 Photo: Clive Darra (Flickr/CC)
Photo: Clive Darra (Flickr/CC)Coming soon to an internet service provider near you: routers infected by internet-of-things botnet-building malware such as Mirai (see Can't Stop the Mirai Malware).
See Also: Fencing an Imaginary Yard; How to Secure your IP with an Unidentifiable Network Perimeter
One of the latest victims is London-based TalkTalk, or, to be precise, many of its broadband customers who were issued routers that contain a vulnerability now being exploited by at least one Mirai variant. Security researchers say the vulnerability appears to relate to a poor implementation of the TR-064 "LAN-Side DSL CPE [Consumer Premises Equipment] Configuration" protocol in its routers.
TalkTalk tells me that it's begun fixing affected routers.
But infected TalkTalk routers are already being used as IoT launch pads for distributed denial-of-service attacks. Researchers at the security firm Incapsula reported in a Dec. 7 blog post that one of its customers - an unnamed bitcoin website - was hit with a DDoS attack on Dec. 5. Incapsula said it traced the attack back to 2,398 Mirai-infected TalkTalk routers located in the United Kingdom.
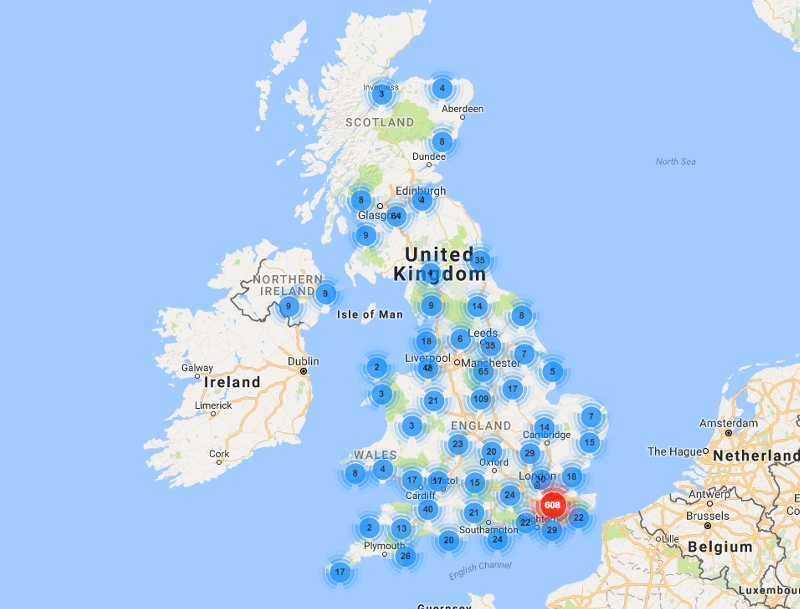 Geolocations of Mirai-infected devices seen in a Dec. 5 DDoS attack against an Incapsula customer.
Geolocations of Mirai-infected devices seen in a Dec. 5 DDoS attack against an Incapsula customer.Another security researcher, speaking on condition of anonymity, told the BBC that he'd exploited the flaw in TalkTalk routers to scrape 57,000 subscribers' devices and retrieve each one's service set identifier (SSID) code and media access control (MAC) address, as well as Wi-Fi password. The researcher said his intention was to highlight that a malicious attacker could have also gained access to the devices, for example, to infect them with Mirai malware, which is designed to target known vulnerabilities - including default access credentials - in dozens of different types of routers and other internet-connected devices, including digital video recorders and IP cameras.
After the BBC was provided with a sample of data pertaining to about 100 of the routers, it shared it with TalkTalk, which confirmed that the information was genuine - while attempting to downplay it posing any threat to customers.
Mirai Variant Strikes Again
Incapsula says the exploited TalkTalk devices appear to have been infected by a Mirai variant that targets the TR-064 protocol, which has also been seen in attacks that exploited D1000 modems built by Taiwanese manufacturer Zyxel that Irish ISP Eir supplied to some of its customers (see Mirai Botnet Knocks Out Deutsche Telekom Routers).
After the Eir exploits began earlier this month, an anonymous researcher - using the handle "kenzo2017" - noted that the TR-064 protocol "is not supposed to be accessed from the WAN side of the modem, but in the D1000 modem, we can send TR-064 commands to port 7547 on the WAN side." As a result, this allows anyone connected to the internet "to 'configure' the modem."
Security researchers say that as of November, more than 5 million devices with an open 7547 port appeared to be connected to the internet.
Kenzo had published a proof-of-concept exploit for Eir routers to the open source vulnerability testing framework Metasploit on Nov. 8, and security researchers said this exploit appeared to have been combined with leaked Mirai source code to produce a new variant.
In the Eir attacks, after this variant infected devices, the malware apparently then closed port 7547, most likely to prevent rival attackers or Mirai malware variants from being able to exploit their devices, multiple security researchers have reported.
Incapsula says that the hacked TalkTalk routers didn't have an open 7547 port. "However, when we fed the same addresses into Shodan" - a search engine for internet-connected device configurations - "we discovered that these ports had been open until a few days ago." Incapsula says that's "the smoking gun" proving that the same Mirai variant that targeted Eir was also used to infect TalkTalk devices.
According to penetration testing firm Pen Test Partners, most routers that use poorly secured TR-064 protocols appear to "have components in them made by a group of companies called Ralkink/Econet/Mediatek," and it's likely that the components all share similar software.
TalkTalk Confirms Attacks
"As is widely known, the Mirai worm is an industry issue impacting many ISPs around the world, and a small number of TalkTalk customers have been affected," a TalkTalk spokeswoman tells me. "We can reassure these customers there is no risk to their personal information as a result of this router issue, and there is no need for them to reset their Wi-Fi password."
Security experts beg to differ on both of the claims.
"I think that the ISP should be replacing all of the affected routers, as it's possible that the hackers could keep control of your router even after you've reset it and applied the fix," Pen Test Partners' Joe Bursell says in a blog post. He says affected users should immediately change their Wi-Fi passwords.
University of Surrey computer science professor Alan Woodward, who also advises the EU law enforcement intelligence agency Europol, tells the BBC: "If TalkTalk has evidence that significant numbers of passwords are out in the wild, then at the very least they should be advising their customers to change their passwords. To say they see no need to do so is, frankly, astonishing."
TalkTalk customer? My advice is to change your wifi password if affected - better safe than sorry https://t.co/UP9mICTN6n
TalkTalk Users Can Demand a New Router
TalkTalk tells me that its website and initial router guide offer instructions on how to change Wi-Fi passwords, and that it's rolling out fixes for hacked and at-risk routers, although it declined to say whether this process was fully automatic, or whether it would require user interaction.
"We have made good progress in repairing affected routers, but any customer who is still having any problems should visit our help site where they can find a guide that will show them how to reset their router," the spokeswoman says. "Alternatively, they can call us, and we can talk them through the repair process or send them a new router."
