Cyberwarfare / Nation-state attacks , Fraud Management & Cybercrime , Governance
Cybereason Says Theft of Subscribers' Call Metadata Could Be Linked to Chinese APT Group(euroinfosec) • June 25, 2019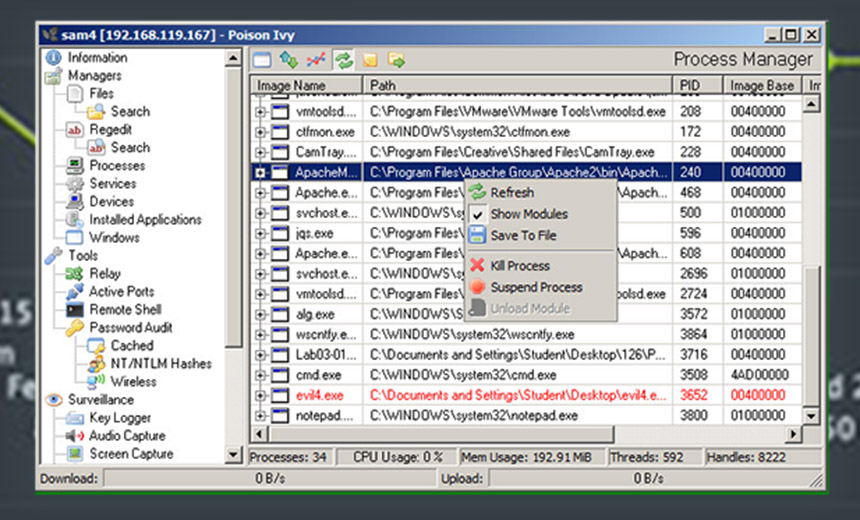 Attackers have been using the Poison Ivy remote-access tool to help maintain persistent access to hacked networks, Cybereason says.
Attackers have been using the Poison Ivy remote-access tool to help maintain persistent access to hacked networks, Cybereason says.Attackers have been surreptitiously hacking into global telecommunications providers' networks to quietly track subscribers as part of an apparent ongoing espionage operation. according to the security firm Cybereason.
See Also: 10 Incredible Ways You Can Be Hacked Through Email & How To Stop The Bad Guys
Cybereason says it discovered the campaign earlier this year after assisting one of the targeted telecommunications firms and tracing back suspicious network traffic. But it says many more telecommunications carriers have been targeted globally, although none of the hacked providers appear to be U.S.-based.
Based on the tools and tactics used in the attack campaign, which Cybereason has dubbed Operation Soft Cell, the security firm says it's found evidence that this operation has been running since at least 2017, although it may tie to attacks that began in 2012.
Cybereason, which is headed by former Israeli counterintelligence officials, says it's not disclosing targets or victims of the campaign because the attacks remain ongoing. Information Security Media Group wasn't able to independently confirm Cybereason's assertions in the report.
Active Directory Hacked
The attackers' goal appears to have been to gain access to a small group of subscribers' call detail records, Cybereason says. Each CDR contains metadata that includes the type of call or communication - such as a text message - as well as the time, duration and source and destination telephone numbers.
To gain CDR access, Cybereason says the attackers often used phishing attacks to gain access to the targeted telecommunications firms' infrastructures, in many cases eventually gaining access to databases, billing servers as well as servers running Active Directory services. With that level of access, attackers were reportedly able to issue themselves administrator-level credentials and also create VPN accounts to make it easier to connect later to the hacked network and disguise their activities.
The attacks appear to have been used to target about 20 individuals that have ties to China and who are based across Africa, Asia, Europe, and the Middle East, Cybereason officials told the Wall Street Journal.
Cybereason CEO Lior Div told the Journal that "we never heard of this kind of mass-scale espionage ability to track any person across different countries." And he said he briefed more than two dozen global telecommunications firms about the hacking campaign over the weekend.
Goal: Gathering Metadata
Cybereason says attackers wouldn't have been able to track targets in real time, although they would have amassed historical geolocation data that could have been used to track their movements.
Gathering telephone metadata has obvious espionage value, because it would have allowed attackers to map targets and their social networks - who they spoke with, for how long, and when - as well as where people traveled.
"Having this information becomes particularly valuable when nation-state threat actors are targeting foreign intelligence agents, politicians, opposition candidates in an election, or even law enforcement," Cybereason researchers Mor Levi, Assaf Dahan and Amit Serper write in a blog post.
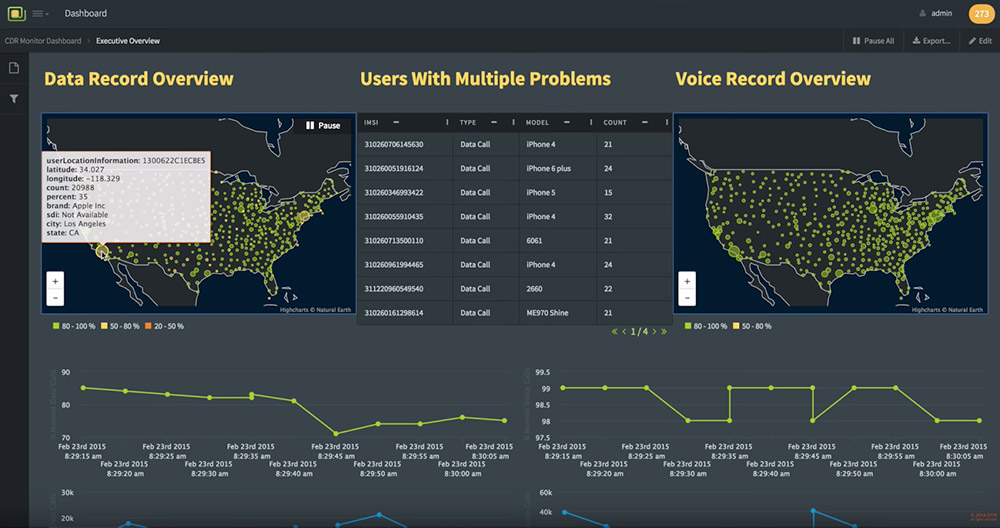 Here's an example of the type of data that would have been available to attackers. Note, however, that researchers have not stated that any U.S. telecommunications firms were targeted. (Source: Cybereason)
Here's an example of the type of data that would have been available to attackers. Note, however, that researchers have not stated that any U.S. telecommunications firms were targeted. (Source: Cybereason)Indeed, the potential value of metadata was highlighted by its being secretly collected in bulk by the U.S. National Security Agency, as former contractor Edward Snowden revealed. In 2015, however, President Barack Obama signed the USA Freedom Act, which ended the NSA's no-longer-clandestine program to collect Americans' bulk telephone metadata (see: Report: NSA Expanded Internet Spying).
Apparent Nexus With China
The researchers say the Soft Cell campaign has the hallmarks of being a Chinese nation-state operation.
"Having found multiple similarities to previous attacks, it is our estimation that the threat actor behind these attacks is likely linked to APT10, or at the very least, to a threat actor that shares tools, techniques, motive and infrastructural preferences with those of APT10," the Cybereason researchers say. "While we cannot completely rule out a 'copy-cat' scenario, where another threat actor might masquerade as APT10 to thwart attribution efforts, we find this option to be less likely in light of our analysis of the data."
Security researchers also refer to APT10, which is believed to be a Chinese advanced persistent threat group, as "CVNX," "MenuPass," "Potassium," "Red Apollo 1" and "Stone Panda."
Last December, the U.S. Department of Justice charged two alleged APT10 hackers with attempting to break into more than 45 U.S. technology companies and U.S. government agencies as well as several managed security service providers as part of what have been dubbed the Operation Cloud Hopper attacks (see: FBI's Wray on China's Counterintelligence Capabilities).
Soft Cell Tools and Tactics
The Soft Cell attackers used a variety of tool and tactics that cross over with the Cloud Hopper attacks, the researchers say. Those include implementing a modified version of the credential-stealing web shell known as China Chopper, which can also be used to remotely control servers, as well as deploying the widely used Poison Ivy remote-access tool.
Attackers, they say, also used a modified version of the nbtscan - aka the NetBIOS nameserverscanner - tool to enumerate local NetBIOS name servers, as well as dumping credentials from compromised machines by using Mimikatz.
Many attack groups commonly use such admin-level tools both for their power as well as to help avoid detection (see: Hackers Wield Commoditized Tools to Pop West African Banks).
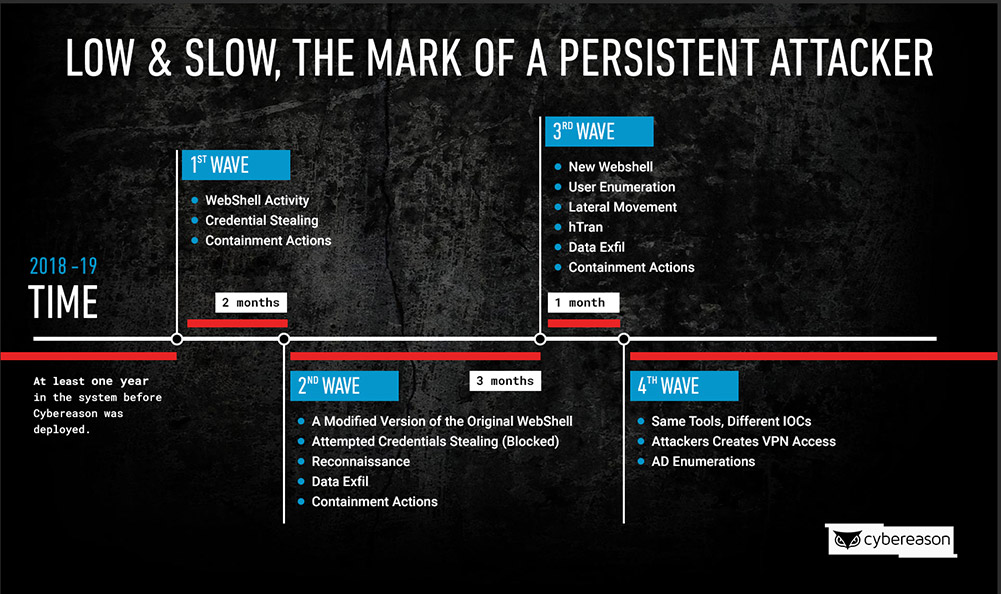
In Soft Cell's case, Cybereason says the attackers were extremely patient and persistent. "The attackers worked in waves - abandoning one thread of attack when it was detected and stopped, only to return months later with new tools and techniques," the researchers write.
Satellite Operators Hacked Too
If Chinese attackers are behind Soft Cell, these would not be the first attacks against telecommunications providers that allegedly trace to that nation.
Last June, the security firm Symantec said it had uncovered a cyber espionage campaign focused on infiltrating three telecommunications operators in Southeast Asia as well as a defense contractor and a satellite communications operator (see: Hackers Hit Satellite Operators and Telecoms, Symantec Says).
Symantec said the attacks, which it ascribed to a group code-named Thrip, ran from 2013 to 2016 before reappearing in 2018. The most recent attacks appeared to trace to three computers in China. But Symantec said that finding, together with an analysis of the tools used by hackers, remained insufficient to definitively attribute the attacks to anyone (see: Stop the Presses: Don't Rush Tribune Ransomware Attribution).

