- Details
- Category: Security News
Compliance , Fraud , Payments Fraud
Why PCI Security Standard Adoption Is Growing in Europe Banking Deregulation, New Breach Notification Rules Drive Uptake
While the Payment Card Industry Data Security Standard gets credit for helping to push U.S. retailers to improve card data security, it's also had a big impact in Europe.
See Also: Unlocking Software Innovation with Secure Data as a Service
"There's a lot more e-commerce maturity in the U.K. than we see in the U.S., and also the chip-and-PIN infrastructure that's been deployed ... in Europe," says Andrew Barratt, the international managing director for Coalfire Systems, which provides compliance services, including PCI auditing. That maturity, however, "doesn't remove the need to protect the card data," he adds, as well as to comply with PCI.
This year marks the 10th anniversary of the launch of the PCI Security Standards Council, which has been instrumental in driving adoption of the PCI DSS, which was first introduced in 2004 (see PCI Turns 10: Will It Last Another 10 Years?).
In the past 10 years, PCI DSS has become a widely used standard throughout Europe. All of the card brands in Europe - Visa and MasterCard dominate, while American Express is up and coming - strongly push PCI, Barratt says. Furthermore, PCI has always been taken quite seriously in the U.K., Germany and France, Barratt contends.
But just as in the United States, not all European organizations that process payment card data understand their PCI compliance responsibilities, says information security consultant Brian Honan, who heads Dublin-based BH Consulting and founded Ireland's first computer emergency response team.
"Very often, many think that PCI only applies to them if they process the credit cards via their website," he tells me. "They are not aware they are obliged to comply with PCI DSS even if they outsource the processing of credit cards to third parties, if they accept credit card payments over the phone, or even in person. So there is still a lot of work to be done to make companies become more aware of their responsibilities and obligations when accepting credit cards."
Deregulation Drives Uptake
Now, however, in more countries in Europe, especially Spain, "some of the big acquiring banks are really starting to push the market for [PCI] compliance, because they're concerned about the risk of fraud, as much as anything," Barratt tells me.
That push is the result of many European countries deregulating their banking industries by jettisoning onerous rules, as well as interbank or cross-border money-moving fees, all of which has opened up their markets to competition. Many service providers as well as acquiring banks - which process payment card transactions on behalf of merchants - use PCI compliance as a competitive advantage, Barratt says. For example, they use compliance to demonstrate their suitability for operating in new markets. In addition, acquiring banks typically contractually enforce PCI compliance on merchants as a fraud-prevention measure, he says.
Future Relevance
PCI, of course, is a global standard, but Barratt says recent updates will be especially applicable to European security practices. That includes PCI recently updating its ecommerce guidance in light of recent attacks. As European organizations increasingly implement point-to-point encryption and tokenization, he says, PCI standards will also help shape related decisions.
Barratt says upcoming PCI guidance relating to telephony-based payments, including alternative ways to handle payment card data over the phone, should help merchants in Europe and beyond that are in pursuit of an "omni-channel payments system." That's an industry buzzword referring to having one all-encompassing payments infrastructure that covers all payment channels.
EU Breach Notifications: PCI Impact
Under the EU's new General Data Protection Regulation, which will be enforced beginning in 2018, organizations that do business with Europeans will also be legally required to inform consumers when their personal data get exposed. "Should that breach impact credit card data, which would be deemed personal data under GDPR, then the company will have to notify the authorities of the breach," Honan says.
That's a first for Europe, and the increased breach transparency will likely "focus the mind of consumers, regulators and inevitably companies" on acceptable cybersecurity practices - including demonstrating PCI compliance, he says.
- Details
- Category: Security News
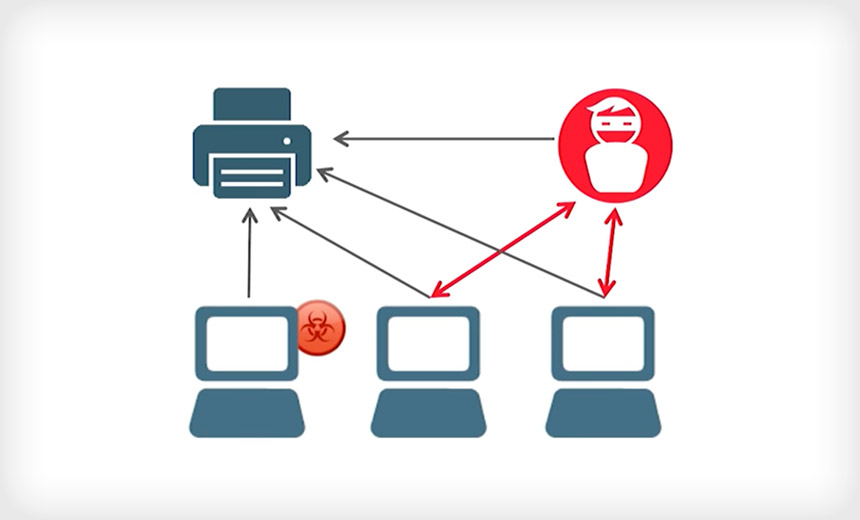 Beware malicious printer drivers. (Source: Vectra Networks)
Beware malicious printer drivers. (Source: Vectra Networks)On July 12, Microsoft issued a patch (MS16-087) that shows the dangerous trade-off sometimes made between security and convenience. It's an attack so devilishly smooth that it's a wonder hackers had not figured it out before.
See Also: From Authentication to Advanced Attack Vectors: Top Trends in Cybercrime in Q1 2016
The finding comes from Vectra Networks, which decided to test if it was possible to deliver malware from a nearby printer to a Windows machine. The attack relies on a protocol called Microsoft Web Point-and-Print, which the company incorporated into Windows to make it easy to connect to a printer.
It's impractical for administrators to have to install a variety of printer drivers for every machine they manage. The Microsoft Web Point-and-Print protocol, introduced around 2007, is designed to deliver a driver for whatever printer that is nearby.
A printer driver is given a free pass: it's not subject to User Account Control, or UAC, which warns users before installing new software. That was a decision by Microsoft to make the process of getting ready to print easier. Also, a driver's digital signature - used to verify if software is legitimate - isn't checked. The driver gets installed straight away with high privileges at the system level.
To test the theory, Vectra Networks found a bug in printer software that allowed them to insert malicious code into a driver. In a demo video, Vectra shows the malicious driver was accepted by the Windows machine and granted the attacker a command-line shell. What's worse, even if the malware is removed, any time a user is close to the same printer, it would be delivered seamlessly again. Vectra says it turned the printer into "internal drive-by exploit kit."
The driver issue is less of a coding mistake than a design or logic bug, says Nicolas Beauchesne, senior security researcher with Vectra. It probably escaped attention sooner because there are fewer tools to detect logic bugs compared to implementation flaws, he says.
"As we improve prevention technology and logic analysis tools, we might expect to find that there are many more logic bugs then we expected, and we may also find that these have been lurking for years," Beauchesne says.
And it may have not been such a secret. "I believe that if a security vendor can think about this angle and find an exploit, an attacker would have thought about it before as well," says Chris Goettl, a program product manager for LANDESK Software.
Long-Term Problem?
Vectra Networks is reverse engineering Microsoft's patch to figure out if this kind of attack will be a long-term problem. But the fix also depends, in part, on the cooperation of printer manufacturers.
"Microsoft is pretty much between a rock and a hard place," Beauchesne says. "Printer vendors have yet to agree on a printing standard or, in some cases, to even sign their drivers. Ensuring that every driver is signed would break older printers until their respective vendors deploy new drivers for all their models."
There are a couple of small barriers to this kind of attack. In Vectra's first example, attackers would have to find a vulnerability in printer software in order to insert malicious code. That's not terribly difficult, however. They would also have to tamper with a printer that is already inside an organization or spoof a device that appears on the network to be a printer, which would also require inside access.
But Vectra found a much more dangerous possibility: an attack delivered over the web. That style of attack could deliver a malicious driver through a compromised web page or even a malicious advertisement. A web attack could be executed using either Web Point-and-Print or the Internet Printing Protocol, which is a set of standards for printing first developed by Novell and Xerox in 1996.
There is a saving grace: Aside from Microsoft's fix, it's possible to control Web Point-and-Print through group policy settings, including just simply turning it off. That would probably irritate users, but at minimum, it would prevent this style of attack. Pick your poison: a gander of users who can't print from some obscure early 2000s printer in the basement, or explaining to the CIO why data has gone walkabout.
- Details
- Category: Security News

A former St. Louis Cardinals scouting director has been sentenced to 46 months in federal prison for illegally peeking at a player-drafting database for the Houston Astros - a hefty term for a distinctly unique hacking case.
See Also: 2016 State of Threat Intelligence Study
Christopher Correa, 36, was accused of illegally accessing Ground Control, a cloud-based database that held the Houston team's most critical observations on potential players, and an Astros email account. He pleaded guilty in January in federal court in Houston to five counts of unauthorized access to a protected computer.
The case is unique because of the stiff sentence Correa received. It is also likely the first ever cyber espionage prosecution relating to sports, says Edward McAndrew, a former federal cybercrime prosecutor and now partner with law firm Ballard Spahr.
"To see [cyberespionage] between two professional sports franchises in a way that was meant to enable one to get a competitive advantage is unparalleled in terms of its prosecution," McAndrew says.
The case also highlights serious errors made by the Houston Astros in managing Ground Control, which was breached by separate attackers while Correa was snooping for player scoops.
Harsh Sentence?
A first-time cyber offender, Correa faced up to five years in prison on each count. Federal judges rarely stack counts when sentencing, so the effectual maximum that Correa could have faced was 60 months. His 46-month sentence is "significant" and shows intent by the judge to deter others, McAndrew says.
Defendants have typically received much lower sentences in similar cases, indicating U.S. District Judge Lynn N. Hughes aimed for a deterrent effect, McAndrew says.
"Sending a message is, in fact, something that judges are supposed to consider when they impose criminal sentences," McAndrew says. "And because of the very unique nature of this particular crime and this particular sentence, I think the judge was certainly doing that here."
Correa was also ordered to pay the Astros $279,038 in restitution. The team lost an estimated $1.7 million as a result of the intrusions.
Correa received a slightly shorter sentence than that of Su Bin, a 51-year-old Chinese businessman who pleaded guilty to conspiring to hack the computer networks of U.S. defense contractors, including Boeing. Bin was sentenced on July 14 to 48 months in federal prison and fined $10,000, according to Reuters.
"If one wanted to heckle this - while Mr. Correa's plea bargain is within the ballpark - one would say he should get more than a two-month discount off of a military-style hack," says Ira Rothken, a technology attorney based in Novato, Calif.
Ground Control
The Houston Astros set up Ground Control in 2012 as part of a move away from pen-and-paper notes. But the team struck out due to poor information security practices.
Ground Control was a password-protected, internet-facing web service containing detailed notes on players that the Astros was scouting, which could have given clues as to which players the team might draft.
Correa, the Cardinals' director of baseball development, in December 2011 was given a laptop of a team employee who moved to the Astros. That employee, referred to as Victim A, also turned over his password to Correa, according to a court document.
Victim A then used a similar password for his Astros email and Ground Control accounts. Correa discovered the variation and accessed both accounts.
In a January hearing, Assistant U.S. Attorney Michael Chu described Victim A's password as "based on the name of a player who was scrawny and who would not have been thought of to succeed in the major leagues, but through effort and determination he succeeded anyway."
"So this user of the password just liked that name, so he just kept on using that name over the years," Chu said, according to a court transcript.
Scouting for Data
In his first intrusion in March 2013, Correa downloaded an Excel file that contained the Astros' scouting list and how the players were ranked.
Three months later, he accessed Victim A's Ground Control account, filtering results to only show players that the Astros were considering who had not been drafted yet.
As Correa was poking around, the Astros faced a larger problem. In March 2014, the Houston Chronicle ran an in-depth story about Ground Control, and unknown attackers accessed the database. The team then changed the database's website address, and Ground Control users were also prompted to change their passwords.
That's when the Astros made a critical mistake. Fearing that some users would not change their passwords fast enough, it reset all Ground Control accounts to a single default password and then emailed that password to all users.
Correa kept his access, as he knew the new URL for Ground Control and saw the default password emailed to Victim A. He then used the default password to open the Ground Control account for Victim B.
The bungled security refresh by the Astros, which came too late, proved to be costly. In June 2014, about 10 months' worth of information from Ground Control was leaked online, Deadspin reported at the time. The Astros undertook a security review, and Major League Baseball contacted the FBI.
When he pleaded guilty on Jan. 8, Correa admitted to the breach, saying that he "trespassed the Astros' resources based on suspicions that they had misappropriated proprietary work from myself and my colleagues."
Judge Hughes then asked Correa, "So you broke in their house to find out if they were stealing your stuff?"
"Stupid, I know," Correa responded.
- Details
- Category: Security News
Governance , Incident Response
Video Interview: Attorney Randy Sabett on Importance of Incident Response Plans Randy Sabett, special counsel, Cooley LLPBecause more federal regulators are paying closer attention to how businesses are protecting consumer information, having a detailed incident response plan is more important than ever, says Randy Sabett, special counsel at law firm Cooley LLP in Washington.
See Also: 2016 Enterprise Security Study - the Results
The Federal Trade Commission, the Securities and Exchange Commission and the Federal Communications Commission are all paying closer attention to consumer protection and privacy risks that surface in the wake of a data breach, Sabett says in an interview with Information Security Media Group.
"I think it's really an extension of what the FTC started several years ago," Sabett says in this video interview with Information Security Media Group. "Now we're seeing, because these various other agencies, in some way shape or form, touch or have jurisdiction over some aspect of personal information, they're all getting involved. ... They're looking at the breach side of it and going after companies in very much the same way the FTC has done over the years."
Having an incident response plan in place, as well as having the right people within the organization prepared to respond, can help reduce fines that regulators could impose after a breach, he says.
In this interview at ISMG's recent Boston Fraud and Breach Prevention Summit, Sabett also discusses:
How the SEC and FCC are following the FTC's lead in post-breach actions; Why regulators are increasingly staking their claims on jurisdiction in the wake of a breach; and How federal action is influencing the roles state attorneys general play in fining organizations that expose personal information about consumers.Sabett is vice chairman of the privacy and data protection practice group at Cooley LLP. A former National Security Agency crypto-engineer, Sabett's practice focuses on data security, privacy, licensing and intellectual property. He has managed numerous data breach incident responses involving major retailers, financial and healthcare organizations, and online service providers. He served on the Commission on Cybersecurity for the 44th Presidency.
- Details
- Category: Security News
Fraud , Payments , Payments Fraud
Video Interview: Marianne Crowe of Boston Fed on Sticking with Long-Term GoalsThe Federal Reserve's strategy for oversight of the U.S. migration toward faster payments won't change in the wake of the heists that exploited international SWIFT payments, says Marianne Crowe of the Fed in Boston. That's because the long-term security of U.S. payments has always been a priority for the Fed in its study of faster payments, she says (see Will Faster Payments Mean Faster Fraud?).
See Also: Unlocking Software Innovation with Secure Data as a Service
"Using situations like SWIFT and others - those are good examples of lessons learned that we can evaluate and take a look at," Crowe says in this video interview with Information Security Media Group. "At the same time, the Fed has always been actively involved in various initiatives in the payments system, through ACH, through check. And with faster payments, [the Fed's Faster Payments Task Force] is on a course now to do that evaluation - to evaluate the different criteria for the right solutions for faster payments, from a security perspective as well as payment efficiency. ... So I don't think anything's changing as they continue to go forward."
In this interview at ISMG's recent Boston Fraud and Breach Prevention Summit, Crowe also discusses:
How the Fed's task forces are dedicated to faster and more secure payments are working together; Four key areas being evaluated to ensure the long-term security of payments in the U.S.; and The ongoing role the Fed will play in evaluating proposals for faster payments technologies and systems in the U.S.;Crowe serves as vice president of payment strategies at the Federal Reserve Bank of Boston, where she oversees industry analysis and applied research on digital and mobile retail payments, standards and security initiatives. She leads the Mobile Payments Industry Workgroup, which represents mobile payment stakeholders focused on eliminating barriers to successful adoption of mobile and digital retail payments in the U.S. She also is a payments liaison with the Federal Reserve's Secure Payments Taskforce. She joined the Fed in 2001.
More Articles …
Page 3464 of 3546

 Randy Sabett, special counsel, Cooley LLP
Randy Sabett, special counsel, Cooley LLP
