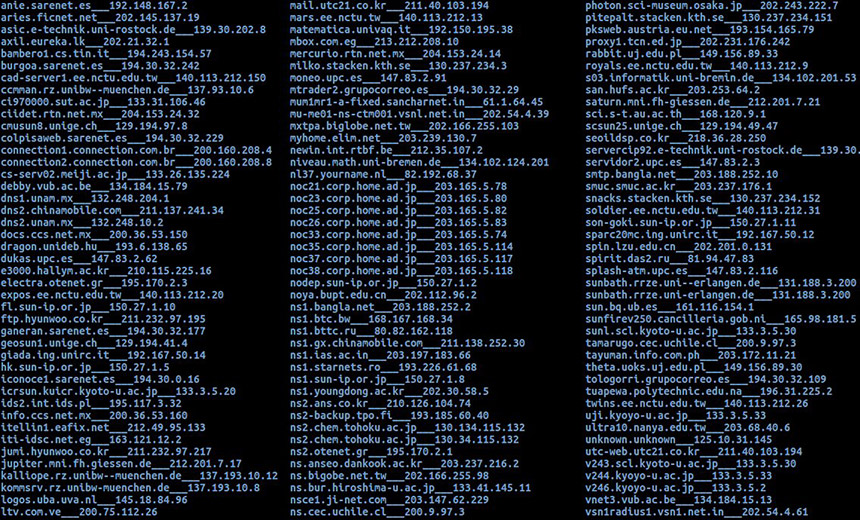
 The latest Shadow Brokers leak lists alleged NSA staging servers.
The latest Shadow Brokers leak lists alleged NSA staging servers.The Shadow Brokers - the group that released what are purported to be hacking tools tied to the U.S. National Security Agency - is back with what it claims to be a list of exploit-staging servers that were hacked by the agency and used to launch online attacks over the course of a decade. The group labels the Oct. 31 data dump as a "special trick or treat for Amerikanskis."
See Also: Main Cyber Attack Destinations in 2016
It's the group's first release of material since Aug. 13, when it dumped exploits and software implants that it said came from the Equation Group, which is the nickname for an advanced hacking group that experts say is likely the NSA's Tailored Access Operations team (see Confirmed: Leaked Equation Group Hacking Tools Are Real).
The leak contains a list of systems in 49 countries, according to an analysis by U.K.-based cybersecurity firm Hacker House. The greatest numbers of compromised servers are located in China, Japan and South Korea.
Security experts say the NSA's TAO launches operations from compromised servers to help mask its activities. Experts have theorized that the Shadow Brokers' first leak came from such a server, and that it either hadn't been scrubbed after an operation or had already been hacked when the agency first began using it.
The latest data dump, which contains 306 domain names and 352 IP addresses, will give affected network operators good reason to conduct further digital forensic investigations.
"These hosts may still contain forensic artifacts of the Equation Group APT group and should be subject to incident response handling procedures," Hacker House writes.
The Shadow Brokers imparted a warning to people doing that kind of analysis, writing that infected computers had rootkits, which is the term for hard-to-detect malware deeply embedded in an operation system. It claimed the rootkits "will self destruct." The group may be referring to capabilities built within a rootkit to erase itself before discovery. The Shadow Brokers cautioned that investigators should create a "cold forensic image" of any computer before subjecting it to analysis, to preserve an undamaged copy of its contents.
Expert: List Looks Legit
Multiple security experts, including Mustafa Al-Bassam, who has been cataloging alleged Equation Group "exploits, implants and tools for hacking firewalls" that have been released by the Shadow Brokers, believes the latest information is tied to NSA operations.
New Shadow Brokers dump contains list of servers compromised by the NSA to use as exploit staging servers. pic.twitter.com/rVNjWCvgoG
— Mustafa Al-Bassam (@musalbas) October 31, 2016The latest Shadow Brokers leak, however, appears to be quite old. The most recent time stamps on some of the systems date from 2010, while some stretch back to 2000. It's unlikely that many of the systems are still in the same state, Vitali Kremez, a senior cybercrime intelligence analyst with security intelligence firm Flashpoint, tells Information Security Media Group.
In an analysis of the latest dump, meanwhile, Kremez highlights the apparent age of the information contained in the leak. "This is almost like looking at dinosaur remnants," he writes.
More Setbacks for the NSA?
If the list is genuine, it would mark another setback for the NSA, which has been grappling with damaging leaks. The arrest of Booze Allen Hamilton contractor Hal Martin in August marked the second time since Edward Snowden that the NSA has faced a large leak of internal data (see NSA Contractor's Alleged Theft 'Breathtaking').
Martin, 51, is alleged to have hoarded terabytes of highly classified material in his car and house. Martin allegedly also possessed some of the same information released by the Shadow Brokers, The New York Times has reported. But it is unclear if he is connected with the group and if the overlap in material is merely coincidence.
The Shadow Brokers has continued to issue new blog posts following Martin's arrest. In announcing the latest leak, the group attempts to address tensions between the United States and Russia over the latter's alleged interference with the presidential election, but in a seemingly nonsensical manner. The poor grammar and syntax of the Shadow Brokers' writings, however, have led some security experts to speculate that the writer might be a native English speaker attempting to appear to be a non-native speaker by making intentional errors.
"Why is DirtyGrandpa threating CIA cyberwar with Russia?" the group writes. It's not clear what the group means with the name DirtyGrandpa.
The United States believes Russia is responsible for hacking the Democratic National Committee and compromising email accounts of high-profile officials. Despite compelling circumstantial evidence, Russia has dismissed the accusations.
New Hacking Toolkits?
The Shadow Brokers dumps have provided security experts with a trove of information into what appear to be at least one intelligence agency's historical attack capabilities, with earlier dumps revealing previously unknown zero-day flaws in Cisco networking gear, which the manufacturer has been patching.
The latest data dump, meanwhile, includes information related to how those tools were likely used. The data includes domain names, IP addresses, the operating systems of the compromised systems as well as related time stamps, which range from 2000 to 2010. Most of the systems were running a version of Sun's Solaris, which is a Unix-based operating system. Other details include names - Dewdrop, Incision, Jackladder, Orangutan, Patchicillin, Stoicsurgeon, Reticulum - that appear to refer to hacking toolkits.
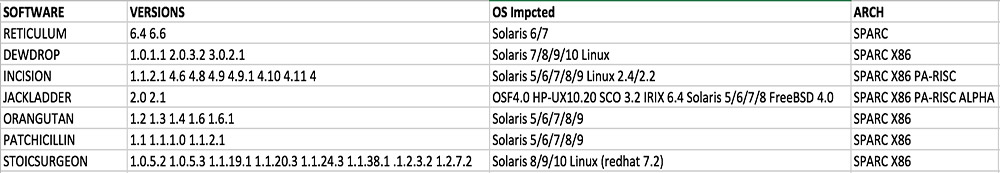 The latest Shadow Brokers data dump includes a list of apparent attack tools. Source: Hacker House.
The latest Shadow Brokers data dump includes a list of apparent attack tools. Source: Hacker House.The Shadow Brokers' post described one such likely tool, called Pinchimpair, as a redirector tool. Hacker House writes that the redirector might be a backdoor or implant that is used for tunneling attacks.
The toolkits appear to not have been publicly named before, and thus it is possible the related attacks may still be ongoing, Hacker House writes. Notably, the company conducted a search using Shodan, which indexes internet-connected devices, and found that some of the domains listed in the leak are still active as well as running the same software listed in the leak. As a result, they would likely still be vulnerable to whatever methods were first used to allegedly compromise them.
"It is strongly advised that if you or your organization are amongst the impacted parties, you perform incident response on identified hosts, and contact security professionals to help determine [the] impact on your network," Hacker House writes. "You may have inadvertently been hosting Equation Group APT cyber attacks from your environment."
While the Shadow Brokers leaks have been continuing, some of what the group has promised to do has yet to materialize. After the group's first release, in particular, it promised to auction the password for a second, encrypted file. The Shadow Brokers said they would release the password to the archive if they received 1 million bitcoins. But that improbable sum that has yet to materialize.

