- Details
- Category: Security News
Anti-Malware , Data Breach , Data Loss
Long-Running Espionage Malware Campaign Has Suspected Russian Government Ties
The Swiss government now says that online attackers used a variant of "Turla" malware to steal at least 23 GB of data from a state-owned defense firm since 2014.
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
The government had already confirmed on May 4 that technology firm RUAG, based in Bern, had been hacked. In addition to the defense sector, state-owned RUAG operates in aerospace, aviation and other sectors.
On May 23, the Swiss government released a 34-page technical report on the hack attack, "to give organizations the chance to check their networks for similar infections, and to show the modus operandi of the attacker group." The report, released via the Swiss public-private partnership called Melani, was prepared in conjunction with Switzerland's computer emergency response team, GovCERT.
The government says its intention isn't to assign blame over the long-running breach because "these attacks may happen to [any] organization regardless of their security level," but rather to help others spot and block similar attacks.
Several information security experts have praised the hack attack report, which includes "indicators of compromise" that can be used to identify signs of related attacks in other networks, as well as defenses that can be used to detect and block related attacks.
"[The] new RUAG report is a very big step on the part of the Swiss," Thomas Rid, a professor in security studies at King's College London, says via Twitter. "Kudos to @GovCERT_CH for raising the bar on governmental attribution reports."
Switzerland isn't the first country to attribute an attack to a specific type of malware, or a group known to have used that malware. In the U.S., for example, the FBI blamed "North Korea actors" for the hack and wiper malware attack against Sony Pictures Entertainment in 2014. But the Swiss report is notable because it lets published technical details do the talking, rather than relying on public officials to make allegations based on unreleased, classified information.
Attribution: Malware, Not Actors
The Melani reports say investigators have purposefully not attempted to attribute the RUAG attacks to a specific group or nation "because - unfortunately - many actors use malware and network intrusions."
But the Turla malware, also known as Snake or Uroburos, has been previously tied to attacks launched by Russian-language speakers. Some security researchers believe that Turla has been used in numerous attacks that have alleged ties to Russian intelligence services. They say that related campaigns stretch back to 2007 or 2008 cyberattacks in the United States that used malware known as Agent.BTZ, which also appeared to have been written by Russian-speaking developers.
The Melani report also describes a variety of countermeasures - many of which are not cost-intensive - that can be used to spot related attacks. "Even if it is difficult to completely protect an organization against such actors, we are confident that they are detectable, as everyone makes mistakes," the report says. "The defending organization must be ready to see such traces, and to share this information with other parties, in order to follow such attackers closely."
Target: Active Directory
The Melani report, which is based on RUAG's security logs, says that attackers demonstrated "great patience during the infiltration and lateral movement," focused only on targets of interest and alternated periods of relative inactivity with "high-activity periods with many [data] requests and big amounts of exfiltrated data," occasionally stealing 1 GB in a day.
After attackers gained access to RUAG's network - Melani says the initial infection vector hasn't been discovered - they also focused on infecting other systems and gaining higher levels of access, aided by a Trojan reconnaissance tool called Tavdig, which is also known as Wipbot and Epic. "One of their main targets was the Active Directory, as this gave them the opportunity to control other devices and to access the interesting data by using the appropriate permissions and group memberships," the report says. Attackers also created peer-to-peer connections between infected devices, using Windows named pipes, to help relay instructions from command-and-control servers to infected endpoint, as well as move stolen information, in a difficult-to-detect manner.
Attackers used some infected endpoints - or bots - to obtain and relay information inside the network and other bots to exfiltrate the data, again to make the attack more difficult to spot. "Some [bots] took the role of a communication drone, while others acted as worker drones," the report says. "The latter ones never actually contacted any C&C servers, but instead received their tasks via named pipes from a communication drone, and also returned stolen data this way. Only communication drones ever contacted C&C servers directly."
The report says that based on a digital forensic investigation, related attacks date from at least September 2014. "Unfortunately, log files at RUAG only go back until September 2014, where we still see C&C activity," the report says. "Additionally, many suspicious devices have been re-installed in the meantime; hence, we cannot determine the initial attack vector." But one possibility, it adds, is that systems were initially infected by targeting websites frequented by RUAG employees via so-called watering-hole attacks.
Highly significant: Swiss gov't publishes detailed APT report, links Ruag cyber attack to Turla, ancestor: Agent.BTZ pic.twitter.com/y9pRzR2G2w
Stolen Information: Value Remains Unclear
The Melani report says that although at least 23 GB was stolen, it's not clear how much of that information might have been of value, in part because investigators didn't discover the attack and begin monitoring attackers until January 2016. "The size of exfiltrated data gives no insight about the confidentiality and the value of the stolen data," the report says. "It is not possible to find out what data actually was stolen using proxy logs because no wiretap was in place before the attack was detected."
But RUAG did begin monitoring the attackers' activities closely after it discovered the attack campaign in January. It says that monitoring continued until May 3, when the related investigation was revealed via multiple press reports, thus tipping off the attackers. "This leakage heavily [damaged] the ongoing investigation, rendering the ongoing monitoring useless," the Melani report says.
- Details
- Category: Security News
Anti-Malware , Encryption , Technology
Kansas Heart Hospital Pays Ransom, Gets Told to Pay Again
Kansas Heart Hospital, based in Wichita, fell victim to a ransomware attack on May 18 and chose to pay the ransom attackers were demanding. But then the hospital was told that to regain full access to files, it would have to fork over an even bigger ransom.
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
So reported CBS-affiliated television station KWCH, noting that the hospital - which had a pre-prepared ransomware response plan in place - opted to not pay any further ransoms.
Kansas Heart Hospital "felt [that this was] no longer ... a wise maneuver or strategy," Dr. Greg Duick, the hospital's president, told KWCH.
The hospital couldn't immediately be reached for further comment on the circumstances surrounding the ransomware outbreak or how much the hospital did pay to attackers. "I'm not at liberty, because it's an ongoing investigation, to say the actual exact amount," Duick told KWCH. "A small amount was made."
Duick added that the hospital's pre-prepared backup plan meant that affected systems could be - and were in the process of being - restored by the hospital's IT staff. "That plan went into immediate action. I think it helped in minimizing the amount of damage the encrypted agent could do," he said. "The patient information never was jeopardized, and we took measures to make sure it wouldn't be."
The Kansas Heart Hospital outbreak follows a surge in ransomware attacks against organizations of all sizes, as well as individuals.
Security experts say many ransomware attacks are random. "Since the average ransom demanded from an individual user is relatively low - typically a few hundred dollars, if that - threat actors distributing ransomware typically follow the 'spray and pray' tactic of sending out as many lures as possible - emails with malicious attachments or links to malicious websites, for example - to maximize their potential gains," researchers at threat intelligence firm FireEye say in a recent blog post. The researchers note that while ransomware attacks have been steadily increasing, beginning in March they saw a massive spike in related infections.
But some ransomware-using gangs have been launching more targeted attacks, often demanding relatively higher ransoms. In February, for example, Hollywood Presbyterian Medical Center acknowledged paying a $17,000 ransom to regain access to data that attackers had forcibly encrypted.
"The targeting of hospitals is no surprise," the FireEye researchers say. "Budget dollars often go toward surgery wards, emergency care centers and supplies for a large number of patients - not security. This makes for a tricky issue, since hospitals cannot operate without the necessary patient data stored in their systems."
Preparation Helps
Security experts say the best way to mitigate the impact of a ransomware attack is to prepare in advance, in part by running up-to-date anti-virus engines and signatures on all systems and ensuring that all critical data gets backed up to servers that aren't connected to the same network, so that a ransomware outbreak can't successfully encrypt them as well.
But even well-prepared organizations will typically face some type of disruption following a ransomware outbreak. In February, for example, Lukas Hospital, based in Neuss, Germany, reported that it had been hit with TeslaCrypt 2.0 ransomware, and that it had complete backups of all systems in place. But the hospital estimated that after its systems were infected, it might take 48 hours in total before its IT environment was back to normal, after it took all systems offline as a preventative measure, before wiping and restoring them. As a result, the institution said that it had rescheduled about 20 percent of its surgeries and temporarily shifted less critical care to other hospitals.
Security experts say that it's up to every individual ransomware victim whether to pay a ransom. And at least in the United States and Western Europe, there are no laws that prohibit doing so (see Ransomware: Is It Ever OK to Pay?). As the Kansas Heart Hospital episode demonstrates, however, paying a ransom doesn't guarantee that victims will actually regain access to their encrypted files.
TeslaCrypt Shuts Down
In the case of new TeslaCrypt victims, however, there is now a way to decrypt files without paying the ransom, thanks to TeslaCrypt's developers having published their encryption key, together with an apology to victims (see Master Key to TeslaCrypt Released by Ransomware Gang). More recently, the gang has even linked directly to a related decryption tool subsequently created by security researchers.
Possible explanations for this surprise turn of events - beyond contrition - include the developers having built a new type of ransomware, or perhaps even having been hacked by a rival gang, "who spilled the master key to ruin their rivals' business," says researcher Paul Ducklin at security firm Sophos, in a blog post.
But the release of the decryption key follows TeslaCrypt's developers apparently having wrapped up their related operations recently, with many ransomware distributors having switched to using CryptXXX ransomware instead, according to the Bleeping Computer forum.
CryptXXX Takes Off
CryptXXX, meanwhile, has been receiving a number of updates recently, including one that arrived following the TeslaCrypt key release, according to a blog post from researchers at security firm Trend Micro.
To date, CryptXXX has been distributed in the wild primarily via legitimate but compromised websites, as well as via malicious advertisements tied to Angler exploit kit, the researchers say. In both cases, Bedep ad-fraud malware is used to also drop a copy of CryptXXX, which is designed to encrypt files while also blocking access to the PC, via a lock screen.
"What makes CryptXXX difficult to stop is that it runs alongside a watchdog program," the researchers say. "CryptXXX runs two simultaneous routines; one that encrypts, and the other to detect abnormal system behavior. When the watchdog detects abnormal system behavior that halts the encryption process, it restarts the encryption routine. This results in a cycle of stopping the malware, and the watchdog restarting the malware."
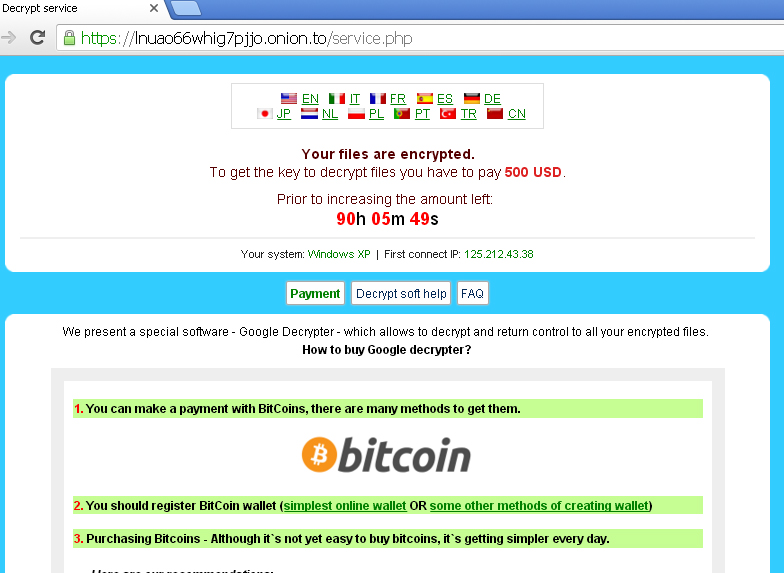 The CryptXXX ransom demand gives victims 90 hours to pay, before doubling the amount. (Source: Trend Micro)
The CryptXXX ransom demand gives victims 90 hours to pay, before doubling the amount. (Source: Trend Micro)
Many types of ransomware double their ransom demand every 24 hours until users pay, although there are some variations on that routine, such as deleting a swath of files every hour until victims pay (see Jigsaw Ransomware Adds Insult to Injury). But CryptXXX, for whatever reason, gives users 90 hours or more to pay the ransom, the Trend Micro researchers note, before then demanding double the amount. As that demonstrates, no matter the explosive growth of ransomware, different gangs will employ different strategies when it comes to trying to compel victims to pay.
- Details
- Category: Security News
Walmart's lawsuit against Visa, which claims the card brand is unfairly preventing retailers from requiring that customers enter PINs when they conduct EMV debit transactions at their points of sale, poses important questions about fair business practices, says Liz Garner of the Merchant Advisory Group, which represents large retailers.
In an interview at Information Security Media Group's recent Fraud and Breach Prevention Summit in Washington, Garner explains why the Walmart suit could impact how EMV in the U.S. is deployed. "Walmart wants to have the choice to implement the best business practice that makes sense for their business and their customers," she says.
Walmart's suit alleges that Visa won't allow the big box retailer to refuse customer requests for signature-based EMV debit transactions, which Walmart claims are far less secure than PIN debit. Limiting Walmart's control over how it conducts POS transactions in its stores is an unfair business practice, Garner argues, and ultimately puts Walmart at greater risk of fraud.
"This is really a move by Walmart to show that the PIN adds value to the customer and adds security to the transaction," she says. "Other merchants have been trying to get their customers to essentially enter their PINs at the point of sale as well. Walmart is not the only one; they just happen to be the one involved in litigation now with Visa."
Impact on Chargebacks
PIN entry helps protect merchants from fraud-related chargebacks, which have skyrocketed since the EMV fraud liability shift took effect in October 2015, Garner adds. "Chargebacks are really non-existent when it comes to PIN-debit transactions on EMV and mag-stripe," she says. "So there is an added benefit there, especially when you hear about the millions of dollars that are shifting over to merchants in chargeback liability post the Oct. 1 EMV shift (see EMV: Chargebacks Hitting Merchants of All Sizes).
During this interview (see audio link below photo), Garner also discusses:
Why routing competition for debit transactions, which is required by law under the Durbin Amendment to the Dodd-Frank Wall Street Reform and Consumer Protection Act, is limited in the current EMV environment; Why EMVCo., which oversees the EMV standard and its specifications, should be reviewed by the government; and Why Visa and MasterCard's efforts to support EMV PIN transactions in other parts of the world have not been mirrored in the U.S.Gartner is vice president at the Merchant Advisory Group, which represents 85 of the country's leading retailers. Previously, she served as director of commerce and entrepreneurship at the National Restaurant Association, representing the restaurant industry before Congress and regulatory agencies about issues impacting restaurant and food service profitability and entrepreneurship. Garner's areas of expertise include retail and mobile payments, data security, privacy, emerging technologies, taxes and finance.
- Details
- Category: Security News

A Japanese ATM cash-out scheme that stole $19 million from South Africa's Standard Bank in less than three hours illustrates why devising better ways to mitigate the risks posed by such schemes must be a priority for financial institutions in those markets - including the U.S. - that still rely on magnetic stripe debit cards.
See Also: How to Mitigate Credential Theft by Securing Active Directory
More vigorous fraud detection and transaction anomaly monitoring might have helped detect the Japanese heist sooner. But as long as ATMs continue to accept magnetic-stripe cards, cash-outs will pose a risk. In the U.S., most ATMs are not expected to begin accepting chip cards until the end of 2016.
"We should be concerned. The fraud activity isn't isolated to Japan. It could happen any place," says one executive with a leading U.S. card issuer, who asked not to be named. "Most issuers don't have numerous rules surrounding ATM activity because it is relatively small volume compared to the amount of spend. It is likely a few of these accounts cued someone and the pattern was noticed as being a trend."
But by the time the pattern was noticed, $19 million was already gone, Standard Bank told Reuters.
The Scheme
Standard Bank did not respond to Information Security Media Group's request for comment. But according to news reports from Reuters and others, the cash-out scheme is believed to be linked to a sophisticated criminal group that has extensive knowledge about how ATM transactions are accepted and transmitted in Japan.
Approximately 1,600 counterfeit mag-stripe debit cards cloned from card data stolen from Standard Bank accounts were used between the hours of 5 a.m. and 8 a.m. on Sunday, May, 15, at 1,400 ATMs located in 7-Eleven convenient stores in Japan, Reuters reports. Those ATMs are owned and operated by Seven Bank, only one of two banks in Japan that accepts cards from other countries, CNN Money reports.
Seven Bank and its parent company, 7-Eleven, did not respond to ISMG's requests for comment.
The well-organized scheme in Japan likely involved criminals with in-depth knowledge of the Japanese banking system, security experts say. The attacks targeted off-premises ATMs, which often have less surveillance than branch ATMs, and occurred after bank business hours in both Japan and South Africa.
"I strongly suspect there was some inside involvement with this organized fraud ring, i.e., current or former bank employees who were familiar with the hours ATM activity is monitored, what rules are set up to raise red flags, how long it would take the bank to notice and shut down fraudulent activity, and associated bank procedures," says Shirley Inscoe, a financial fraud analyst at consultancy Aite. "Off-premises ATMs are often targeted by fraud rings. It is easy to add hardware and cameras, and visual inspections of the machines happen far less often than with on-premises machines. It is a best practice for consumers never to use these machines, but consumers often opt for convenience over security."
A Global Trend?
Experts for years have warned of upticks in ATM cash-outs. For example, back in late 2013, federal authorities announced arrests linked to a $45 million ATM cash-out and prepaid card scheme that targeted banks throughout the world in late 2012 and early 2013 (see New Arrests in $45 Million ATM Cash-Out ).
As more markets ramp up migration to EMV cards, which help prevent counterfeiting, fraudsters will work overtime to ensure they can get as much bang for their cash-out buck before the mag-stripe completely disappears (see ATM Cash-Out: Why Banks Are at Risk and Why We Can Expect More ATM Cash-Outs).
"Cash-outs continue because it's the most direct route to stealing cash," says financial fraud expert Avivah Litan, an analyst at the consultancy Gartner. "It's much more direct than selling goods bought with stolen cards or taking over online bank accounts. With ATM cash-outs, the cash simply spews out of the ATM - a criminal's dream come true."
But the recent Japanese cash-out scheme appears to have been more sophisticated and targeted than most because it involved only 7-Eleven ATMs in one country using counterfeit cards stolen from only one bank, Litan adds.
"It is rather surprising that the thieves got away with this, given that Standard Bank is relatively sophisticated and has advanced fraud detection systems," she says. "I am guessing the criminals identified a very particular security weakness in Standard's fraud-detection system related to foreign magnetic-stripe cards used at foreign, low-tech ATMs. Certainly these less-sophisticated ATMs have less of their own fraud controls, for example, against skimming. And they also typically don't have the ability to detect abnormal access activity at the ATM itself."
But the executive at the card issuer who asked not to be named says Standard Bank deserves credit for detecting the scheme in less than three hours. Had counterfeit cards from numerous banks been used, he says, detection would have been even more difficult.
How Should Banks Prepare?
Monitoring for anomalous activity, such as detecting foreign cards being used multiple times at multiple ATMs over a short period of time, is essential to the fight against cash-out schemes, says Gray Taylor, a payments expert who is executive director of Conexxus, a convenience store and petroleum industry technology association.
"U.S. and E.U. [European Union] banks have put in the neural technology to track anomalies like this," he says. "That is why, sometimes frustratingly, you get declined when you try to use your card in a new country or city. Simple parameter-driven sentinels would have seen the spike in foreign transactions from one country and notified Standard Bank to shut down and verify."
More video surveillance at ATMs is also needed to fight fraud, Taylor adds. "Most off-premises ATMs do not have dedicated video. The U.S. Secret Service has noted this is also a cause for third-party ATM fraud in the U.S. - the video has the ATM off in the distance, and perps can't be identified."
Owen Wild, global director of security solutions at ATM manufacturer NCR, says banks and credit unions also must have multilayered defenses in place to detect the more sophisticated types of cash-out schemes.
"The combination of data, analytics, rules and real-time monitoring will enable financial institutions to monitor both the cards and the terminals on which the transactions are initiated for the likelihood of suspicious behavior," Wild says. "But in order for the maximum level of security of the transaction, full and complete implementation of the EMV standards is required through the processing chain."
Some larger U.S. banks are already considering additional out-of-band authentication that can help to verify the authenticity of ATM transactions to reduce risks associated with cash-outs, says John Gunn, a vice president at VASCO Data Security.
"We are already seeing large banks moving to integrate ATM security measures into their mobile banking applications," he says. "It is easy for fraudsters to buy stolen cards to make unauthorized withdrawals. But it's nearly impossible to commit theft if they must also have the intended victim's mobile phone physically at the ATM at the same time. You can expect to see banks leverage customers' mobile phones to reduce fraud across all channels in the future."
- Details
- Category: Security News
Breach Notification , Data Breach , Legislation
Both Nations Have Committed to Strengthening Notification Requirements
Neither Australia nor New Zealand has laws requiring organizations to notify people affected by data breaches, but officials in both countries are reviewing proposals and plan to introduce related legislation.
See Also: Security Shouldn't be Boxed: The Cloudified Edge & End of an Era for Hardware Box Providers
Regulators in both countries now generally encourage organizations to report breaches depending on the type of information released and the potential impact. But what constitutes a serious breach could be open to interpretation - a gap that both nations hope to close with new legislation.
New Zealand's Privacy Act
In 2011, New Zealand's Law Commission completed a five-year study of the country's Privacy Act, which went into effect in 1993. The review was launched over concerns and warnings that the law wasn't keeping up with the pace of technology changes.
One of the commission's key recommendations is that people should be notified of serious security breaches. The government went so far as to say that the best course of action would be to repeal the existing Privacy Act then re-enact it with various critical updates included.
In May 2014, then-Justice Minister Judith Collins said the government would introduce a targeted technical consultation on proposals before a bill was introduced to Parliament.
The proposals included requiring organizations to report data breaches to the privacy commissioner and to notify individuals in what are considered "serious" cases.
The mandatory reporting requirement would have two tiers. Under the first tier, which covers less serious breaches, organizations would be required to report "material" breaches, a calculation that takes into account the information leaked, number of people affected and if the lapse is part of a systemic problem.
A tier-two breach is more serious. In that case, organizations would have to take reasonable steps to notify the commissioner if there is a real risk of harm, such as loss, injury, significant humiliation or adverse effects on rights or benefits.
Failing to notify the privacy commissioner of a data breach would trigger a fine of up to NZ$10,000 ($6,750). Another proposal was to give the privacy commissioner new powers, including the ability to issue compliance notices, as well as stronger authority to investigate suspected privacy problems.
Two years later, however, there is still no new law on the books. But current Justice Minister Amy Adams said earlier this month that she intends to implement the reforms identified by the Law Commission and "modernize" the Privacy Act.
"I intend to release an exposure draft of the new Privacy Bill before the end of 2016 for targeted consultation," she said in a speech to the Wellington Privacy Forum on May 11. "This will provide an opportunity for privacy experts to comment on whether the draft bill implements the government's privacy reforms in a way that is clear, accessible and user-friendly." She plans to then introduce the bill in New Zealand's Parliament next year.
"These reforms will incentivize private entities and public sector agencies to value early identification and prevention of privacy risks that could cause harm," she said.
Australian Information Commissioner Guidelines
In Australia, there has been significant public support for some type of data breach notification requirement, according to a recent analysis by the law firm Corrs Chambers Westgarth. The Labor government introduced draft bills in 2013 and 2014, but a law never made it on the books.
Governments are generally reluctant to impose new regulations on businesses, says attorney Gordon Hughes, a partner with the Melbourne-based law firm Davies Collison Cave, who specializes in technology and data protection.
"Certainly there is resistance from the commercial sector to any form of significant mandatory data breach reporting obligation," Hughes tells Information Security Media Group. "A bank doesn't want to advertise to the world that their information has been compromised."
Currently, the Office of the Australian Information Commissioner recommends that breached organizations inform both the OAIC and those affected by a breach if there is a "serious risk of harm." The OAIC says organizations should consider what kind of personal information was breached, the cause and extent of the breach, as well as what harm individuals could experience, when assessing whether it's serious.
The OAIC's guidelines note, for example, that Australian Medicare numbers, driver's license details, health or financial information such as payment card numbers "might pose a greater risk of harm to an individual than their name or address."
It adds: "A combination of personal information typically creates a greater risk of harm than a single piece of personal information."
But while those might be the OAIC's recommendations, under current Australian law, organizations are under no obligation to notify consumers or the OAIC if they've been breached.
Australia: Support for Breach Legislation
But there's support from Australia's ruling Liberal Party to push ahead. In March, the government concluded a public consultation on the Privacy Amendment (Notification of Serious Data Breaches) Bill 2015, which would amend the country's Privacy Act of 1988 to incorporate a mandatory reporting requirement.
The notification requirement would apply to federal government agencies and private organizations with an annual turnover exceeding AU$3 million ($2.2 million). It also applies to foreign companies that deal directly with Australian consumers or process information on behalf of Australian businesses.
"The implications for Australian businesses (and foreign businesses conducting business in Australia) are likely to be significant and far-reaching," write Philip Cantania, partner, and Tim Lee, senior associate, both of Melbourne-based law firm Corrs Chambers Westgarth. "Australian companies that use offshore data processing services are particularly likely to be impacted."
Serious or repeated breaches could be subject to civil penalties up to AU$1.7 million ($1.2 million). Organizations would have 30 days to determine if a breach meets the reporting threshold.
Experts expect to see no action on the legislation until after Australia holds a federal election on July 2. Hughes said the issue of data protection hasn't even come up in current campaigns.
"Privacy is not a big vote winner," he said. "People just don't get excited about it."
More Articles …
Page 3433 of 3546
