- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In Development
Receive Invite When Available
- Details
- Category: Security News
In the wake of the controversy over Hillary Clinton's use of private email servers, President Obama voices his concerns about the state of federal government IT security in this edition of the ISMG Security Report.
You'll also hear:
The ISMG Security Report appears on this and other ISMG websites on Tuesdays and Fridays. Be sure to check out our July 5 and July 8 reports, which respectively analyze the latest victim of hackers making fraudulent SWIFT transfers and the fierce battle between endpoint protection product makers. The next ISMG Security Report will be posted Friday, July 15.
Theme music for the ISMG Security Report by Ithaca Audio under Creative Commons license.
- Details
- Category: Security News
Messaging , Risk Management , Technology
Commenters Weigh In on Clinton's Email Practices Interview Creates Lively Debate on Security vs. Convenience
Those commenting on my recent interview with Purdue University Computer Science Professor Eugene Spafford about Hillary Clinton's email server controversy are divided over whether users will devise ways to circumvent systems safeguards to do their jobs more effectively.
See Also: 2016 Enterprise Security Study - the Results
"Where security policy isn't in sync with the way people work, policy workarounds and 'exceptions' become the rule," Scott Petry, CEO and co-founder of Authentic8, a provider of secure browsing, writes in the podcast's comments section.
But a commenter identified as DJL - David J. Lineman, president of information security and data privacy products and services provider Information Shield - writes that convenience "is an extremely weak justification for a major violation of security policy. You can be sure that if the CSO of a Fortune 100 company had a personal server in her basement that stored trade secrets, and there was a known breach, she would be terminated."
 Hillary Clinton checks her email.
Hillary Clinton checks her email.Clinton, the presumptive Democratic Party nominee for president, used private email servers while serving as secretary of state. An FBI investigation found that Clinton, despite her denial, knowingly used the private servers to transmit a few messages marked classified. But the Justice Department declined to prosecute, which dismayed many of her political critics.
Spafford, in the interview, lamented that the debate surrounding the use of private email servers concentrated on politics and failed to focus on why such things happen. "I think this is more politically driven than it's functionally driven because if it were functionally driven, people would say, 'What are the root causes, and how do we fix them?' rather than trying to assign blame."
Taking Risks for Expedience Sake
A commenter identified as Jennifer WhoDat Farwell, agrees, writing that it's irrelevant whether Clinton felt what she did was right or wrong. "Humans have such a high, innate risk tolerance that we will take all sorts of risks for the sake of expediency and achievement," Farwell writes. "That is how we got to the top of the food chain. Instead of debating whether she made a typical human error (which she did), let's have a productive conversation about using technology to help humans be more productive without engaging in risky behaviors we are not programmed to avoid."
 Eugene 'Spaf' Spafford
Eugene 'Spaf' SpaffordSpafford contends that security professionals should do more to create secure systems that can help individuals perform their jobs efficiently. It's a point picked up by Wendy M. Grossman, a journalist who previously blogged about this matter. "HRC had requested a secure Blackberry and been refused," Grossman writes in response to my interview. "I know security is important, but it's incredible to me that the security people apparently thought their ideas about technology should take precedence over what the U.S. secretary of state was telling them about her working needs. Collaboration with people who need to do their jobs needs to be a top priority in doing good security."
"Baloney," responds another commenter using the handle voice-of-experience. "Convenience nor ignorance had nothing to do with why this private server was setup. HRC did not want her emails to be discovered as they would expose her corrupt activities."
Commenter Ms NoWay Jose contends "we are heading down a slippery slope of failures" if we allow convenience to trump security. "Security is security; it's not like hundreds of millions of identities haven't been stolen worldwide. It's not like we don't have to worry about intelligence leaking because both of these are happening far too much from incompetence and security ignorance. Sorry, but the security of our national intelligence is far more important than the convenience of someone who doesn't want to follow the laws. If you can't handle the job, then get out."
State Department Inaction
One question that seems unanswered is why the higher-ups responsible for State Department IT security didn't put a stop to Clinton's use of private email servers if they posed a security risk. "Didn't her private email server have a different domain suffix than the usual State Department ones?" asks Patrice Boivin, CEO of Orion Software, a provider of software to the rental industry. "Why in the world didn't anyone notice this or do something about it is my question. Bureaucracies are full of organizational chart boxes where the people in the boxes are either incompetent, running amok, or not allowed to make the decisions that go with their job descriptions. Someone must have noticed; question is, why wasn't this nipped in the bud?"
Commenting on the blog's premise focusing on developing secure systems that also facilitate the work habits of users, Jay Wack writes: "The situation is all the more frustrating because there are solutions and standards available that satisfy all concerned from an ease of use perspective and from the security perspective. ANSI, a national peer review process, has published several standards directly applicable. X9.69 and X9.73 specifically. Designed for secure information sharing. A problem for all of us."
These are just a sampling of the many comments we received on my Spafford interview. It's not too late for you to join this discussion. Post your comments below.
- Details
- Category: Security News
Anti-Malware , Data Loss , Encryption
Ransomware Variant Deletes Everything 'Ranscam' Malware Pretends Bitcoin Ransom Will Recover Nuked Files
How low will ransomware go?
See Also: Creating a User-Centric Authentication and Identity Platform for the Healthcare Industry
Security researchers say there's been a flood of new malware variants reaching the market. Cybercriminals are eager to cash in on the profit potential afforded by ransomware - many targets are easy pickings. And the developers who create the malware are eager to turn a profit by selling their attack code to more would-be users.
Greater competition inevitably leads to "innovation," and in this case it almost always comes at the expense of victims' data.
You might think that encrypting a victim's files en masse, deleting the originals and then demanding bitcoins for the decryption key is bad enough. But don't forget cybercriminals targeting not just individuals but also organizations providing critical services, including healthcare facilities and the police. Another wrinkle, of course, is that even the most profit-oriented developer-cum-criminal may fumble their crypto, thus leaving files unrecoverable.
More recently, some ransomware developers have opted for shock value, such as a variant named Jigsaw that takes its inspiration from horror movie "Saw" and begins deleting a user's files while they watch.
What most ransomware victims would find truly evil, however, is malware that simply deleted all of their data, then pretended it was encrypted until victims paid the ransom.
Scam Ransomware Debuts
Enter Ranscam, which represents perhaps the most lazy - and crass - type of ransomware built to date, in that it seeks to cash in on ransomware fears while delivering nothing but scorched-earth tactics, according to Edmund Brumaghin and Warren Mercer of Cisco's Talos Security Intelligence and Research Group.
"It lacks complexity and also tries to use various scare tactics to entice the user to paying," such as informing users that their files have been moved to a "hidden, encrypted partition," and then displaying a ransom message that persists even after reboots, the researchers say in a blog post. The message also says that every time they click the payment link on the ransom note but don't pay, some of their files will get deleted, the post notes.
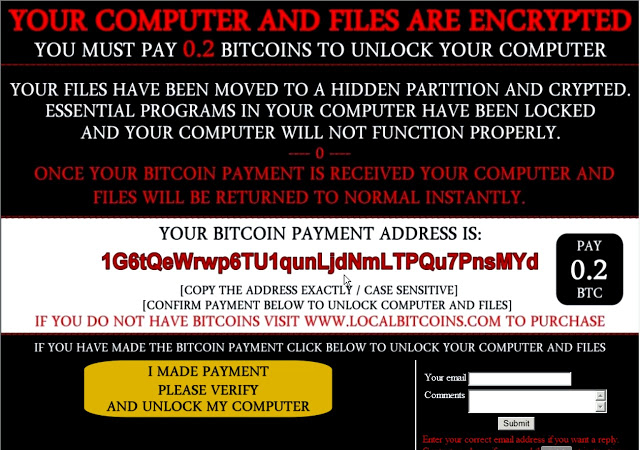 Ranscam promises to decrypt a locked PC in exchange for 0.2 bitcoins (about $135), but the supposedly encrypted files have already been deleted. (Source: Cisco Talos)
Ranscam promises to decrypt a locked PC in exchange for 0.2 bitcoins (about $135), but the supposedly encrypted files have already been deleted. (Source: Cisco Talos)
But that's a lie - the files are already gone, the researchers say, noting that the ransomware doesn't include any encryption or decryption capabilities. Instead, they say, the .NET executable malware is designed to use the Windows Command Processor to run a batch file that deletes the contents of designated folders - largely focused on user-generated content - as well as core Windows files that get used for restoring the system, shadow copies of files and registry keys associated with booting into safe code, among other files.
After that, the malware displays the ransom note, but by then it's too late. "The author is simply relying on 'smoke and mirrors' in an attempt to convince victims that their files can be recovered in hopes that they will choose to pay the ransom," the Talos researchers say. "The lack of any encryption - and decryption - within this malware suggests this adversary is looking to 'make a quick buck' - it is not sophisticated in any way."
It's not clear how widespread Ranscam might be, or how attackers have been sneaking it onto victim's computers. Also, it's not the first virus to outright delete data. But in recent years, such attacks have been relatively rare, aside from a handful of wiper malware attacks that targeted organizations in the Middle East or South Korea, plus the attack launched against Sony Pictures Entertainment in 2014.
7 Enterprise Ransomware Defenses
The takeaway from threats such as Ranscam - or any other malware that can wipe a hard drive - is simple: Preparation is everything (see No-Brainer Ransomware Defenses).
On that front, the U.S. Computer Emergency Response Team, which is part of the Department of Homeland Security, this week updated its recommendations for battling ransomware. In particular, US-CERT recommends:
Backups: Whitelisting applications: Updated operating systems and software: Anti-virus: Least privilege: Killing email-borne macros: Don't click:Simply keeping good backups would take a big bite out of ransomware attackers' profits. "Not only does having a good backup strategy in place help ensure that systems can be restored, it also ensures that attackers are no longer able to collect revenue that they can then reinvest into the future development of their criminal enterprise," the Cisco Talos researchers note (see Please Don't Pay Ransoms, FBI Urges).
More Articles …
Page 3462 of 3546
