- Details
- Category: Security News

In the wake of reports that 65 million stolen credentials from micro-blogging platform Tumblr have surfaced in a darknet marketplace, it's clear that 2016 is fast becoming the year of "historical mega breaches."
See Also: 2016 State of Threat Intelligence Study
That's Australian security expert Troy Hunt's encapsulation of the recently revealed, but older, string of massive data breaches (see Troy Hunt: The Delicate Balance in Data Breach Reporting).
Other older mega breaches that have just been revealed include the theft of 360 million accounts from MySpace - it's not clear when they were stolen - which is the biggest breach listed on "Have I Been Pwned?" - Hunt's free breach notification site. It's followed by the 2012 theft of 165 million accounts and 117 million credentials from LinkedIn, Tumbler, and then the 2011 breach of 41 million accounts at "adult social network" Fling, which also only came to light this month.
Hunt notes that together, these newly disclosed old breaches represent four of the five largest data breaches ever seen.
Tumblr Sounds 2013 Breach Alert
Tumblr first issued a related security warning pertaining to its 2013 breach this month, but it didn't indicate how many accounts may have been compromised. "We recently learned that a third party had obtained access to a set of Tumblr user email addresses with salted and hashed passwords from early 2013, prior to the acquisition of Tumblr by Yahoo," Tumblr's May 12 security alert reads. "As soon as we became aware of this, our security team thoroughly investigated the matter. Our analysis gives us no reason to believe that this information was used to access Tumblr accounts. As a precaution, however, we will be requiring affected Tumblr users to set a new password."
The stolen Tumblr data is being offered for sale by a hacker known as Peace - also the seller behind the stolen LinkedIn, Fling and MySpace credentials - via the darknet marketplace The Real Deal, reports Motherboard. But the information is reportedly only being sold for about $150 in bitcoins, apparently thanks to Tumblr having "hashed" the passwords - which converts each one into an alphanumeric string - after having first "salted" them, which adds unique digits to each password, thus making them harder to crack.
 A hacker known as "Peace" has offered stolen Tumblr credentials for sale on the darknet marketplace known as The Real Deal.
A hacker known as "Peace" has offered stolen Tumblr credentials for sale on the darknet marketplace known as The Real Deal.
Tumblr's Password-Hash Fail
Tumblr hasn't disclosed which hashing algorithm it used. In theory, hashing will make passwords tougher to reverse engineer, provided the hashing is correctly implemented (see Researchers Crack 11 Million Ashley Madison Passwords).
But Hunt says that Tumblr used the SHA1 cryptographic hash function and estimates that at least half of its passwords being sold could be cracked.
If that's true, Tumblr's hashing practices weren't up to snuff. Indeed, security experts have long warned that SHA1 should never be used for passwords, and that only dedicated password hashes - such as mcrypt - be used instead (see LinkedIn's Password Fail). As a result, security experts warn that anyone who's reused their Tumblr password on other sites should change every password, preferably to something that's unique.
Spring Cleaning for Hackers
It's not clear what the impetus might be behind so many old breaches now coming to light, especially when the credentials are being offered for so little money. Perhaps it's just a bit of stolen-credential spring cleaning on the part of hackers such as Peace.
But the spate of newly discovered historical mega breaches is a reminder that some breaches may go undetected for years. Others, such as the LinkedIn breach - originally believed to encompass 6.5 million credentials - apparently can turn out to be much worse than anyone seems to have realized. And if the spate of recent breach revelations is any indication, there may be more bad news soon to come.
- Details
- Category: Security News
Breach Notification , Data Breach , Legislation
A Look at Breach Notification Laws Around the World As Europe Preps Mandatory Notifications, What's the Norm Elsewhere?
On the data breach front, a lot has changed since 2003.
See Also: Achieving Advanced Threat Resilience: Best Practices for Protection, Detection and Correction
That's when California began enforcing the world's first data breach notification law, known as S.B. 1386. The law requires organizations in both the public and private sector to notify any California resident if their unencrypted personal information gets exposed, inadvertently or otherwise.
Since then, breach notification laws have continued to spread, although notification is still not mandatory in most countries.
To take stock of the current state of nation's data breach notification requirements, my colleagues at Information Security Media Group and I have explored efforts in four regions:
Europe: The EU's General Data Protection Regulation, which goes into effect in May 2018, includes a number of privacy provisions, including mandatory breach notifications. Some legal experts say the regulation will serve as a model for other countries (see Mandatory Breach Notifications: Europe's Countdown Begins). United States: Some 47 states, three U.S. territories and Washington, D.C., have breach notification laws of varying strength. But efforts to replace them with a single - and more straightforward - federal law have stumbled, in part because previous efforts would have weakened some states' current approaches, Eric Chabrow reports (see Single U.S. Breach Notification Law: Stalled). Australia and New Zealand: Officials in both countries are reviewing mandatory breach notification proposals but have yet to pass any related laws, as Jeremy Kirk reports (see Australia, New Zealand Still Mulling Data Breach Laws). India: Lacking any mechanism for enforcing a data breach notification law, experts say it's unlikely the country will see any related laws anytime soon, Geetha Nandikotkur reports (see Why India is Still Not Ready for Breach, Privacy Laws).Today, nearly 90 countries have data protection laws - or relevant court rulings - on the books, ranging from Angola and Argentina to Venezuela and Zimbabwe, according to the law firm DLA Piper. But many of those countries still don't require breached organizations to notify either authorities or the individuals whose personal information was exposed in the event of a breach.
Data Breach Notification Upsides
Breach notification laws aren't a security panacea, but they do offer upsides:
Consumers get a heads-up that they're at increased risk of identity theft or fraud. Organizations that mishandle personally identifiable information can get named and shamed. Law enforcement agencies can better track attacks and allocate resources to help bust criminals who target, buy or sell PII.But sometimes when PII or emails and passwords get dumped online, the source isn't clear. Notifications are also contingent upon organizations discovering that they've been hacked and then understanding the full extent of the breach. As the 2012 LinkedIn hack demonstrates, the social network failed to spot that more than 160 million user credentials had been compromised until they showed up for sale on an underground forum four years later (see Troy Hunt: The Delicate Balance in Data Breach Reporting).
On the other hand, even some insight into current breaches, on a regional level, can help wake up consumers, legislators and regulators to the full extent of the problem. Until now, for example, only European ISPs and telecommunications firms have been required to report breaches to EU authorities.
"That's one thing that I often smile at, when I hear about Europeans going 'Oh, we must be more secure than U.S. companies because you never hear about data breaches in Europe," Dublin-based information security consultant Brian Honan tells me.
Come 2018, however, all EU organizations will be required to report breaches or risk massive fines. And when the law comes into effect, perceptions will change as the number of notifications rapidly piles up. "Just because you don't hear about it doesn't mean it's not happening," says Honan, who's also an adviser to the EU's law enforcement intelligence agency, Europol.
- Details
- Category: Security News

The theft of a backpack holding a laptop computer and paper documents containing medical information on perhaps thousands of National Football League players serves as a lesson in the importance of properly safeguarding health information, even for entities falling outside of HIPAA's reach.
See Also: The Inconvenient Truth About API Security
The theft, which the NFL now acknowledges, occurred in April when a car containing the backpack of a Washington Redskins athletic trainer was broken into in downtown Indianapolis, the news site Deadspin reports.
"The backpack contained a password- protected, but unencrypted, laptop that had copies of the medical exam results for NFL Combine attendees from 2004 until the present, as well as certain Redskins' player records," Deadspin reports, quoting an email reportedly sent on May 27 by NFL Players Association Executive Director DeMaurice Smith to each team's player representative. The players association is the union for pro football players.
The NFL Scouting Combine is a week-long event held each February in Indianapolis where college football players perform tests for NFL coaches and scouts. Many current players participated in the Combine.
The player's association email obtained by Deadspin also notes: "We have also been advised that the backpack contained a zip drive and certain hard copy records of NFL Combine medical examinations as well as portions of current Redskins' player medical records. It is our understanding that our electronic monitoring system prevented the downloading of any player medical records held by the team from the new EMR system.
The players association declined to comment to Information Security Media Group on the incident.
NFL Statement
But the NFL tells ISMG in a statement: "Once we became aware of the theft, we promptly worked with the club and the NFLPA to identify the scope of the issue. The club is taking all appropriate steps to notify any person whose information is potentially at risk. As the NFLPA memo confirms, the theft of data involves information maintained by one club and no information maintained by any club on the NFL electronic medical records system was compromised, and the theft is entirely unrelated to that system."
All NFL clubs have been directed to re-confirm that they have reviewed their internal data protection and privacy policies; that medical information is stored and transmitted on password-protected and encrypted devices; and that every person with access to medical information has reviewed and received training on the policies regarding the privacy and security of that information, according to the NFL statement.
In addition, the NFL notes, "We are aware of no evidence that the thief obtained access to any information on the computer that was stolen nor aware that any information was made public."
The Redskins organization says that "no Social Security numbers, protected health information under HIPAA, or financial information was stolen or are at risk of exposure," according to Deadspin, and the players association letter says it had "consulted" with the U.S. Department of Health and Human Services about the incident.
The team says it's also "taking steps to prevent future incidents of this nature, including encrypting all laptops issued to athletic trainers and other team personnel and through enhanced security training," Deadspin reports.
The Redskins did not immediately respond to a request for comment.
Regulatory Gap?
Even though health information was apparently involved, the NFL incident appears to be outside of HIPAA's regulatory range, security experts say.
"While the team's medical personnel likely qualify as healthcare providers, they and their records may not be subject to HIPAA if they do not electronically submit healthcare claims to health plans or otherwise electronically interact with insurers," says privacy attorney Adam Greene of the law firm Davis Wright Tremaine. "If HIPAA does not apply, certain state laws may nevertheless have required encryption of the data or breach notification of the theft."
Privacy attorney Kirk Nahra of the law firm Wiley Rein notes: "It is unlikely HIPAA is relevant. A football team isn't a covered healthcare provider, and I doubt this involved the team 'health plan,' certainly for players that are not on the team. So this is an issue of the HIPAA gaps, where HIPAA does not apply to all medical information but only to certain information in certain contexts when held by certain people," he adds.
David Holtzman, vice president of compliance at security consultancy CynergisTek, adds: "It is also unlikely that the league or the team is a business associate [under HIPAA] because they did not obtain, maintain or create the health information while performing a function or service to a HIPAA covered entity."
In a statement to ISMG, a spokeswoman for the HHS Office for Civil Rights, which enforces HIPAA, says: "In a circumstance where an NFL trainer meets the definition of a covered entity (i.e., bills payers/insurers for care using HIPAA standard transaction), the trainer would be required to comply with HIPAA. We do not know enough about the circumstances here to know whether the trainer was or was not a HIPAA covered entity."
Most states have laws that require protecting sensitive personal, financial or health information from unauthorized disclosure, Holtzman says. "Most state laws exempt reporting when the device on which the information is stored is encrypted. And many allow that notification is required only if the individual is put at risk of financial harm or identity theft."
Although the NFL likely doesn't face any HIPAA-enforcement actions, it could still face lawsuits as a result of the incident.
"The league and the NFL players union have stated that the keeping of the medical information about players and participants in the league combines without encryption was a violation of league rules," Holtzman says. "And, earlier this year Jason Pierre-Paul, a player for the New York Giants, filed a lawsuit against ESPN and one of their reporters for publishing online copies of medical records concerning treatment at a Miami hospital. Clearly, there is more to watch for concerning where and how any of the data in these health records show up."
Assessing Risk
Keith Fricke, principal consultant at consultancy tw-Security, says that having a laptop password-protected, but not encrypted, "gives a false sense of security" because passwords can be cracked or circumvented.
"It's akin to locking the windows and doors to a house, but thieves being able to peek through the window's transparent glass," he says. Encrypting the device helps "makes those windows opaque," he says.
Fricke urges all organizations - not just those covered by HIPAA - to encrypt mobile devices. "Err on the side of caution. Just because there isn't sensitive information on the device today, doesn't mean it won't be added by an employee later," he says.
"Encrypting laptops and other portable devices like USB drives or smartphones is a 'no-brainer,'" Holtzman says. "In each of the six years since the implementation of the HIPAA Breach Notification Rule, upwards of 60 percent of all reportable large breaches were the result of loss or theft of an unencrypted portable device or media on which PHI had been stored."
Old Data?
The NFL security incident, which involved data dating back as far as 2004, also serves as a reminder for organizations to dust off their data retention policies and procedures.
"Why would 10-year-old medical information about players, most of whom are not on your team, ever still be retained on a laptop like this?" Nahra asks. "It may not be a legal issue, but it certainly raises this data management question for any kind of business entity."
Fricke suggests that organizations periodically assess data contained on mobile devices. "If you don't need to have the data there, then archive it and pull it up when needed, in case there's ever an adverse event, like the device getting lost or stolen," he says.
- Details
- Category: Security News

A House committee is seeking answers from the Federal Reserve Bank of New York about the recent $81 million SWIFT-related theft from the central bank of Bangladesh and its implications for U.S. financial services firms.
See Also: Data Center Security Study - The Results
The House Committee on Science, Space and Technology launched its probe after warnings from SWIFT that the heist from Bangladesh Bank's New York Fed account and related malware attacks were "part of a wider and highly adaptive campaign targeting banks," which may have targeted a dozen or more institutions (see 5 SWIFT Cyber Heist Investigations).
"This is deeply troubling and it is Congress' responsibility to ensure, through its oversight, that the NY Fed is taking all precautions to protect American finances and aggressively execute its own role as overseer of SWIFT," reads a May 31 letter to William C. Dudley, president of the New York Fed Reserve, signed by Lamar Smith, R-Texas, committee chairman, as well as committee member Barry Loudermilk, R-Ga.
SWIFT, formally known as the Society for Worldwide Interbank Financial Telecommunication, is a cooperative owned by 3,000 banks that bills itself as "the world's leading provider of secure financial messaging services." It's now used by 11,000 banks globally to daily process 25 million communications that collectively account for billions of dollars' worth of transfers.
But the security of that messaging system has been called into question following a series of reports that malware-using attackers have been injecting fraudulent messages into the SWIFT network as part of a campaign that may stretch back to at least 2013.
"We are writing to request a briefing and information related to the February incident as well as information related to the NY Fed's role in overseeing ... SWIFT," the House committee's letter reads. The deadline for the Fed to respond and brief the committee is June 14.
As the letter suggests, the central banks of the 11 countries that comprise the G10 - Belgium, Canada, France, Germany, Italy, Japan, the Netherlands, Sweden, Switzerland, the United Kingdom and the United States - together oversee SWIFT, with the National Bank of Belgium taking the lead role.
Probing SWIFT-Related Weaknesses
Other legislators and regulators also have been asking SWIFT-related questions.
On March 22, Rep. Carolyn B. Maloney, D-N.Y., wrote to the New York Fed seeking further details on the Bangladesh Bank heist, to which the Fed responded on April 14.
Also in April, Britain's central bank, the Bank of England, wrote to all U.K. banks seeking details of how they were responding to risks related to the SWIFT network.
On May 19, Sen. Tom Carper, D-Del., the ranking Democrat on the Senate Homeland Security and Governmental Affairs Committee, also wrote to Dudley at the New York Fed, asking how the Fed was responding to the bank heists.
On May 23, meanwhile, Maloney wrote to Fed Chair Janet Yellen, Comptroller of the Currency Thomas Curry and Federal Deposit Insurance Corp. Chairman Martin Gruenberg, asking if they planned to follow the Bank of England's lead and order all U.S. banks to conduct a full cybersecurity review.
War of Words
The Bangladesh Bank heist, which came to light in March, initially triggered a war of words, with Bangladeshi officials accusing SWIFT and the New York Fed of sharing in the blame for the heist by failing to spot and stop the fraudulent transfers. But the New York Fed fired back, saying that the transfer requests had been valid, and so they had been honored, per existing agreements. SWIFT, meanwhile, accused Bangladesh Bank of having substandard security practices, including weak passwords and nonexistent firewalls on systems that it used to interface with the SWIFT network (see SWIFT to Banks: Get Your Security Act Together).
On May 10, officials from Bangladesh Bank, SWIFT and the New York Fed met and then released a joint statement pledging to work more closely together. "The parties also agreed to pursue jointly certain common goals: to recover the entire proceeds of the fraud and bring the perpetrators to justice, and protect the global financial system from these types of attacks," they said.
The House Committee on Science, Space and Technology has also requested an update on the status of those initiatives as well as details of "any remedial steps" that the Fed has taken to address vulnerabilities related to using the SWIFT network.
Meanwhile, after initially blaming the breaches on banks, SWIFT has changed its tune and released a five-point security improvement plan, which includes better support for banks' information sharing and fraud-detection efforts. But no aspect of that plan, or related information sharing, will be mandatory.
SWIFT has also promised to issue more detailed security guidance to users.
Should SWIFT Cover Losses?
Some security experts, however, say SWIFT must do more, such as requiring banks to comply with new industry security regulations and external audits (see Blocking Hack Attacks: SWIFT Must Do More).
In a May 24 statement, Gottfried Leibbrandt, SWIFT's CEO, dismissed such proposals: "SWIFT is not all-powerful, we are not a regulator, and we are not a policeman; success here depends on all the stakeholders in and around the industry."
If investigators uncover more hack attacks and fraudulent SWIFT money-moving messages, however, or such attacks worsen, SWIFT may be forced to take stronger steps or risk further damage to its reputation.
Ricardo Villadiego, CEO of anti-fraud firm Easy Solutions, says it's useful to contrast SWIFT's response to hacked customers, versus how banks respond to their hacked customers. "From the SWIFT CEO's point of view, he is accurate when he is saying the SWIFT network wasn't compromised," Villadiego says. "That is true. But now what is also true is that if you compare this with traditional phishing attacks, the banks' systems weren't compromised, but the money was stolen from users."
In such cases, most banks promise to cover customers' losses. For example, Lloyds Bank, a British retail and commercial bank, offers the following online and mobile banking guarantee: "We guarantee to refund your money in the unlikely event you experience fraud with our Internet Banking service - as long as you've been careful, for example, by taking reasonable steps to keep your security information safe."
"It would be nice to see the same reaction from SWIFT here," Villadiego says.
- Details
- Category: Security News
Anti-Fraud , Anti-Malware , Fraud
$25 Million in Losses Tied to 'Lurk' Malware-Using Cybercriminals Russia's Federal Security Service (FSB)
Russia's Federal Security Service (FSB)Russian authorities have arrested about 50 people in connection with an ongoing investigation into a hacker group that's suspected of unleashing malware-enabled hack attacks against customers of major Russian financial institutions.
See Also: 2016 Enterprise Security Study - the Results
The gang allegedly stole 1.7 billion rubles ($25.5 million) from accounts at multiple Russian financial services firms over a five-year period, Russia's federal security service, known as the FSB, says in a June 1 statement. It adds that Sberbank - the largest bank in Russia and Eastern Europe - assisted with its investigation, but didn't name any of the other victim banks.
The gang had attempted to steal a further 2.3 billion rubles ($34 million) by issuing false payment instructions, which were blocked, Russia's Interior Ministry tells Reuters.
The FSB, which is the successor to the Soviet KGB, says it made related arrests - supported by Interior Ministry and National Guard troops - in 15 regions across Russia.
"As a result of [house] searches a large quantity of computer equipment was confiscated along with communications gear, bank cards in false names and also financial documents and significant amounts of cash confirming the illegal nature of their activity," the FSB says.
All of the suspects have been charged with activities related to developing, distributing and using malware. After the raids, 18 primary suspects were denied bail, while three were placed under house arrest, according to the FSB.
Security experts say the malware used by attackers, called Lurk, was previously used primarily for click fraud, which refers to the practice of generating fake clicks on advertisements to illegally generate profits for website operators. But Moscow-based security firm Kaspersky Lab, which shared related intelligence with Russian banks and law enforcement agencies, says that 18 months ago, Lurk began to be deployed to assist in attacks against Russian banks, with attackers attempting to disguise their identity by using compromised VPN services.
"We realized early on that Lurk was a group of Russian hackers," says Ruslan Stoyanov, head of computer incidents investigation at Kaspersky Lab, in a statement. "Our company's experts analyzed the malicious software and identified the hacker's network of computers and servers. Armed with that knowledge, the Russian police could identify suspects and gather evidence of the crimes that had been committed."
Hackers Pummel Russian Banks
An unnamed source with knowledge of the investigation tells Russian news agency TASS that in March and April alone, six Russian banks - including Metallinvestbank, Metropol, Regnum and Russian International Bank - fell victim to related cyber attacks, and that Metallinvestbank alone lost 680 million rubles ($10.2 million).
As this week's arrests demonstrate, Russian authorities do target Russian residents who attack domestic targets (see Russian Cybercrime Rule No. 1: Don't Hack Russians). But in the past, gaining convictions has been difficult because under Russian law, investigators must prove that any cybercrime was accompanied by monetary theft from Russian organizations or individuals, according to Sergey Nikitin, deputy head of the computer forensics laboratory and malicious code analysis team at Moscow-based cybersecurity firm Group-IB (see Russia: 7-Year Sentence for Blackhole Mastermind).
The Malware
The Lurk malware used in the alleged cybercrime spree is primarily designed to infect systems and then download further malware, in part by using digital steganography, which refers in this case to hiding malware inside image files, according to Dell SecureWorks.
But that isn't the only type of malware being used to target Russian banks. This week, security firm Zscaler published a report on Android malware that's disguised as the official Sherbank mobile banking app. A Kaspersky Lab spokeswoman tells Information Security Media Group that the app isn't connected to the Lurk gang.
Regardless, the app demonstrates one way that hackers have been tricking banking customers into revealing their access credentials, thus allowing attackers to drain their accounts.
Zscaler doesn't detail how the Trojan app has been distributed, and notes that the Sherbank app currently available from Google Play is legitimate. But if a user installs the Trojan version on their device, the malware requests administrator privileges which "can cause devastating effects to the victim's device" if allowed, Shivang Desai, a security researcher at Zscaler, says in a blog post. Those abilities include intercepting SMS messages - which could be used to grab the one-time codes banks send to authorize transactions, especially for attacker-initiated money transfers - as well as the ability to call any number, which attackers could use to generate illegal profits by calling expensive toll numbers that they also control.
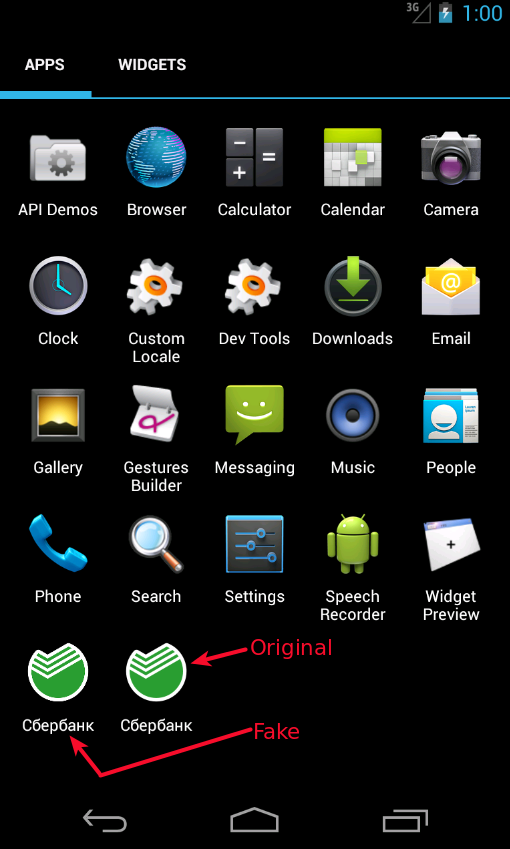 Attackers disguised their malware to look like Sberbank's Android app. (Source: zScaler)
Attackers disguised their malware to look like Sberbank's Android app. (Source: zScaler)Desai says the malware is also designed to present a fake log-in screen and steal credentials whenever users start up the Whatsapp app, Google Play Store, or the VTB 24 app, which provides access to accounts at Russian banking giant VTB. After the malicious app gets installed, it also suppresses all access to the legitimate apps.
"Even if the victim tries to access the original app, the malware will forcefully present its own fake login screen to the victim," he says, and after anyone provides their log-in credentials, they get sent to the attackers' command-and-control server.
Deleting the app can be difficult, short of wiping a device and reinstalling core software. "The malware has a very clever approach to remain persistent," Desai says. "It registers a broadcast receiver that triggers whenever the victim tries to remove administrator rights of the malware app, locking the Android device for a few seconds. As a result, it is not possible to uninstall this malicious app by revoking admin rights."
More Articles …
Page 3438 of 3546
