Application Security , DevSecOps , Next-Generation Technologies & Secure Development
Experts Offer Insights on Addressing the Challenges(gsuparna) • August 9, 2018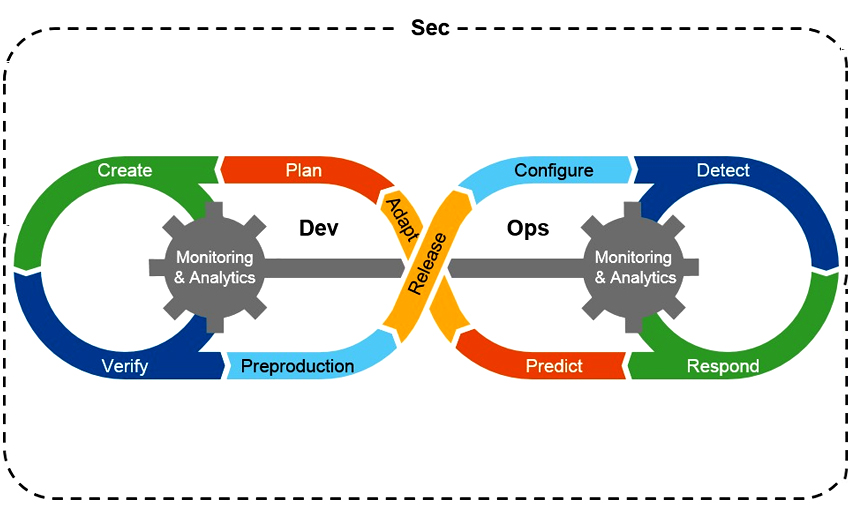
Although there's widespread agreement that addressing security early in the software development cycle is an essential component to any breach prevention strategy, implementing DevSecOps can prove challenging.
See Also: Matching Application Security to Business Needs
DevSecOps, which melds security into the DevOps function, requires collaboration among the development, security and operations groups, fully involving each in all aspects of the project, says Satyavathi Divadari, vice president of information security risk management, at Wells Fargo, India.
"The development team must make an effort to build secure software," says U.S.-based Sameer Shelke, co-founder and CTO at Aujas, a global information risk management solution provider. "I also feel they have to have a notion of a security champion. Not everybody in the development team will have security knowledge. So there has to be that one person who has the security know-how and works with other developers in the team to take ownership of security." (See: Leveraging a Next-Generation SOC to Enhance Threat Detection)
The Challenges
Aditya Khullar, technical cybersecurity, at Paytm, India's largest mobile wallet, says implementing a DevSecOps approach can prove to be quite challenging.
"Unfortunately, some organizations still believe in the notion that incorporating security earlier in and throughout the process of a development cycle will delay quick rollout of innovative new applications," Khullar says. "But when an organization speeds up development by skipping steps meant to identify flaws in untested code, it exposes itself in ways that would have been unthinkable under traditional development models."
Nearly 60 percent of data breaches worldwide in the past two years were related to exploiting a known software vulnerability that was not yet patched, Divadari says. Most notably, the massive Equifax breach involved such an exploit.
The DevSecOps model can help to avoid releasing software with vulnerabilities that pave the way for breaches.
"The DevSecOps model identifies the security vulnerabilities in the initial phases of the development cycle - planning, design and coding," Divadari explains.
Evolution of DevSecOps
DevOps, a software engineering culture and practice that aims at unifying software development and software operation, is becoming more common. But too often, security is an afterthought, says Sajan Paul, director, systems engineering, India and SAARC at Juniper Networks.
"Businesses now have a continuous development environment. Ecommerce websites see high traffic every day. In such an environment, it's not practical to have security outside the software system," Paul says. "If a CISO comes in later, he will implement SIEM along with SOC to keep a check on the red flags. However, this model is not scalable beyond a point and fails to address the requirements of new age digital companies."
The below graph shows the security testing challenges faced by firms.
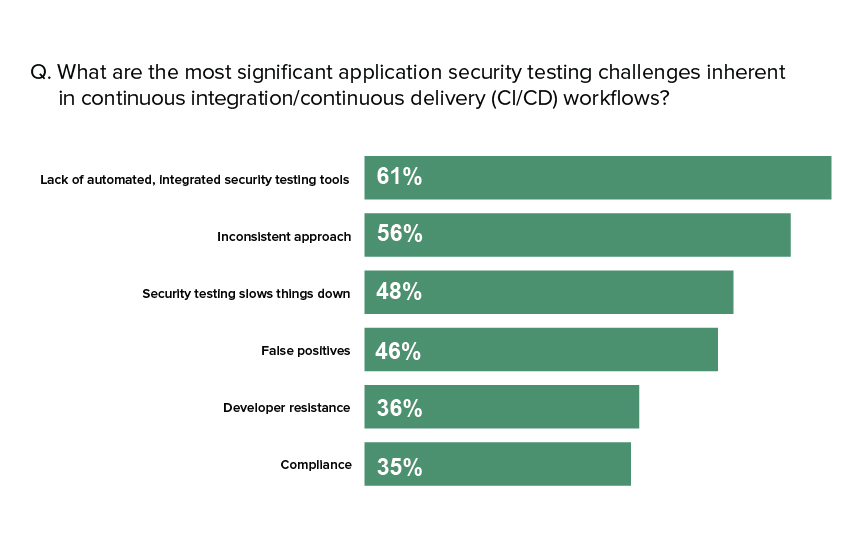 Source: Synopsys
Source: SynopsysSecurity teams must determine if existing security tools can be integrated into a DevSecOps environment, identify alternative tools where needed and pinpoint procedures or controls that have to be updated or adapted, security experts advise.
A DevSecOps model requires standardized security practices, stresses Siddharth Shankar Agarwal, vice president of engineering at Zapr, India's largest media-based audience platform. "This will help in following the basic security practices irrespective of the software used," he says. "Both security and development teams must agree on libraries [to be used for the] development of code and security audits. The focus must be on automating security code review."
Khullar says that his firm made the decision to shift from DevOps to DevSecOps because of the speed with which it has to deliver services to customers.
"For organizations like Paytm, security outside of DevOps does not work. It limits the speed at which we want to reach out to our customers," he says. "Earlier, the security team got involved when a product was complete. Since security could not be compromised, we often had to wait a long time to market a product as we wanted to make sure it met our security standards."
As organizations move to adopt DevSecOps, Khullar suggests that they take the following steps:
Adapt the security testing tools and processes to the developers, not the other way around; Focus on identifying and removing zero-day/critical vulnerabilities; Train all developers on the basics of secure coding.Not Always the Right Choice
Despite the benefits, using DevSecOps isn't always appropriate.
"Software with very high quality requirements, such as critical infrastructure controllers that may need formally or semi-formally validated security, will likely not work in DevSecOps," says Gerald Beuchelt, CISO at LogMeIn, a provider of software as a service and cloud-based remote connectivity services for collaboration. "Similarly, environments that have generally a low or zero tolerance for failure, such as financial transaction systems, national defense systems, electric power grid controllers, or life-support technology would in many cases not be ideal candidates for an unmodified DevSecOps approach."
Agarwal also notes that in certain sectors, such as financial services, healthcare and manufacturing, government regulations may restrict what can be done in some parts of the production environment.
"DevSecOps covers only one aspect of security, and not all security can be run in this manner," adds U.K.-based Steve Marshall, CISO and head of cyber consulting at Bytes Software Services .
The security element in DevSecOps is technical security and not corporate or information security, he notes. As a result, the corporate and information security teams must continue to act independently within an organization, he says.
"Therefore, it is advisable to embed only the technical security teams within the DevOps teams," Marshall says. "It is at this point one needs to consider if this change of function and role may require a completely different skill set than what traditional technical security teams have."
There are other challenges as well. "Developers think they can rely on automated security tooling to solve their issues, but they can't," says Pieter Danhieux, CEO, Secure Code Warrior, a cybersecurity company. "A second problem is most modern development makes use of a myriad of coding stacks, some of them quite new. Usually, these new frameworks are not supported yet by some of the security tooling (such as AST). This is another reason why it is vital that the developers themselves have secure coding skills, because the tools will never cover everything from a coding language perspective."

