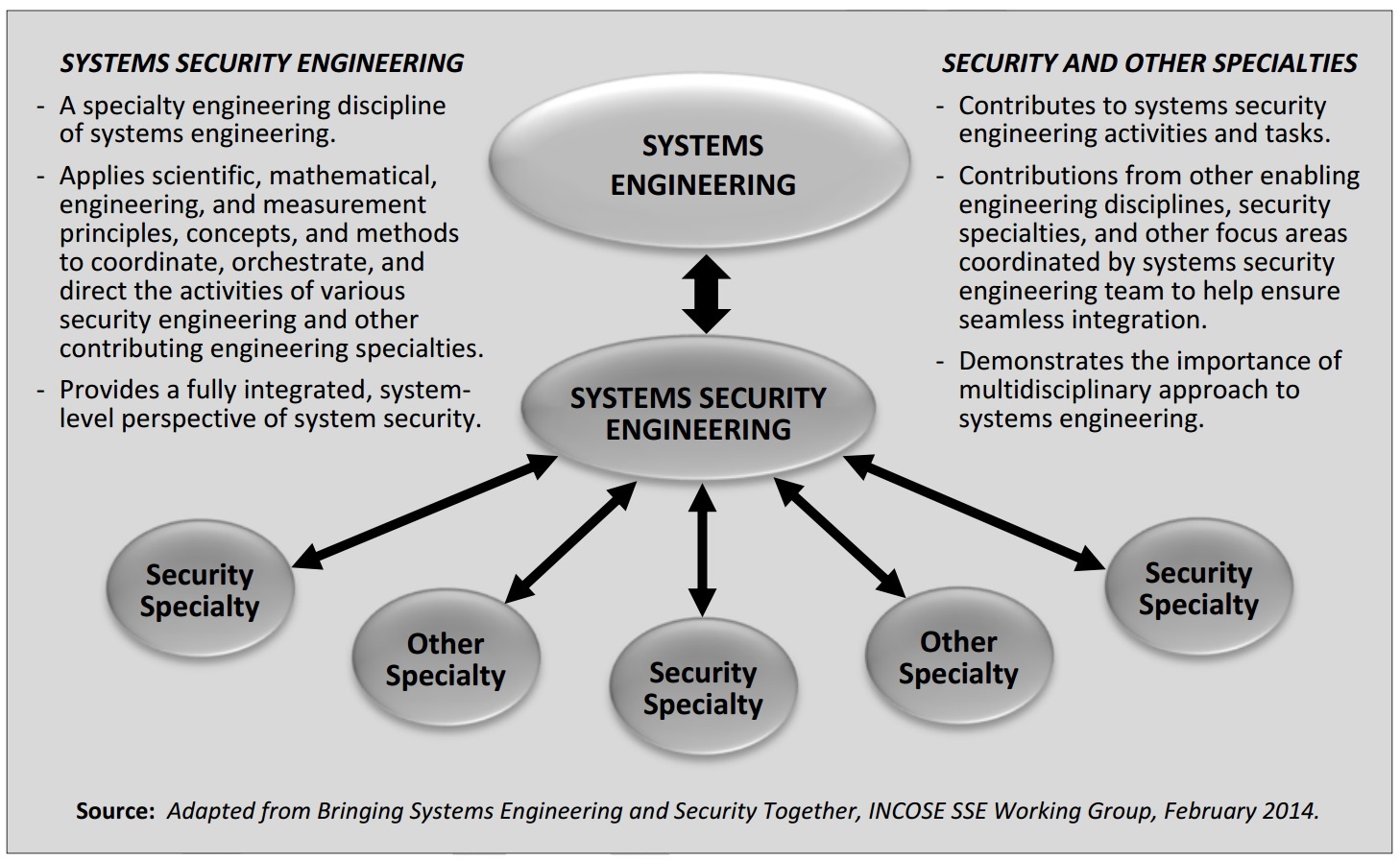
"We're all relying on the same commercial products today," Ross says. "This is going to give us an opportunity to take a step back to see how we can build security in from the start. We have talked about that forever, but now we do have an approach that can work to help us do the things that been saying for years."
NIST this past week issued the second draft of SP 800-160, a result of nearly five years of work by Ross and his colleagues. It's soliciting comments on the current draft at
In the interview, Ross discusses:
Ways the new guidance encompasses a disciplined, engineering approach to building security into hardware, software and firmware; How the guidance could help CISOs and others get buy-in from senior executives for building trustworthy and resilient systems; and The holistic enterprise view of IT security the guidance promotes and how it could help security practitioners and others to identify the often invisible dangers lurking within IT systems.Systems Security Engineering Framework
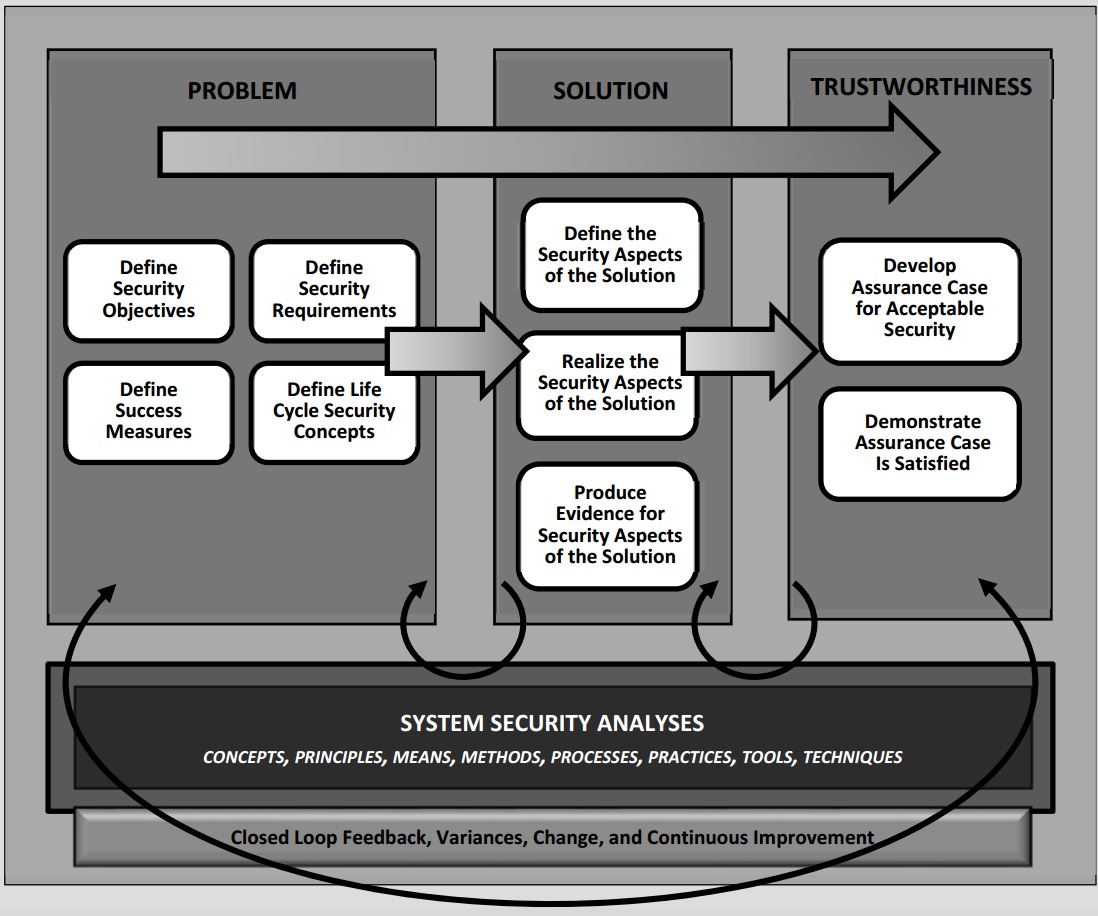 Source: NIST
Source: NISTRoss says the guidance encourages enterprise managers to assess the value of their information assets. Then, he says, they should use security design principles and systems engineering processes to develop appropriate security requirements, architecture and design. The objective is to implement a security capability that can adequately protect information systems and reduce a system's susceptibility to adverse consequences from threats and other hazards, all in the context of an organization's tolerance for risk.
"The systems security engineering considerations give organizations the capability to strengthen their systems against cyberattacks, limit the damage from those attacks if they occur, and make their systems survivable," Ross says.
Security consultant Robert Bigman, former CISO at the Central Intelligence Agency, sees SP 800-160 as becoming the "de facto standard for integrating 'trustability' into the design, development, deployment and operation of systems used both within government and commercial critical infrastructure industries."
Hear Ross, Bigman Speak at ISMG Summit
Bigman and Ross will be featured presenters at the ISMG Fraud and Breach Prevention Summit in the Washington, D.C., area on May 18. Bigman will lead a session titled "Creating 'Trustability' to Strengthen Breach Defenses." Ross will deliver a keynote address on "Securing New Generation of IT: The Promise Engineering-Based Approach." Registration is now available online.
Ross was also lead author of NIST SP 800-30 and SP 800-37, guidance on risk assessment and risk management. He specializes in security requirements definition, security testing and evaluation and information assurance. Ross leads NIST's Federal Information Security Management Act Implementation Project, which includes the development of key security standards and guidelines for the federal government and critical information infrastructure.
See also: Video: Ron Ross Promotes New InfoSec Approach and Applying Engineering Values to InfoSec, an audio interview with Ross on the first draft version of SP 800-160.
- Details
- Category: Security News
Cybersecurity , Data Breach , Fraud
Summit to Explore Cybersecurity Agenda for 45th President Washington Conference Will Feature Top InfoSec Influencers President Obama with his national security advisers.
President Obama with his national security advisers.The Obama administration has implemented a number of cybersecurity and privacy initiatives aimed at making IT more secure for the federal government and the private sector. Those include the cybersecurity framework, National Strategy for Trusted Identities in Cyberspace, employing encryption and sharing cyberthreat information.
See Also: Security Shouldn't be Boxed: The Cloudified Edge & End of an Era for Hardware Box Providers
Will the next president carry on the Obama cybersecurity policies or decide to take a different approach? That's a question to be debated by a panel of experts at Information Security Media Group's Fraud and Breach Prevention Summit in the Washington area May 17 and 18.
The summit also will feature keynote addresses by government luminaries, including Department of Homeland Security Deputy Undersecretary for Cybersecurity Phyllis Scheck, National Institute of Standards and Technology Fellow Ron Ross and Virginia Technology Secretary Karen Jackson.
Phyllis Schneck addresses how computers can defend against malware much as the human body fights off viruses.Other sessions will feature presentations by Jeremy Grant, former head of the National Strategy for Trusted Identities in Cyberspace, an initiative to create a trustworthy identity cyber-ecosystem; former U.S. CERT Director Mischel Kwon; and longtime Central Intelligence Agency CISO Robert Bigman.
These influencers and others will cover topics that reach beyond the government and have a direct impact on how private enterprises secure their systems to prevent fraud and breaches.
Political Issues
The panel on how the next president will deal with cybersecurity will include Karen Evans, former federal CIO; Ari Schwartz, former special assistant to the president and senior director for cybersecurity; Steve Chabinsky, a member of the presidential Commission for Enhancing Cybersecurity and former FBI deputy director for cyber; and Larry Clinton, chief executive of the Internet Security Alliance.
It's not at all clear how the next president will tackle cybersecurity because the candidates have not extensively articulated their goals. But the panel will explore what existing programs will likely be retained by the next administration and which ones could be eliminated or altered. Plus, the panelists will discuss potential new cybersecurity initiatives the next president would pursue. Our experts will address:
The cybersecurity priorities facing the 45th president; How the experiences of the candidates reflect the way they'd address cybersecurity as president of the United States; and How the next president's cybersecurity initiatives will influence the way your organization secures its IT.Keynote Speakers
One of the keynoters who will address critical cybersecurity issues is Schneck, DHS's top policymaker devoted solely to cybersecurity, and her portfolio includes overseeing the voluntary program in which the government and private sector share cyberthreat information. Schneck also is a leading proponent of malware provenance, which examines malicious code to identify attributes that could be shared by other malware (see DHS Eyes Malware Provenance to Identify Malicious Code).
Ron Ross discusses the impact of new NIST guidance on adapting engineering practices to cybersecurity.NIST's Ross, another keynoter, will discuss draft guidance on systems security engineering, which details an integrated approach to building trustworthy resilient systems. It's a novel scheme for enterprises to establish their IT security programs (see How to Bake Security Into IT From the Start).
Virginia's Jackson will conclude the summit with a presentation on how the state's Office of the Secretary of Technology works with stakeholders inside local, state and federal government, as well as in the private sector, to beef up security (see VA Gov. McAuliffe on Cybersecurity).
Other Hot Topics
Other sessions will tackle such critical issues as the authentication, the emerging threat landscape, identity management, the insider threat and ransomware.
"Identity as the Great Enabler: Improving Security, Privacy and Customer Experiences," will feature former NSTIC leader Grant, now managing director at the security adviser Chertoff Group, and Liz Votaw, senior vice president of Bank of America's OmniChannel Authentication Strategy. This session will explore how identity "done right" is a fundamental building block for any CEO and CISO, enabling organizations to streamline processes and enable more user-friendly online experiences for employees, partners and customers (see Enhancing Authentication: Status Report)
In another session, Kwon, the former U.S. CERT director, will be joined by Brian Varine, Justice Department security operations center manager to discuss: "Investigating the Unknown: Improving Security Operations." And former CIA CISO Bigman will offer a presentation on creating "trustability" by strengthening breach defenses (see Former CIA CISO on Practical Defensive Measures ).
The sessions outlined here are just part of a jam-packed day-and-a-half summit agenda that also features a number of non-government fraud and breach prevention experts. Please check out the complete agenda, and I hope you'll join me at this educational event.
- Details
- Category: Security News
Authentication , Data Loss , Technology
Mail.Ru Says Leaked Credentials 99.982% Invalid But Hold Security Claims Leaked Email Addresses Pose Phishing Risk
A security firm's report that it obtained 1.17 billion email credentials from a young Russian hacker is "media hype," according to Russian email service Mail.Ru, which says virtually all of the leaked data for its users - a substantial subset of the leaked data - is invalid (see: 272 Million Stolen Credentials For Sale? Don't Panic).
See Also: Rethinking Endpoint Security
Hold Security CISO Alex Holden told Reuters that his firm obtained the collection of leaked data, including 272 million unique credentials, for free from a young Russian hacker that he dubbed "the collector." The security company said the collector's data set included login credentials for multiple email services, including Gmail, Hotmail and Yahoo, as well as 57 million accounts for Mail.Ru. But Holden also said that it wasn't clear how many of the credentials might work.
On May 6, after analyzing the 57 million Mail.Ru credentials included in the dump, Mail.Ru determined that virtually all of the account credentials for its users are invalid, a company spokesman tells me. "According to Holden himself, 99.55 percent of the username/password combinations are outdated. Our analysis shows that the number of the expired or otherwise invalid combinations is even higher (99.982 percent)," Anna Artamonova, who heads Mail.Ru's email and portal division, says in a statement. "The number of Mail.Ru accounts in the database is large due to the fact that Holden has acquired the database from a Russian 'hacker,' and Mail.Ru is the biggest email provider in Russia and the Russian-speaking Internet segment."
Mail.Ru says it notified the 0.018 percent of affected users whose valid credentials were found in the dump. But 23 percent of the Mail.Ru email addresses in the data dump don't exist, Mail.Ru said, and 64 percent have incorrect passwords - although that could also be because the email address was being used for a different website. Finally, 12.4 percent of the Mail.Ru accounts included in the data set "had already been marked as suspicious," meaning "our system considers those either hacked or controlled by a robot, and blocked," thus requiring users to go through account-recovery procedures to regain access.
Accusation: Report is Hype
Artamonova says that the collection of credentials "is most likely a compilation of a few old data dumps collected by hacking web services where people used their email address to register," thus suggesting that most of the other data included in the leak is also outdated.
Given the fact that the data dump of credentials for Mail.Ru users was almost completely outdated, "it is fair to assume that the sole purpose of issuing the report was to create media hype and draw the public attention to Holden's cybersecurity business," Artamonova contends.
But Holden has called those allegations "baseless," and said his firm responded quickly to all of Mail.Ru's inquiries, including sharing the data leak with the email provider directly, so it could determine whether the information posed a risk and take appropriate measures to protect any affected customers.
Holden also repeated that of the 1.17 billion credentials his firm obtained on underground forums, it had already reported that only 42.5 million credentials appeared to be new, while it had seen the rest in prior data dumps. "We reported accurately that a person from Russia gathered hundreds of millions of stolen credentials and gave them away to fellow hackers - or security researchers posing as hackers," he says.
Service Providers Monitor Dumps
In the wake of Holden's initial report, I reached out to Google, Microsoft and Yahoo, to ask how they were responding, and if any of the account data appeared to be valid.
None have shared any validity findings with me. And while Google has yet to respond at all, Yahoo and Microsoft told me that they were investigating the breach report.
"Unfortunately, there are places on the internet where leaked and stolen credentials are posted, and when we come across these or someone sends them to us, we act to protect customers," a Microsoft spokeswoman told me. "Microsoft has security measures in place to detect account compromises and requires additional information to verify the account owner and help them regain sole access to their account."
Mail.Ru says it, too, actively monitors data dumps on behalf of its users. "We regularly monitor the web for credential dumps and check them in order to take steps to protect our users when necessary. We take a very serious approach to ensure our users' security, and we take special pride in our information security team," Artamonova says. "It's sad that this case casts a shadow over their image."
But Holden tells me that wasn't his intention. "I have no reason to doubt that security measures of the Mail.Ru services are good," Holden says. He contends, however, that the valid email addresses that his firm turned up in the data dump could be used for phishing and spamming attacks.
- Details
- Category: Security News
Authentication , Data Loss , Technology
272 Million Stolen Credentials For Sale? Don't Panic No One Knows If Leaked Account Credentials Even Work
(Note: An update on this report is now available.)
Don't fear the leaked logins.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
That's the message from numerous security experts in the wake of reports that Milwaukee-based Hold Security obtained 1.17 billion stolen credentials - of which 272 million are unique - for free from an unidentified "kid from a small town in Russia."
Hold Security CISO Alex Holden tells Reuters that the leaked credentials are for tens of millions of email addresses tied to the world's biggest email service providers. All told, he claims, the login information includes credentials for 40 million Yahoo, 33 million Hotmail and 24 million Gmail email accounts; hundreds of thousands of accounts for email service providers in China and Germany; and 57 million accounts tied to Russia's Mail.ru, which says it sees 64 million active email users per month.
In a blog post, Hold Security says that the collected information was amassed by a young Russian hacker over an unspecified period of time, and that he originally attempted to sell it for just 50 rubles ($0.75), before giving it away to Hold Security in exchange for some "likes" on his social media accounts.
"We do not pay hackers for stolen data," Hold Security says. Holden also tells Reuters that the company alerts and shares recovered data with relevant organizations, and that it charges little or nothing for doing so.
Google didn't respond to a request for comment about the Hold Security data and whether it appeared to be accurate or still active, while Microsoft and Yahoo say they're investigating.
But Mail.ru tells me that it's obtained a sample of data that contains Mail.ru email accounts from Alex Holden. "Early analysis shows that many username/password combinations contain the same username paired with different passwords. It means that the [data set] is compiled from different sources, where people used email addresses as their usernames" a Mail.ru spokeswoman says.
The firm says it will warn any users if it finds their active login credentials in the data set, although so far, it has found none. "We are now checking whether any username/password combinations match valid login information for our email service, and as soon as we have enough information we will warn the users that might have been affected," the spokeswoman says. "The first check of a sample of data showed that it does not contain any combinations valid for [accessing Mail.ru] email [accounts]."
Account Credential Warning Redux
If the warning over a massive quantity of credentials being offered for sale online by a Russian sounds familiar, that's because it recalls a 2014 warning from Holden about "what could be arguably the largest data breach known to date," by a group he dubbed CyberVor ("vor" is Russian for thief). Holden claimed the group amassed 1.2 billion unique credentials tied to more than 500 million email addresses, in part, by exploiting known flaws to hack into websites. But it was less a breach and more a semi-curated list of potentially active access credentials for various sites (see CyberVor Update: Hold Security Responds).
The warning by Hold Security led the FBI to investigate, as well as to question Holden about how exactly he'd found the information. The FBI said Holden declined to answer that question, citing confidentiality agreements (see FBI Probes 1.2B Stolen Credentials). Hold Security also caught flak from security experts for appearing to use the breach to advertise a $120 per year service designed to alert organizations when the security firm found their customers' account details in data dumps or for sale on cybercrime forums.
Fast-forward to April 2016, and a hacker reportedly offering to part with stolen credentials for less than $1, which suggests that the proffered data quality is poor, at best. And Hold Security's pattern of trumpeting large sets of allegedly stolen or leaked user credentials also has many security experts questioning the usefulness of its reports.
"Based on similar reports by Hold Security in the past, we suggest that the method and tone of this disclosure is intended to generate media attention and marketing rather than highlight an actual increased threat," threat-intelligence firm iSight Partners says in a research note.
Massive Leaked-Data Sets? Not Unprecedented
To be clear, we are talking about a substantial amount of account data, although such a collection would not be unprecedented, iSight Partners notes. But it's not clear how the credentials were amassed, if they still work or if they were ever legitimate. "There is no evidence that these credentials are associated with active user accounts, and could easily include data obtained from publicly leaked breaches, accounts created through automated means by malicious actors, data from credential theft botnets and numerous other sources," iSight Partners says.
With all that in mind, security expert Troy Hunt, who runs the free "Have I Been Pwned?" service to alert email accountholders when their details show up in data dumps, advises everyone to "chill a bit" over what he characterizes as a "very inconclusive incident."
Everyone need to chill a bit over this incident, there's very little info on where they came from or if even legit https://t.co/FWRAhFlSqi
For now, take these and any other reports about email account credential leaks with a grain of salt. Also don't rush to change Gmail, Hotmail, Mail.ru or Yahoo email address passwords unless advised to do so by those firms.
On the other hand, now is a great time to ensure that you're not reusing passwords (see Why Are We So Stupid About Passwords?). Also activate multifactor authentication for any service that offers it. That way, even if your valid email account credentials do get stolen, you'll still be protected.
Mail.ru, for example, says it's made numerous, related upgrades and changes. "Last year we launched a two-factor authentication, which we strongly recommend all our users to set up as it is one of the most effective ways to protect an email account," its spokeswoman tells me. "Also, we no longer offer new users a security question as a password recovery method."
More Articles …
Page 3423 of 3546
