- Details
- Category: Security News
Anti-Malware , Forensics , Technology
Attackers Can Hack Non-Jailbroken iOS Devices, Security Experts Warn
A complex - but practical - attack is being used to install malware on non-jailbroken Apple iOS devices, security experts warn.
See Also: Secure, Agile Mobile Banking: Keeping Pace with Last Best User Experience
Palo Alto Networks discovered the attack in the wild. It's being enabled by a Windows application called Aisi Helper, which tricks iOS devices into installing malware called AceDeceiver. Aisi Helper subverts a digital rights management feature called FairPlay that's built into iOS devices, while the malware itself is designed to upload infected devices' Apple ID and passwords to a command-and-control server.
Security researchers at Palo Alto Networks say Aisi Helper is marketed as a tool for installing pirated apps, and to date works only in China. But the technique used by Aisi Helper to bypass Apple's app review process and "walled garden" security model could be used by any malicious application running on a desktop to potentially install iOS apps "without the user's knowledge," Palo Alto researcher Claud Xiao contends in a blog post.
More Such Attacks to Come?
"If you are responsible for security in your organization, I suggest you familiarize yourself with this new form of Trojan as it is only a matter of time before further malware makes use of the same attack vector," Alan Woodward, a University of Surrey computer science professor, says in a blog.
Previously, attackers who wanted to exploit a non-jailbroken iOS device had to rely on digital certificates issued by an enterprise, which are used, for example, to allow mobile device management software to manage approved iOS devices that are allowed to connect to an enterprise's corporate network.
"What makes AceDeceiver different from previous iOS malware is that instead of abusing enterprise certificates - as some iOS malware has over the past two years - AceDeceiver manages to install itself without any enterprise certificate at all," Xiao says. "It does so by exploiting design flaws in Apple's DRM mechanism, and even [though] Apple has removed [apps containing] AceDeceiver from the App Store, it may still spread thanks to a novel attack vector."
The FairPlay Man-In-The-Middle Attack
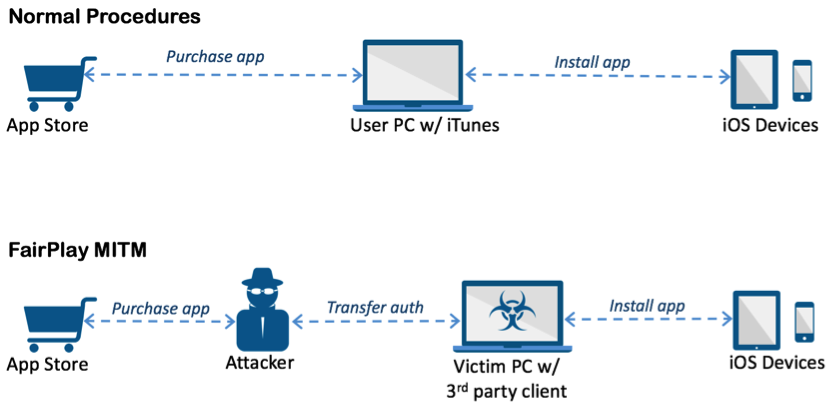 Source: Palo Alto Networks
Source: Palo Alto Networks
This attack vector centers on Apple's FairPlay DRM protection mechanism, which can be abused to trick any iOS into installing software, even if it hasn't been purchased from the App Store or signed using an enterprise digital certificate.
The FairPlay flaw isn't new. Indeed, man-in-the-middle attacks that targeted FairPlay - to spread pirated apps - were first seen in the wild in January 2013.
In August 2014, a team of Georgia Institute of Technology researchers described how the attacks worked and warned that the Apple DRM flaws could potentially be used to launch large-scale attacks against iOS devices. But so far, no such attacks apparently have occurred.
AceDeceiver Appeared in July 2015
The first AceDeceiver-infected app appeared on the Apple App Store in July 2015, Xiao says, although he declined to name the app. Subsequently, the AceDeceiver-infected "AS Wallpaper"- an app that gives users additional options for changing the background on their device - appeared on Apple's U.S. App Store in November 2015. A third infected app, called "i4picture," debuted on Apple's U.S. and U.K. App Stores on January 30, he adds.
Palo Alto says it discovered the malicious apps and warned Apple on February 24. It says Apple removed them from the App Store the next day.
Apple says it uses a code-review process, which it has never described in full, to look for signs of malicious code before it approves any app and allows it to be distributed via its official App Store. But whoever designed AceDeceiver and snuck three related apps onto the App Store obviously bypassed these checks.
"AceDeceiver's software got through Apple's review process by lying dormant inside what looked like a legitimate app," says digital forensic scientist Jonathan Ździarski, author of "iPhone Forensics," in a blog post. "It called home to a C2 [command-and-control] server to see if it should activate itself. After the app review process completed, it was signed by Apple, and could be turned on to do damage. At this point, it didn't matter that Apple removed it from the store - it was signed by Apple, and Apple can't revoke their own certificate."
Fortunately, at least for now, the risk from AceDeceiver is low, says threat-intelligence firm iSight Partners, because current versions of Aisi Helper are designed to only deploy the malware on iOS devices located inside mainland China. In the future, any "targeted individuals [would have to] have a Windows PC with the Apple App Store installed - which the malicious actor must compromise first - before infecting any attached iOS devices," it says. Even so, however, "due to the value of iOS security-defeating methods, we can expect the FairPlay Man-in-the-Middle technique to be reused in other malicious campaigns that may target victims outside China."
Apple declined to comment on these developments.
- Details
- Category: Security News
In the world of the extended enterprise, everybody seeks greater visibility into network activity. But Gidi Cohen was there in 2002, founding Skybox Security to provide analytics to improve cybersecurity. Cohen discusses the evolution of visibility.
"Skybox since its inception ... always focused on providing basic management tools to the CISOs and security teams," says Cohen, the CEO of Skybox. "We always believed one of the most elementary tools for any management in security specifically is getting visibility into whatever's going on. "
And with today's tools and the power of data analytics, this visibility translates into new ways to actually visualize one's security landscape.
One of today's key priorities is for security leaders to be able to visualize their attack surface across all of the multiple endpoints. "That might sound simple, but large enterprises or government agencies may have potentially millions of attack vectors," Cohen says. "So, the ability to distill [data] into simple visuals ... can bring great value to every CISO."
In an interview recorded at RSA Conference 2016, Cohen discusses:
The evolution of visibility tools; How this visibility enhances cybersecurity; Feedback from security leaders who have deployed these tools.Cohen co-founded Skybox in 2002 and has guided the company's vision and development as a leader in cybersecurity analytics. He is a frequent speaker at industry conferences worldwide, demonstrating how sophisticated analytics, modeling and simulation, as well as unprecedented network visibility can be used to reduce an enterprise's attack surface.
- Details
- Category: Security News
Cybersecurity , Data Breach , Risk Management
Congress Hears Testimony About Lack of Actuarial Data North Dakota Insurance Commissioner Adam Hamm testifies on cyber insurance before a House panel.
North Dakota Insurance Commissioner Adam Hamm testifies on cyber insurance before a House panel.A dearth of actuarial data stymies the growth of the cyber insurance market, industry experts told Congress at a March 22 hearing.
See Also: Unlocking Software Innovation with Secure Data as a Service
"Unlike fire insurance, [cyber] insurers do not have 100 years' worth of cyber loss data that they can use to build out new policies," Thomas Finan, a former Department of Homeland Security strategist who helped launch DHS's Cybersecurity Insurance Initiative, testified.
Finan, now chief strategy officer at Ark Network Security Solutions, and other witnesses testifying before the House Homeland Security Subcommittee on Cybersecurity, Infrastructure Protection and Security Technologies, called for the creation of a repository of cyber insurance data, including claim information and payouts, not only to support insurers creating cyber insurance policies but also to help enterprises gain a better understanding of the cyber risks they face.
Ex-DHS policymaker Thomas Finan discusses cyber insurance as a vehicle for helping corporate executives weigh risks.None of those testifying called for the federal government to run the repository, but some suggested the government could furnish funding and other resources, a point emphasized by the subcommittee's chairman. "I'm committed to ensuring that legislators help facilitate - but not mandate - solutions to better protect our private sector networks against cyber adversaries." said Rep. John Ratcliffe, R-Texas.
Repository of Cyber Data
Some of the experts see a repository as also providing a centralized platform to share the information that many companies retain about hacking activity. "Making this data available centrally can inform analysis of long-term trends for insight into the effectiveness of security practices," said Matthew McCabe, senior vice president of the insurance brokerage Marsh.
McCabe said carriers, their business customers and regulators could potentially use the data to analyze whether certain security protocols or practices have effectively mitigated cyber risks. The government and industry, he added, also could analyze whether organizations that have implemented cyber practices using the cybersecurity framework published by the National Institute of Standards and Technology have proven more resilient in withstanding cyberattacks.
In the wake of the recent passage of information sharing legislation, he said, government and industry could explore whether the greater availability of cyber threat indicators has enabled organizations to fend off malevolent actors.
Marsh's Matthew McCabe addresses the value of actuarial data and the culture of information sharing."The greater availability of cyber incident data to strengthen underwriting may also facilitate market forces to address current and future risks, and eventually encourage further carrier participation," McCabe said. "Better data could also enable the insurance industry to introduce solutions to close gaps in current coverages and to determine how to best detect and mitigate future incidents, or to reduce incident response times and facilitate recovery."
Pricing Cyber Insurance
Gathering the right data is critical in getting insurers to properly price cyber insurance policies. "If a product is priced too low, the insurer may not have the financial means to pay claims to the policyholder," said North Dakota Insurance Commissioner Adam Hamm, who testified on behalf of the National Association of Insurance Commissioners. "If too high, few businesses and consumers can afford to purchase it, instead opting to effectively self-insure for cyber incidents, limiting the ability of the insurance sector to be used as a driver of best practices."
Cyber insurance tends to be more customized and more expensive than other forms of insurance. Gathering and analyzing data about cyber incidents, some witnesses testified, could help carriers to standardize cyber policies they offer and, perhaps, bring down prices and extend coverage.
"Because this line of insurance is still in its infancy," Hamm said, "we're basically at a point where if you've seen one cybersecurity policy, you've seen one cybersecurity policy."
- Details
- Category: Security News
Encryption , Privacy , Technology
FBI Testing New Technique to Unlock Shooter's iPhone Apple CEO Tim Cook speaks March 21 at the company's Cupertino campus.
Apple CEO Tim Cook speaks March 21 at the company's Cupertino campus.This story has been updated.
See Also: Unite & Disrupt: Mitigate Attacks by Uniting Security Operations
The Department of Justice has been granted a delay of a March 22 hearing relating to a court order compelling Apple to help the FBI unlock the iPhone 5C issued to San Bernardino shooter Syed Rizwan Farook. That's because it says it may have found a way to unlock the phone without Apple's assistance (see Apple Accuses DOJ of Constitutional, Technical Ignorance).
On March 21, the U.S. government submitted a document to the court saying that "an outside party demonstrated to the FBI a possible method for unlocking Farook's iPhone," and that while testing was still required to ensure that it would work, if it did succeed then "it should eliminate the need for the assistance from Apple ... set forth in the ... [order] in this case."
Accordingly, the Justice Department filed a "motion to vacate" with the court, requesting that the March 22 hearing be delayed, in case the FBI can find another way to gain access to the iPhone. "The government proposes filing a status report with the court by April 5, 2016," the filing notes. That request was granted, with U.S. Magistrate Judge Sheri Pym canceling the hearing and ordering the Justice Department to "file a status report" by April 5.
Apple said it's premature to declare a victory in the dispute because it's possible authorities could come back in a few weeks and insist they still need help, according to the Associated Press.
Robert Cattanach, a former Justice Department attorney who handles cybersecurity cases for the law firm Dorsey & Whitney, told AP that the government would likely not have disclosed it had a lead unless it was almost certain the method would work. That's because the disclosure weakens the government's case by introducinng doubt that it could only access the phone with Apple's help, he said. "They've created ambiguity in a place where they've previously said there is none," he said.
Tim Cook on Protecting Privacy
The Justice Department's move followed Apple CEO Tim Cook taking to the stage March 21 at his company's Cupertino, Calif., campus to announce a range of new products, including a new iPhone and iPad. But first, he touched on the encryption debate "on everybody's mind," which kicked off after the FBI obtained the court order requiring Apple to help it unlock the iPhone 5C issued to the Faroook, the San Bernardino shooter (see Apple Accuses DOJ of Constitutional, Technical Ignorance).
"We need to decide, as a nation, how much power the government should have over our data and over our privacy," Cook said on stage. "We believe strongly that we have a responsibility to help you protect your data and protect your privacy. We owe it to our customers and we owe it to our country. This is an issue that affects all of us, and we will not shrink from our responsibility." (See Feds Counter Apple's Arguments Over iPhone 'Backdoor').
Farook's Dec. 2 workplace rampage, which the government has described as terrorism, left 14 people dead. Farook and his wife, Tashfeen Malik, were killed in a shootout with police. The bureau says it recovered Farook's phone from his car following the shootings.
While decrying the attacks, Cook vowed that Apple would fight the "dangerous" request, which he said was the equivalent of the FBI demanding that Apple "build a backdoor to the iPhone." And in Apple's latest legal filing, submitted to the court on March 15, the company's legal team has described the government's move as an attempt to "order private parties to do virtually anything the Justice Department and FBI can dream up," adding that "the [country's] founders would be appalled."
PR Campaign?
Regardless of the Justice Department's move to potentially withdraw the court order against Apple, some security and legal experts contend that the Justice Department had been running a carefully planned public relations campaign calculated to give the FBI the power to demand crypto backdoors from U.S. hardware and software manufacturers.
Information assurance consultant William Murray, for example, who's an associate professor at the U.S. Naval Postgraduate School, has criticized the Justice Department for the lack of "courtesy and respect" it has shown to Apple, in part by blindsiding the company with the court order (see Apple vs. FBI: Readers Debate).
"While government officials swear to uphold the Constitution, by design and intent, the Constitution limits their ability to 'govern.' It is to be expected that they will chafe under its restrictions. That is why we have courts and an adversarial system," he says. "Perhaps with the best motives and intent, and while perhaps within the limits of the Constitution and the law, the DoJ has gratuitously insulted and unnecessarily alarmed citizens."
Legal experts have said the case involving the court order against Apple might take several years - or more - to be resolved, unless of course, the Justice Department requests that Judge Pym withdraw her order against Apple.
Apple Pitches iPhone SE
Cook on March 21 announced Apple's forthcoming range of new products as the company battles a decline in worldwide iPhone sales. He announced that Apple would begin shipping later this month a new iPhone SE, which features a 4-inch screen and is meant to target customers who prefer a smaller and less expensive device.
As with all phones built since the iPhone 5S, the iPhone SE will also include the Touch ID fingerprint scanner, which is used to provide biometric access to the device, as well as to help create a unique, cryptographic key to secure data stored on the phone. That technology was not built into the iPhone 5C, and multiple information security experts have suggested that if it had been, then the late Farook's finger might have been used by the FBI to unlock the device.
Apple Patches 38 iOS Flaws
In other Apple security news, the company has released iOS 9.3, which patches 27 flaws in the 9.2.1 version of its mobile operating system. The new version also includes a fix for an iMessage encryption flaw discovered by a research team from Johns Hopkins University in Baltimore, led by cryptography professor Matthew E. Green. He and his team of graduate students have also published a paper that details a related attack in full.
The iMessage vulnerability, designated as CVE-2016-1788, could be abused by an attacker to obtain and decrypt any photos or videos sent using Apple's iMessage, the researchers say. "The attack is more interesting than just attachments and affected more than just iMessage," says Ian Miers, who was part of the research team, via Twitter. "Apple had to fix other apps, but won't say what."
Apple says that by targeting the vulnerability, "an attacker who is able to bypass Apple's certificate pinning, intercept TLS connections, inject messages and record encrypted attachment-type messages may be able to read attachments." Despite the dispassionate language and seeming caveats, however, multiple information security experts have labeled this vulnerability as posing a serious threat and warn that it can be exploited.
Green tells The Washington Post that his team's discovery of the Apple crypto flaw has direct and immediate implications for the Apple-FBI case.
"Even Apple, with all their skills - and they have terrific cryptographers - wasn't able to quite get this right," Green said. "So it scares me that we're having this conversation about adding back doors to encryption when we can't even get basic encryption right."
Really looking forward to iOS 9.3. You should all patch.
Apple: New Security Hire
In other developments, Apple has hired George Stathakopoulos, formerly of Amazon, as its new head of corporate information security, Reuters reports.
Stathakopoulos, who was Amazon's vice president of information security, also formerly served as Microsoft's general manager of product security. Apple, which didn't respond to a request for comment, hasn't officially confirmed Stathakopoulos's hiring. He reportedly began work at Apple earlier this month.
- Details
- Category: Security News
Compliance , Encryption , Fraud
European Card Payment Association Brings New Expertise, Perspective to Board Jeremy King, international director, PCI Security Standards Council
Jeremy King, international director, PCI Security Standards CouncilThe PCI Security Standards Council envisions PCI-DSS as a single, globally-unified data security standard. Now that the European Card Payment Association is a strategic regional member of the council, that goal is significantly closer, says Jeremy King, the council's international director.
See Also: Rethinking Endpoint Security
The PCI Council on March 22 formally announced its partnership with the ECPA, describing the pairing as "joining forces to protect against payment data theft around the world." What this means in practical terms is that the ECPA will now collaborate with the council's working groups and committees to help shape future versions of PCI-DSS, as well as to promote adoption of the standard to its members, in conformance with evolving European Union regulations.
For King, the added benefit is the influx of new technical expertise to help adapt to new payments platforms and to combat ever-shifting fraud schemes.
"What we're getting is expertise in organizations that have been using chip technology for the last 10 years," King says in an exclusive interview with Information Security Media Group. "So we're getting good cryptographers; we're getting good people who understand how payments work, how chip cards work, how contactless cards work. And so that is a fantastic technical resource that is coming into the council."
ISMG's Tom Field caught up with King at the end of the PCI Council's executive board meeting in Paris on March 17. In the interview, excerpted below, King talks about how this new strategic partnership will fuel global acceptance of PCI standards.
"One of the key things we always go on about is that our standards are global," King says. "And people say, 'Where is this global input?' Here it is."
Also in this interview, King discusses:
Fraud migration post-EMV in the U.S.; The evolving payments landscape; How the council will address security gaps at small-to-midsized merchants.King leads the PCI Security Standards Council's efforts to increase global adoption and awareness of PCI security standards. His responsibilities include gathering feedback from the merchant and vendor community, coordinating research and analysis of PCI-managed standards in European markets and driving educational efforts and council membership through involvement in local and regional events. He also serves as a resource for approved scanning vendors and qualified security assessors. Before joining the council, King was the vice president of the payment system integrity group at MasterCard Worldwide.
Significance of Partnership
TOM FIELD: The European Card Payment Association has now become a strategic regional member of the PCI Security Standards Council. What is the significance of this news?
JEREMY KING: This is a major achievement for both the council and for the ECPA. The ECPA is a relatively new organization made up of 13 European regional card associations. These are the local debit card issuers and schemes here in Europe, and essentially they've come together because within Europe we've got a lot of new European regulation that is coming through at the moment. We've also got the European Central Bank trying to simplify payments across the European payments area. So there was a need for all of the different European schemes to come together.
FIELD: How is this partnership going to help protect payment data?
KING: What we're getting actually is expertise in organizations that have been using chip technology for the last 10 years. So we're getting good cryptographers; we're getting good people who understand how payments work, how chip cards work, how contactless cards work. And so that is a fantastic technical resource that is coming into the council that isn't always readily available.
We also get their understanding of how the European field is playing and how the European regulation field is in coming into force. Also, we're then able to share our standards with each of these individual organizations. ... They can see that, yes, our standards are global. One of the key things we always go on about is our standards are global. And people say, "Where is this global input?" Here it is.
Assessing the Threat Landscape
FIELD: What are the payment security threats that give you the most concern?
KING: I think it is still in the card-not-present space. There are still too many organizations that don't realize - and this is something that we're trying to reiterate especially in the U.S., as they migrate to EMV - even within EMV transactions, the transaction is not encrypted. And so the key data elements around the expiry date and the cardholder name are in clear text. So although EMV is going to be a fantastic way to reduce face-to-face fraud, it's going to change the fraud pattern in the U.S.
We're trying to really make merchants and other organizations aware ... that the fraud is going to migrate to the card-not-present space. It's the biggest challenge, and everyone has to be aware of that, and everyone has to understand about securing data, but also even more so now it's about securing their organizations. It's understanding that the criminals can find one way into a network and then they're into your organization, and from there they can just find the data and steal it.
Getting Message to the Masses
FIELD: Do you find it's just the bigger organizations that are getting the message, or are you seeing the rank-and-file merchants starting to follow suit?
KING: The bigger organizations have been getting the message, and it was clear to us that we needed to work harder on the small merchant side. We've had a task force running for the last 18 months with the major task of "how can we simplify our information that we're providing to them?" Far too many times when I was talking to smaller merchants, they were just saying, "We don't understand how or what this language means. ..."
So we've been working on this, and hopefully by the end of May we are going to have some new guidance specifically for small merchants.
EMV Migration
FIELD: Let's talk about the EMV migration in the U.S. What progress are you seeing?
KING: I think the good news is that now we're seeing definite big improvements on the figures in terms of merchants that are EMV-enabled. ... I know there is a lot of feeling like this isn't going quickly enough, but it is a lot of work. It is not so much we can't get the cards out - we can. But it's just making sure that every merchant is set up correctly.
The other exciting thing with the EMV migration is that it is a technology enabler. Over here, especially in the UK, contactless cards are really taking off in the last year or so. Now to have the EMV contactless card, you need the EMV terminals. To have Apple Pay and Samsung Pay and Google Pay working at their best, you need the EMV terminals.
Merchants should be ensuring the new terminals that they are putting in place are contactless-enabled. So we're going to go not only with the EMV, but we're also going to get the benefits of contactless cards or fast tap-and-go payments. We were discussing about where payments are going to go next. We're all into the wearables. Is it going to be on my watch? Is it on a Fitbit? Is it on a token? All of this needs the fast payment infrastructure to be in place, and this is what's coming.
Now ... the U.S. is going from a new position, they're getting all of the latest technology. So they're going to be at the very latest, most secure place. Some of our technology over here has been around for up to five, 10 years. So, if I'm an international criminal, I just look for which is the weakest security. Is the weakest security in the future going to be in the U.S.? Maybe not. Will it be easy to hack into an older system in the U.K.? Maybe so.
More Articles …
Page 3400 of 3546
