Anti-Malware , Network & Perimeter , Ransomware
It's Not WannaCry, But at Least 100,000 Systems at Risk from Wormable Flaw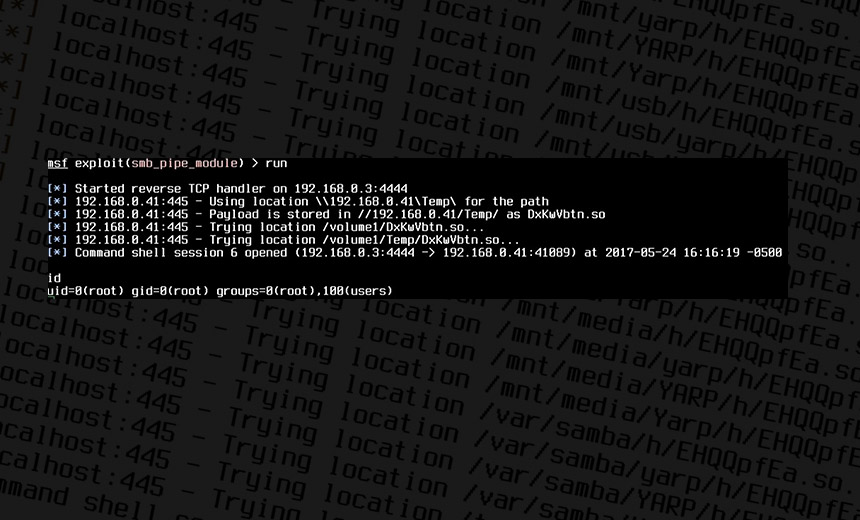 Proof-of-concept exploits of the Samba flaw in Ubuntu and Synology NAS devices. (Source: HD Moore)
Proof-of-concept exploits of the Samba flaw in Ubuntu and Synology NAS devices. (Source: HD Moore)In the wake of WannaCry, there's a critical, newly announced flaw in a protocol based on the Windows server message block - SMB - that security experts are warning could also be exploited via mass attacks, and potentially by a worm designed to exploit the bug.
See Also: Balancing Fraud Detection & the Consumer Banking Experience
The flaw, designated CVE-2017-7494, exists in Samba, which provides Windows-based file and print services for Unix and Linux systems. By successfully exploiting the flaw, an attacker could execute arbitrary code on a device with root-level access permissions.
"All versions of Samba from 3.5.0 onwards are vulnerable to a remote code execution vulnerability, allowing a malicious client to upload a shared library to a writable share, and then cause the server to load and execute it," according to a security alert published Wednesday by the Samba open source project.
Samba has released patches for versions 4.4 and newer that fix that flaw. "Samba vendors and administrators running affected versions are advised to upgrade or apply the patch as soon as possible," its alert says.
For unsupported but still vulnerable systems - 3.5.x to 4.4.x - or any supported versions of Samba that cannot be upgraded for whatever reason, the Samba team has detailed a workaround that involves adding the "nt pipe support = no" parameter to Samba's SMB configuration file and then rebooting the smbd daemon. "Note this can disable some expected functionality for Windows clients," Samba's alert says.
Security experts say the flaw should be patched as quickly as possible. "A remote attacker could exploit this vulnerability to take control of an affected system," the U.S. Computer Emergency Response Team, US-CERT, says in a security alert. "US-CERT encourages users and administrators to review Samba's security announcement and apply the necessary updates, or refer to their Linux or Unix-based OS vendors for appropriate patches.
Thankfully, no related attacks have yet emerged. "The internet is not on fire yet, but there's a lot of potential for it to get pretty nasty," Jen Ellis, a vice president at Rapid7, says in a security alert. "If there is a vulnerable version of Samba running on a device, and a malicious actor has access to upload files to that machine, exploitation is trivial."
Samba use is widespread. "Many home and corporate network storage systems run Samba and it is frequently installed by default on many Linux systems, making it possible that some users are running Samba without realizing it. Given how easy it is to enable Samba on Linux endpoints, even devices requiring it to be manually enabled will not necessarily be in the clear," Ellis says.
Easy to Exploit
Just one line of code can be used to exploit the Samba flaw, according to HD Moore, vice president of research and development at Atredis Partners.
Re: Samba bug, the metasploit one-liner to trigger is just: simple.create_pipe("/path/to/target.so")
Moore, the developer of the Metasploit open source penetration-testing software suite, says a working exploit for the flaw is under development. He expects it to be added to the Metasploit Framework sometime Thursday.
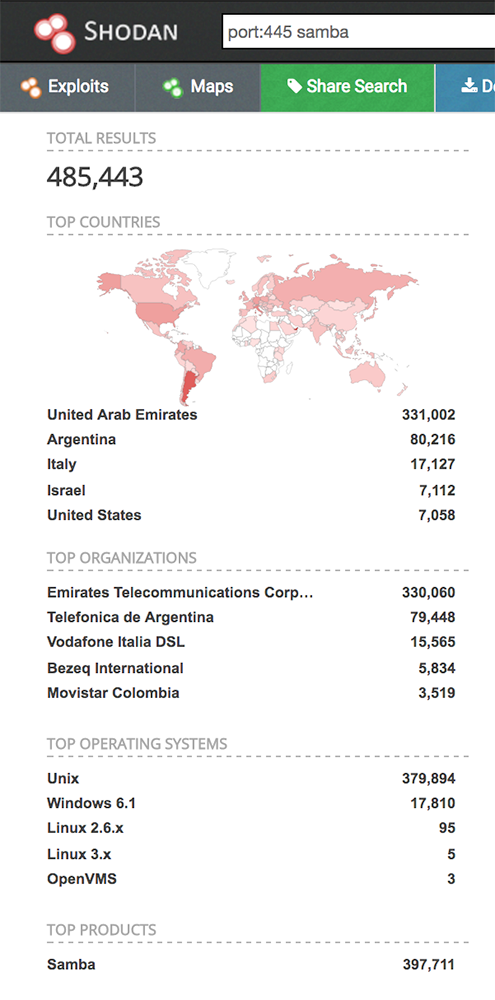 Shodan search results for internet-connected devices on which Samba is accessible via port 445.
Shodan search results for internet-connected devices on which Samba is accessible via port 445.Already, Moore notes, working proof-of-concept exploits have been demonstrated against the Ubuntu operating system as well as Synology network-attached storage devices.
Rebekah Brown of Rapid7 tells Reuters that the firm was able to create proof-of-concept malware to exploit the flaw in just 15 minutes. "This one seems to be very, very easy to exploit," she says.
As of Thursday, there were more than 485,000 internet-connected systems running Samba via port 445, according to a search conducted using internet-connected device search engine Shodan.
Scans run by Rapid7's in-house internet scanning project, dubbed Project Sonar, have found that more than 104,000 of these internet-connected endpoints running a vulnerable version of Samba. "Of those, almost 90 percent (92,570) are running versions for which there is currently no direct patch available," Ellis says.
Enterprise Risks
Enterprise environments are at particular risk due to Samba-using devices. "Samba makes it possible for Unix and Linux systems to share files the same way Windows does. While the WannaCry ransomworm impacted Windows systems and was easily identifiable, with clear remediation steps, the Samba vulnerability will impact Linux and Unix systems and could present significant technical obstacles to obtaining or deploying appropriate remediations," Ellis says.
No Samba patches may be forthcoming for older devices that include the functionality, or for which users cannot patch the device's firmware or operating system. As a result, these devices could be exploited to give attackers access to enterprise networks. In such cases - if workarounds can't be applied - security experts say that the devices must be considered no longer securable and decommissioned.
Serious, But No WannaCry
Researchers have been making comparisons between the Samba flaw and the SMB flaw, MS17-010, patched by Microsoft in all supported operating systems in March. After the WannaCry worm unfolded May 12, Microsoft also issued emergency patches for three unsupported operating systems: Windows XP, Server 2003 and 8.
The fast spread of the WannaCry ransomware was thanks to it having been designed with the worm-like ability to exploit the SMB-targeting EternalBlue exploit revealed in the April "Equation Group" attack-tool dump made by the Shadow Brokers. But the worm also looked for another Equation Group tool - a backdoor called DoublePulsar, designed to give the Equation Group stealthy, ongoing and remote access to the system. If either tool was present on an endpoint, the worm attempted to exploit it and infect the system with ransomware.
So far, however, no one has fielded a worm that targets the new Samba flaw to infect devices with malware. But there is a risk that such attacks could appear, Rapid7's Ellis says. "Organizations should be monitoring all internal and external network traffic for increases in connections or connection attempts to Windows file sharing protocols," she says.
Also, ensure all Samba-using systems, including storage appliances, remain fully backed up. "Many network-attached storage [NAS] environments are used as network backup systems," Ellis says. "A direct attack or worm would render those backups almost useless, so if patching cannot be done immediately, we recommend creating an offline copy of critical data as soon as possible."

