Anti-Malware , Fraud , Phishing
Russian Hacking Group's Latest Malware? Not So Fancy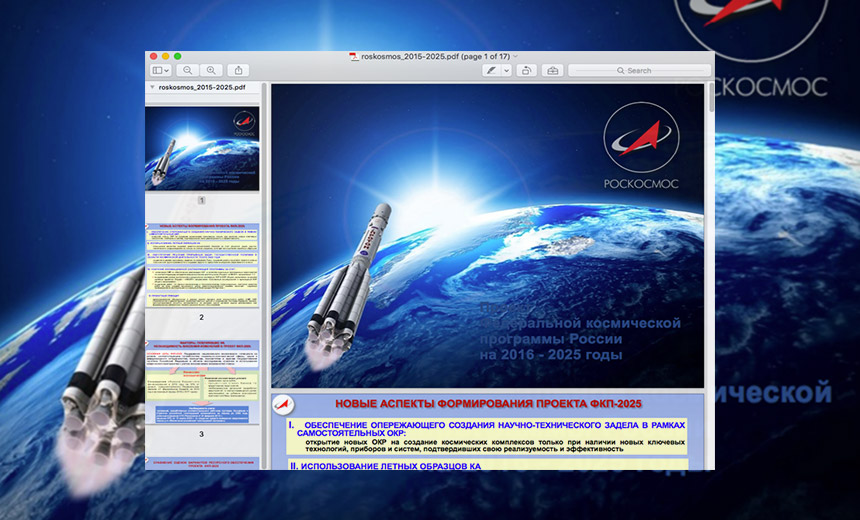 Decoy document delivered by the Sofacy (Fancy Bear) gang. (Source: Palo Alto Networks)
Decoy document delivered by the Sofacy (Fancy Bear) gang. (Source: Palo Alto Networks)A new kind of malicious software for Apple Mac computers is believed to have been developed by the same Russia-linked hacking group that allegedly struck the Democratic National Committee and the World Anti-Doping Agency.
See Also: Eight Capabilities IT Pros Should Look for in a CASB
Palo Alto Networks says the malware, called Komplex, pretends to be a 17-page PDF document describing future projects of the Roscomos State Space Corporation, Russia's space agency. The malware is designed to steal information from a compromised system and send it to a remote server.
Komplex was likely developed by Sofacy, one of several nicknames for the Russian hacking group, Palo Alto says. Other names for the group include Fancy Bear, APT28, Pawn Storm and Sednit.
Several computer security companies have pinned the intrusion into the servers of the Democratic National Committee on Fancy Bear and another group, Cozy Bear. Cybersecurity vendor Crowdstrike believes Fancy Bear is affiliated with the GRU, one of Russia's intelligence agencies (see Report: Russia's 'Best' Hackers Access DNC's Trump Research).
The attack on the DNC resulted in the leak of more than 19,000 internal emails, which caused turmoil in the party after the correspondence showed party officials favored Hillary Clinton for the Democratic presidential nomination. The group is also believed to have hacked WADA, releasing documents that called into question drug exemptions granted to top athletes for the Rio Olympics (see Hackers Dump US Olympic Athletes' Drug-Testing Results).
The U.S. government is investigating whether the Russian government is behind the DNC hack and other suspicious activity, although it has not directly blamed it. But in the first presidential debate on Sept. 26, Democratic nominee Hillary Clinton directly accused Russian President Vladimir Putin of ordering the attacks (see Clinton, Trump Tackle Cybersecurity in Debate).
Not So Fancy
Fancy Bear's most public successes haven't relied on what most computer security experts would characterize as being exceptional hacking. Rather, the group has employed well-known social engineering techniques and tricks, which are often adequate against weak targets.
For example, WADA has said the group gained access to its ADAMS database, which is used for scheduling athletes for drug testing, through compromised login credentials. ADAMS was accessible through the web. It appears Fancy Bear set up domains to mimic WADA's real domain in order to capture usernames and passwords through phishing emails.
Komplex isn't very fancy, either. Getting it installed on machines is predicated on victims being duped by the PDF and ignoring warnings from Apple's operating system that an application will be installed.
Thomas Reed, a Mac expert with the security firm Malwarebytes, writes in a blog post that Komplex is "trivial in execution, trivial to detect and trivial to remove."
It doesn't appear that Komplex was signed with a developer's digital certificate from Apple. Although anyone can obtain those certificates, the inclusion of one makes an application appear more legitimate, at least on surface inspection.
Depending on how it is configured, Apple's Gatekeeper will block applications that are not available via the Mac App Store - which only hosts approved programs - or that do not come from a list of "identified developers" maintained by Apple.
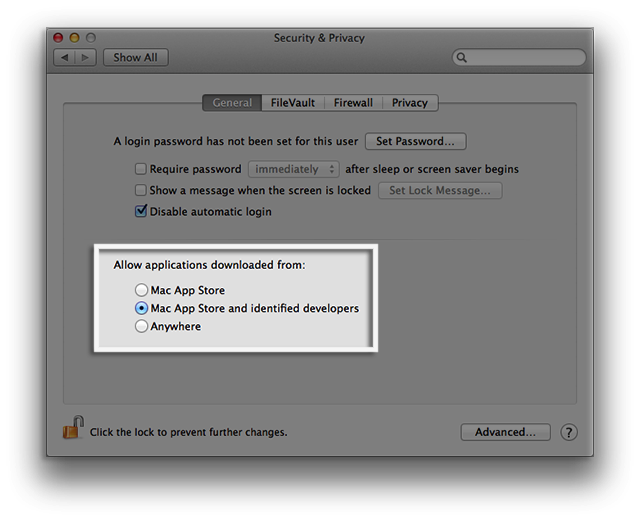 Apple OS X Gatekeeper settings.
Apple OS X Gatekeeper settings.Reed says that regardless of whether Komplex was signed, users would see a warning that the content is actually an application coming from the internet. That should raise a big red flag for users, because Komplex pretends to be a PDF.
"Of course, we know folks will still click right through stuff like that without reading it," Reed says.
Patrick Wardle, director of research with the company Synack, tested Komplex and found it also triggered another warning for users to download Apple's Xcode development suite. He posted a screenshot of the warning on Twitter. Komplex's various binaries appeared to be unsigned "and really not that sophisticated," Wardle says in an email.
looks like the OSX/Komplex malware authors didn't test on a non-developer box? #malwareFail pic.twitter.com/f4docEZvUk
Link to Fancy Bear
Palo Alto Networks found strong links between Komplex and another piece of malware that cybersecurity firm BAE Systems analyzed in June 2015. In particular, static elements for network communications, such as the composition of URLs and HTTP structure data, were the same, as well as the algorithm used to encrypt and decrypt network traffic, according to Palo Alto's blog post.
The malware found by BAE Systems didn't rely on social engineering to get installed. Instead, it used a zero-day vulnerability in MacKeeper, a security application for Mac that many experts advise not installing (see MacKeeper Hid Product Update Error).
"These overlaps suggest that the Trojan delivered by the MacKeeper vulnerability was, in fact, the Komplex Trojan," Palo Alto writes.
According to BAE's analysis from June 2015, real exploit attempts appeared in the wild only a few days after security researcher Braden Thomas developed proof-of-concept code that took advantage of the MacKeeper flaw.
The issue, now patched, caused MacKeeper to execute code contained within a maliciously crafted URL. Hackers often seize upon weaknesses in third-party applications, with Adobe's Flash browser plug-in among the most consistently targeted.
Palo Alto also found strong links between Komplex and a variant of the banking malware Carberp developed by Fancy Bear, even though Carberp is written for Windows.
The Carberp variant had the exact same token value for a command-and-control URL that was encoded into Komplex. Both programs' binaries also had the same file extensions for that URL and in the same order.
"Based on these observations, we believe that the author of Sofacy's Carberp variant used the same code, or at least the same design, to create the Komplex Trojan," Palo Alto writes.
Apple was notified about Komplex, Palo Alto says.

