Anti-Malware , Network & Perimeter , Risk Management
Zero-Day Flaw Revealed via Equation Group Tool Dump
Cisco has begun releasing software updates for its Adaptive Security Appliance devices to patch a zero-day flaw that was revealed via leaked Equation Group attack tools. Cisco ASA devices provide anti-virus, firewall, intrusion prevention and virtual private network capabilities (see Equation Group Hacking Tool Dump: 5 Lessons).
See Also: How to Mitigate Credential Theft by Securing Active Directory
On Aug. 13, a group calling itself the Shadow Brokers published a 250 MB data dump that contained an assortment of Equation Group tools, including EGREGIOUSBLUNDER, targeting Fortinet-built Fortigate devices; BENIGNCERTAIN, targeting Cisco PIX devices; as well as other tools designed to exploit Juniper and Topsec equipment. The tools, which date from 2013, are widely believed to have been developed by the U.S. National Security Agency for use by its Tailored Access Operations group (see NSA Pwned Cisco VPNs for 11 Years).
So far, only one zero-day vulnerability has been found via the leaked tools, in the attack tool code-named EXTRABACON. "The EXTRABACON exploit targets a buffer overflow vulnerability in the SNMP code of the Cisco ASA, Cisco PIX and Cisco Firewall Services Module," according to Cisco's related security alert. "An attacker could exploit this vulnerability by sending crafted SNMP packets to an affected Cisco product." Successfully exploiting the vulnerability would then give the attacker full control over the system, including the ability to execute arbitrary code.
Cisco warned that all versions of ASA could be exploited.
Hold the EXTRABACON
On Aug. 24, however, Cisco began releasing patches for ASA devices to block the flaw exploited by EXTRABACON. "Cisco has updated the security advisory for the SNMP Remote Code Execution Vulnerability (CVE-2016-6366), which addresses the EXTRABACON exploit," writes Omar Santos, principal engineer in the Cisco Product Security Incident Response Team, in a blog post. "We have started publishing fixes for affected versions, and will continue to publish additional fixes for supported releases as they become available in the coming days."
Cisco says the following devices can likely be exploited via CVE-2016-6366:
Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500-X Series Next-Generation Firewalls Cisco ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers Cisco ASA 1000V Cloud Firewall Cisco Adaptive Security Virtual Appliance (ASAv) Cisco Firepower 4100 Series Cisco Firepower 9300 ASA Security Module Cisco Firepower Threat Defense Software Cisco Firewall Services Module (FWSM) Cisco Industrial Security Appliance 3000 Cisco PIX FirewallsTo patch the vulnerability, Cisco's security advisory says users of ASA 7.x and 8.x should update to 9.1.7(9) or later, and users of 9.x should update to patched versions that it expects to release by Aug. 26.
No Fix for PIX Devices
That PIX devices are vulnerable to CVE-2016-6366 is concerning, because Cisco stopped supporting - and issuing updates - for the devices in 2013. Even so, security researcher Mustafa Al-Bassam last week found that at least 15,000 PIX servers are still in use and thus at risk from the flaws targeted by the Equation Group attack tools.
In its security advisory, Cisco says that it will not be patching PIX devices. "Cisco Firewall Service Modules and Cisco PIX Firewalls have passed the last day of software support milestone as stated in the published end of life documents," it says. "Further investigations into these devices will not be performed, and fixed software will not be made available."
Security Researchers First Detailed Risks
The danger posed by EXTRABACON was first revealed Aug. 16, when the Australia-based security researcher known as XORcat confirmed that EXTRABACON could be used to gain remote access to Cisco devices running firmware version 8.4, up to 8.4(4). "The requirements for the ExtraBacon exploit are that you have SNMP read access to the firewall, as well as access to either telnet or SSH," XORcat wrote. "Once the exploit is successful, the attacker will be able to SSH to or telnet to (depending on what protocol is setup on the [firewall]) without needing to enter credentials," unless an SNMP password was enabled for the device.
On Aug. 17, Cisco confirmed that ASA devices were vulnerable to the attack and released related IPS and Snort signatures to help block any attempts to exploit the flaw while it prepped related patches. It also said that related attacks could be blocked if the devices were set to use an SNMP password. This is known as the "SNMP community string," according to Craig Williams, senior technical leader of Cisco's security intelligence and research group Talos.
Cisco ASA SNMP Remote Code Execution vulnerability is a *new defect* - The SNMP community string needs to be known https://t.co/VepFS4X3RZ
But some security researchers have suggested that obtaining the SNMP password would be a trivial task for a sophisticated attacker.
I mean, that's true in a strictly literal sense, but discovering the required information is TRIVIAL. Sigh.
Researchers initially believed that EXTRABACON only worked against ASA devices running 8.x firmware, up to version 8.4.(4). But Hungary-based security consultancy SilentSignal on Aug. 23 reported that its researchers had successfully adapted EXTRABACON to target up to ASA version 9.2(4), which was released in July 2015.
We successfully ported EXTRABACON to ASA 9.2(4) #ShadowBrokers #Cisco pic.twitter.com/UPG6yq9Km2
The takeaway is that it would have been easy for the anyone - NSA or otherwise - in possession of the 2013-era tool set to update it and exploit the latest generation of ASA devices.
Intelligence Oversight Questions for Congress
One unanswered question - beyond the identity of the Shadow Brokers - is how they obtained the attack tools. On that front, Nicholas Weaver, a senior staff researcher focusing on computer security at the International Computer Science Institute in Berkeley, Calif., says it's time the U.S. Senate and House intelligence oversight committees begin asking NSA officials some pointed questions.
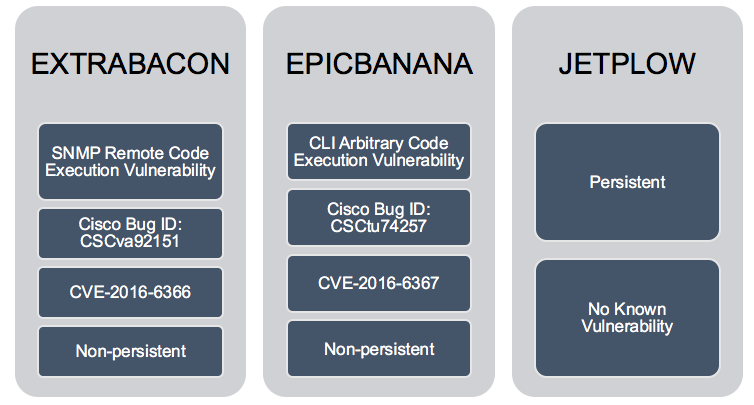 Exploits and related vulnerabilities targeting Cisco ASA, Cisco PIX and Cisco Firewall Services that have been ascribed to the Equation Group and/or NSA.
Exploits and related vulnerabilities targeting Cisco ASA, Cisco PIX and Cisco Firewall Services that have been ascribed to the Equation Group and/or NSA.For starters, when did the NSA know or suspect that one of its firewall attack toolkits had gone missing? "If the NSA knew of the breach of their tools and failed to notify Cisco and Fortinet, this would represent a serious dereliction of the NSA's Information Assurance [Directorate] mission because both of those products are used by the [U.S.] government and on [Department of Defense] systems which IAD is charged with protecting," Weaver writes on the Lawfare blog.
There are three leading theories as to how the tools came to be obtained by the individual or group calling themselves the Shadow Brokers: Hackers infiltrated a top secret system, an insider stole and leaked them, or a member of the NSA's Tailored Access Operations group loaded the tools onto an unclassified server while prepping an attack and accidentally left them there.
Many security experts suspect the third possibility to be most likely, and Weaver says that tools with difficult-to-use interfaces could easily be to blame.
