Cybercrime , Cybercrime as-a-service , Finance & Banking
Street Value of 70,000 Cards on Joker's Stash Is $3.5 Million, Group-IB Says(euroinfosec) • February 22, 2019 Stolen Pakistani bank cards are being offered for sale on the Joker's Stash carder forum. (Source: Group-IB)
Stolen Pakistani bank cards are being offered for sale on the Joker's Stash carder forum. (Source: Group-IB)A notorious carder site is featuring a fresh batch of Pakistani banks' payment card data with an estimated street value of $3.5 million.
Moscow-based threat intelligence firm Group-IB says that in late January, it spotted the sale of nearly 70,000 cards on the cybercrime marketplace called Joker's Stash, which specializes in selling batches of stolen payment card data. This marks the second time in the past six months that a big batch of Pakistani bank card data has appeared for sale (see: Pakistan: Banks Weren't Hacked, But Card Details Leaked).
Group-IB says 96 percent of the new 69,189 bank cards being offered for sale are advertised as being issued by Pakistan's Meezan Bank, based in Karachi, the country's largest city.
Meezan Bank bills itself as being Pakistan's first and largest Islamic bank, offering a range of Shariah-compliant products and services. It has 600 branches in 159 cities. The bank didn't immediately respond to a request for comment on the card data that's appeared on Joker's Stash.
 The headquarters of Pakistan's Meezan Bank in Karachi (Photo: Meezan Bank)
The headquarters of Pakistan's Meezan Bank in Karachi (Photo: Meezan Bank)Group-IB said it saw two batches of Pakistani cards get posted to Joker's stash in the form of dumps advertised under the following names:
Pakistan-D+P-01: First offered for sale on Jan. 24, this included about 1,500 cards, most of which were issued by Meezan Bank. Pakistan-D+P-02: First offered for sale on Jan. 30, this dump contains 67,654 Pakistani bank cards. "The sellers marked the set as 'high valid' and unlike the first set, advertised the database on all major underground forums, such as Omerta, Crdclub [and] Enclave," Group-IB says. It adds that the card numbers were initially sold with no refunds possible, before the listing was updated to say buyers have three hours after purchase to receive a full refund for any card numbers that don't work.The cards are being sold for a premium - $50 per card, above the $10 to $40 that is more often charged for bank cards on darknet forums, Group-IB says. "Pakistani banks' cards are rarely sold on underground card shops," the firm says. "This, and the fact that all the cards came on sale with PIN codes, explains the high price."
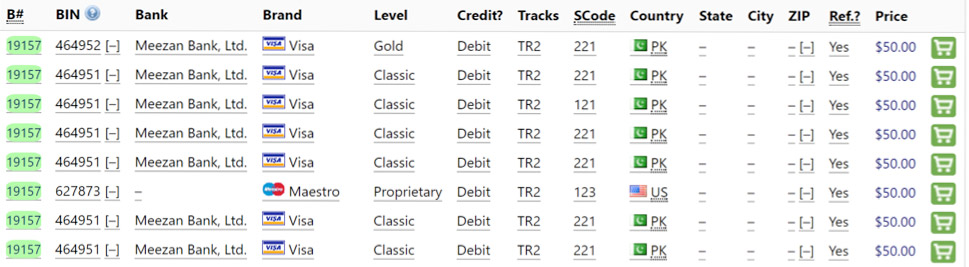 Sample of data being advertised on Joker's Stash (Source: Group-IB)
Sample of data being advertised on Joker's Stash (Source: Group-IB)The appearance of so much Pakistani bank card data in one place is unusual, says Dmitry Shestakov, head of Group-IB's cybercrime research unit. "The scale, volume, frequency and connection to one institution contributes to the theory that the leak might be involved in a larger incident, potentially an advanced actor gaining access to card systems within Pakistan," he says.
Attack of the Cloned Cards
Fraudsters often use stolen payment card data to create cloned cards. Third parties, acting as money mules, may be hired to use those cards to fraudulently purchase and resell goods. Cards might also be used to withdraw cash from ATMs (see: Taiwan Sentences Money Mules in ATM Attacks).
Group-IB says some scammers also create dummy companies, use cloned cards to buy nonexistent goods from the companies, then withdraw the money in cash from the dummy companies' bank accounts.
Fraudsters have tended to favor payment cards issued in the U.S. or Canada, and to a lesser extent Western Europe. But security experts say fraud controls in these regions have been continuing to improve, enabling card issuers to more rapidly block fraud.
Banks in emerging markets, such as Pakistan, however, "frequently do not have adequate anti-fraud control," allowing attackers to perpetrate a number of different types of fraud, Group-IB says.
Late-2018 Dumps
The latest dumps of Pakistani payment card data to Joker's Stash follow earlier dumps, Group-IB says:
Oct. 26, 2018: 10,467 payment cards issued by smaller Pakistani banks posted for sale. Oct. 31, 2018: 11,795 cards issued by banks in Pakistan and others in the region posted. Early November 2018: 177,878 payment cards from a number of international banks offered for sale. Cards from major Pakistani banks, including Habib Bank, MCB Bank Limited and Allied Bank Limited, were part of the dump.The State Bank of Pakistan responded to those data dumps via a statement it issued on Nov. 6, 2018, saying that none of the country's banks had been hacked. But in response to the payment card data breach, SBP says some banks did restrict the use of payment cards internationally, requiring approval from customers prior to any international transaction being approved.
Frequent Targets: POS Systems, ATMs
The appearance of fresh card data on Joker's Stash often sends banks and card issuers scrambling in an attempt to determine the origin of the data. Such dumps have sometimes offered the first clues that an organization was hacked, potentially by attackers having infected its point-of-sale systems with RAM-scraping malware, then exfiltrated massive quantities of payment card data (see: Fast-Food Chain Sonic Investigates Potential Card Breach).
Another potential target: Bank ATMs into which gangs have installed physical skimmers, aka "cutlets," that record magnetic card data and record video, allowing attackers to "read" victims' PIN codes (see: Cybercrime Gangs Advertise Fresh Jobs, Hacking Services).
Magecart at Work
Joker's Stash has continued to serve as the carder marketplace of choice for many cybercriminals, including some of the groups known as Magecart.
"Magecart is an umbrella term given to at least seven cybercriminal groups that are placing digital credit card skimmers on compromised e-commerce sites at an unprecedented rate and with frightening success," according to security firms RiskIQ and Flashpoint.
The firms say one of the more advanced Magecart gangs, known as Group 6, tends to only sell stolen card data on Joker's Stash. Group 6 has been tied to the breach of e-commerce site Newegg, as well as U.K. flagship carrier British Airways, which is owned by International Airlines Group.
 Payment card data stolen from retailer Newegg by Magecart Group 6 appeared for sale on the notorious carder site Joker's Stash about a week after the attack was remediated.
Payment card data stolen from retailer Newegg by Magecart Group 6 appeared for sale on the notorious carder site Joker's Stash about a week after the attack was remediated.'Formjacking' on the Increase
Security firm Symantec, in its Internet Security Threat Report, says hackers are increasingly using "formjacking" attacks that inject JavaScript into sites - aka digital skimming - to "steal credit card details and other information from payment forms on the checkout web pages of e-commerce sites."
The security firm estimates that 4,800 new websites fall victim to formjacking attacks each month.
"Requiring only a few simple lines of code loaded onto a website, formjacking represents a significant threat to online retailers or anyone who collects personally identifiable information from their customers via their website," Symantec's report says.
Group-IB says that on average, a total of 1.8 million new payment cards get offered for sale on carder sites each month.

