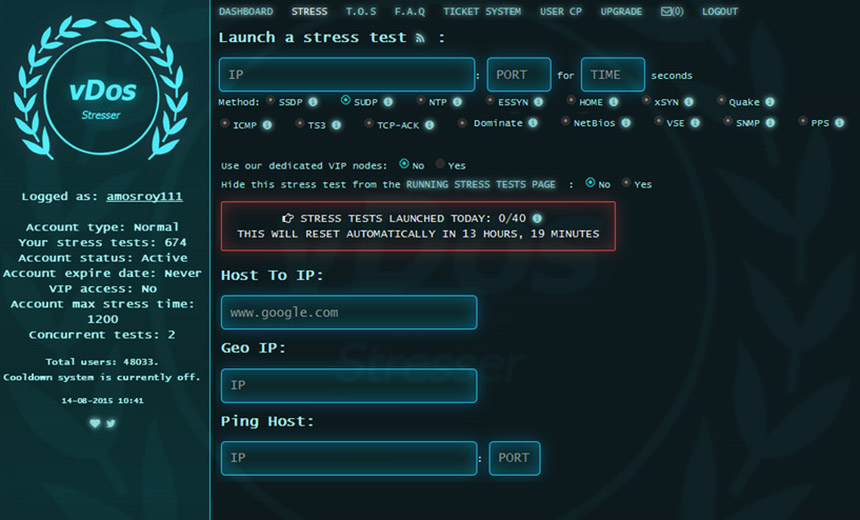
 The vDOS site user interface
The vDOS site user interfaceTwo men have been arrested by Israeli police, at the request of the U.S. Federal Bureau of Investigation, in connection with an investigation into the vDos site, which provided distributed denial-of-service attacks on demand.
See Also: A Smarter Approach to Third-Party Vendor Risk: A Case Study
Itay Huri, a.k.a. "P1st" and "M30w," and Yarden Bidani, a.k.a. "AppleJ4ck," both age 18, were arrested Sept. 8, according to a local press report. Police told Israeli financial website The Marker that the arrests were made at the request of the FBI, and that both men were questioned Sept 9 and released under house arrest for 10 days after they posted the equivalent of about $10,000 in bail. Both men have been prohibited for 30 days from connecting to the internet or using any type of telecommunications device and from leaving the country or communicating with each other, police said. They also are required to report to police for questioning on demand. Both men's passports have also been confiscated.
Police did not specify the charges against the men, The Marker notes. But both were named by security blogger Brian Krebs in a Sept. 8 blog on the vDos service. Based on leaked documents, he estimated that vDos had earned more than $600,000 in profits over the past two years, courtesy of launching 150,000 DDoS disruptions.
The vDos site advertised various plans costing $30 to $200 per month. But the site and service have been offline since Sept. 9.
All of the email domains associated with vDos administrators used a domain that had been registered to someone named Itay Huri, using a phone number tied to Israel, Krebs reported. The service was configured to send requests for tech support via text messages - using an SMS service called Nexmo.com - to six mobile phone numbers, one of which matches with a phone number used by Huri on a domain registration, and another that's tied to an Israeli citizen named Yarden Bidani, according to the blogger. Krebs added that support emails were being routed to the email addresses itay@huri[dot]biz, This email address is being protected from spambots. You need JavaScript enabled to view it. and This email address is being protected from spambots. You need JavaScript enabled to view it., with the latter apparently being used by Bidani.
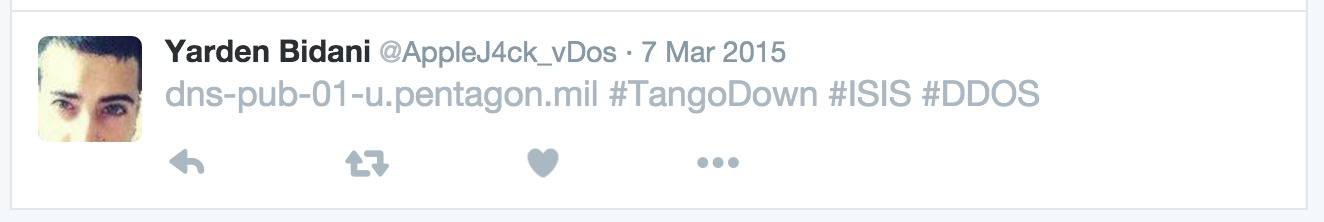
On March 7, 2015, the Twitter account @AppleJ4ck_vDos, which lists "Yarden Bidani" as the account holder's name, and "vdos-s.com" as his site, claimed that parts of the Pentagon website had been disrupted.
Based on the leaked data, other potential victims of vDos included gaming site GoodGame.co.uk, anti-DDoS firm Zare.com and the Model United Nations club for the U.K.'s Imperial College in London, the Register reports.
Customer Secrets Spilled
DDoS defense provider CloudFlare is hosting a text file containing a list of attacks carried out by vDos from April to July, including the vDos username that commissioned the attack, the target IP address, as well as details relating to the attack type, date and time. The information was gleaned after an anonymous security researcher reportedly exploited a vulnerability in the vDos site in July and stole copies of the databases and configuration files underpinning the site. Krebs said he was given a copy of those files and noted that many trouble tickets logged by the site related to users complaining that DDoS attacks that they commissioned against targets in Israel were not happening - suggesting that the site's administrator's prohibited attacks against Israeli targets.
"Chances are that many of vDos's customers may have imagined that their details would have been kept private, and that there would have been little risk of their identities being discovered," says security expert Graham Cluley in a blog post. "That belief was clearly misguided."
Claims of Legitimacy
DDoS-on-demand services are often marketed as being stresser/booter services that can supposedly help administrators test their sites' resilience against DDoS disruption attempts. And vDos appeared to be no different, running a blog post on Aug. 4, for example, titled "5 ways to prevent DDoS attacks."
On June 21, vDos published a tweet marketing its services a preventive tool. "#Booters give your #network the ounce of prevention it needs against #DDoS by simulating Layer 4 and Layer 7 tests," it stated.
Likewise, Huri and Bidan appeared to be positioning themselves as DDoS security experts. In August, they released a technical paper on amplified DDoS attack techniques - how to maximize disruptive power using minimal resources - for an Israeli technology site called Digital Whisper. The paper was bylined with Huri's name as well as a researcher using the email address "This email address is being protected from spambots. You need JavaScript enabled to view it.," which - as noted - has been previously tied to Bidan.
Distributed Cybercrime Economy
Despite any claims to legitimacy, stresser and booter services have long been favored by anyone who holds a grudge - criminals, hacktivists, unscrupulous competitors, rival political parties - as a way to disrupt any individuals or organizations to which they're opposed.
DDoS defense firm Incapsula estimates that DDoS-for-hire services accounted for 93 percent of all DDoS attacks seen between January and March of this year. That was a marked increase from April to June 2015, when Incapsula tied 64 percent of all DDoS attacks to such stresser or booter services.
Using such services enables criminals to obtain DDoS attack capabilities without having to maintain related infrastructure themselves. Indeed, cybercrime gangs such as Armada Collective and DD4BC have used such disruptions, or the threat of such disruptions, to extort victims into giving them bitcoins (see Stresser/Booter Services Fuel DDoS Extortion).
Advertisements for vDos have also often been featured on the Hack Forums site - described as "a wretched hive of scum and villainy" by Robert McArdle, threat research lead for Europe, the Middle East and Africa at security vendor Trend Micro.
McArdle has said that Hack Forums often attracts cybercrime wannabes - a.k.a. script-kiddies - who lack technical knowledge but want to know how to bolster their skills, noting that so often, "today's idiot is tomorrow's supervillain."

